What Is a Vulnerability Scanner for Websites?
A website vulnerability scanner is a specialized tool designed to inspect and analyze a website for possible security gaps or weaknesses. These tools crawl through a site, much like a search engine robot, checking its structure, code, server settings, and more. The goal is to identify any potential vulnerabilities that could be exploited by hackers or malicious software.
These scanners can also play a crucial role in verifying the effectiveness of your security measures, ensuring that your defenses are up to par. They can identify gaps in protection, outdated software, and even the use of default or easily guessable passwords.
Vulnerability scanners must be used regularly to keep up with the ever-evolving landscape of web threats. New vulnerabilities are discovered every day, and hackers are always on the lookout for new ways to exploit them. Regular scanning ensures that you stay one step ahead of these cyber threats.
This is part of a series of articles about vulnerability assessment.
What Are the Common Web Vulnerabilities Detected by Vulnerability Scanners?
Vulnerability scanners can detect a wide range of vulnerabilities, from simple misconfigurations to complex code-based vulnerabilities. Let’s explore some of the most common types of vulnerabilities.
SQL Injection
SQL injection, often abbreviated as SQLi, is a type of vulnerability that occurs when an attacker can manipulate the SQL statements that a web application makes to its database. By inserting malicious SQL code into user inputs, an attacker could potentially access, modify, or even delete data from the database. This could lead to unauthorized access to sensitive information, data corruption, or even the complete takeover of the website.
Vulnerability scanners can detect potential SQL injection vulnerabilities by testing various inputs and observing the website’s response. If the website behaves differently or returns an error message that reveals information about the database structure, the scanner would flag this as a possible SQL injection vulnerability.
Cross-Site Scripting (XSS)
Cross-site scripting, or XSS, is another common web vulnerability. This occurs when an attacker can inject malicious scripts into web pages viewed by other users. Such scripts can steal sensitive information like login credentials or personal details, manipulate website content, or even redirect users to malicious websites.
Vulnerability scanners can identify potential XSS vulnerabilities by attempting to inject a benign script into user inputs. If the script is executed when the page is viewed, the scanner will flag this as a possible XSS vulnerability.
Cross-Site Request Forgery (CSRF)
Cross-site request forgery, or CSRF, is a type of attack that tricks the victim into submitting a malicious request. This is done by forcing the user’s browser to send a forged HTTP request, including the user’s session cookie, to a website where they’re authenticated. This could lead to unauthorized actions being performed on the victim’s behalf.
Vulnerability scanners can detect CSRF vulnerabilities by looking for areas of the website that lack anti-CSRF tokens or other protective measures. If such areas are found, the scanner will flag them as potential CSRF vulnerabilities.
Security Misconfiguration
Security misconfiguration is a common vulnerability that occurs when a website or web application is incorrectly set up, leaving it exposed to potential attacks. This could involve anything from leaving default account settings unchanged to having unnecessary services running on the server.
Vulnerability scanners can identify security misconfigurations by comparing the website’s current settings against a database of known secure configurations. If any discrepancies are found, the scanner will highlight these as potential security misconfigurations.
Insecure Direct Object References (IDOR)
Insecure direct object references (IDOR) are a common vulnerability where a web application exposes a reference to an internal implementation object. This can be as simple as a reference to a file or directory or as complex as a reference to a database record or key.
A vulnerability scanner can detect IDOR by testing various object references within your web application. If the scanner can manipulate these references to access unauthorized data, it indicates an IDOR vulnerability.
XML External Entities (XXE)
XML external entities (XXE) occur when an application processes XML data that includes a reference to an external entity. This can lead to disclosure of internal files, denial of service, or even remote code execution.
A vulnerability scanner can detect XXE vulnerabilities by sending various XML inputs to your application. If the application responds with data from an unexpected source, it indicates an XXE vulnerability.
Exposed PII
Personally identifiable information (PII) refers to any data that can identify an individual. This can include names, addresses, social security numbers, and more. If your website inadvertently exposes PII, it could lead to serious privacy breaches.
Vulnerability scanners can detect exposed PII by crawling your website and examining the data it sends and receives. If the scanner finds PII in places it shouldn’t be, like URLs or error messages, it indicates a PII exposure vulnerability.
Remote Code Injection
Remote code injection is a serious vulnerability where an attacker can inject and execute their own code on your website. This could allow them to steal sensitive data, disrupt your service, or even take control of your site.
Vulnerability scanners can detect remote code injection by sending various inputs to your website. If these inputs cause unexpected behavior or output, it can indicate a remote code injection vulnerability.
Exposed Remote Desktop Service
Exposed remote desktop services, such as RDP (Remote Desktop Protocol) or VNC (Virtual Network Computing), can provide a direct entry point for attackers to your system. If these services are inadequately secured, they can become a significant vulnerability.
Vulnerability scanners can detect exposed remote desktop services by scanning your network for open ports associated with these services. If it finds any, it can test them for vulnerabilities like weak passwords or unpatched software.

Operationalizing CTEM Through External Exposure Management
CTEM breaks when it turns into vulnerability chasing. Too many issues, weak proof, and constant escalation…
This whitepaper offers a practical starting point for operationalizing CTEM, covering what to measure, where to start, and what “good” looks like across the core steps.

How Does a Web Vulnerability Scanner Work?
A web vulnerability scanner operates by sending various inputs to your website and analyzing the responses. These inputs are designed to trigger potential vulnerabilities, and the responses can indicate whether a vulnerability is present.
The scanner begins with a process called ‘crawling’. This involves navigating through your website, following links, and identifying all possible input points. This could include form fields, URL parameters, cookies, and more.
Once the scanner has identified these input points, it begins testing them for vulnerabilities. It does this by sending a range of specially crafted inputs, known as payloads, to each input point. These payloads are designed to trigger potential vulnerabilities.
The scanner then analyzes the responses to these payloads. If a response indicates a potential vulnerability, the scanner records it for further investigation.
Related content: Read our guide to vulnerability detection tools.
Tips from the Expert

Rob Gurzeev, CEO and Co-Founder of CyCognito, has led the development of offensive security solutions for both the private sector and intelligence agencies.
In my experience, here are tips that can help you better utilize and enhance your use of website vulnerability scanners:
- Leverage differential scanning: Implement differential scanning to compare the current scan with the previous one. This can highlight new vulnerabilities introduced by recent code changes or configuration updates, helping to catch issues before they go live.
- Utilize custom payloads for complex applications: Modify the scanner’s payloads to suit the specific needs of your web application, especially if it’s custom-built or uses unique frameworks. This ensures that the scanner tests the application effectively, avoiding false negatives.
- Correlate with threat intelligence feeds: Use threat intelligence feeds to update your scanner with the latest vulnerability signatures and emerging threats. This ensures that your scans are always relevant to the current threat landscape.
- Monitor scanner performance: Track the performance of your vulnerability scanner over time, including the rate of false positives and scan duration. Optimize settings and payloads to improve accuracy and efficiency, reducing the time between scans and the need for manual verification.
- Use multi-scanner approaches: Different scanners often excel at detecting different types of vulnerabilities. Combine the use of multiple vulnerability scanners to improve overall coverage and reduce the chances of missing critical security issues.
Notable Vulnerability Scanners for Your Website
1. OWASP ZAP
Source: zaproxy.org
The Zed Attack Proxy (ZAP), originally created by OWASP, is an open-source vulnerability scanner specifically designed for web applications. It functions as an intercepting proxy, allowing users to inspect and modify the traffic between their browser and the web server.
ZAP offers automated scanners as well as a set of tools for manual security testing. A key feature is its spider, which automatically crawls new applications to identify URLs, which are then targeted for vulnerabilities.
ZAP also provides a passive scanning feature that identifies security issues in the background while browsing, making it an effective tool for ongoing security assessments. Its active scanner probes the identified URLs to find potential vulnerabilities. Being community-driven, it is regularly updated with the latest threat intelligence.
2. Nessus
Source: Nessus
Nessus, developed by Tenable Network Security, is a commercial vulnerability management tool. It scans for a wide range of vulnerabilities, including software flaws, missing patches, malware, and misconfigurations across various systems.
Nessus is known for its high-speed discovery, configuration auditing, asset profiling, sensitive data discovery, and vulnerability analysis of security patches. Its plugin architecture ensures that it remains up-to-date with the latest vulnerabilities.
A key feature of Nessus is its ability to save policies and configurations, allowing for consistent scans across different environments. It also provides detailed remediation steps for each identified vulnerability, which can assist IT professionals in addressing security gaps.
3. Burp Suite Community Edition
Source: Burp Suite
Burp Suite Community Edition, is a free platform for web application security testing. The community version is limited than the professional edition—it lacks the automated scanner, but is still useful for manual testing. It includes an intercepting proxy, which allows detailed inspection and modification of the requests and responses between the client and the server.
Another significant feature is the Burp Repeater, which lets security testers manually modify and resend individual requests and analyze the responses. Its Intruder tool is useful for performing customized attacks to identify and exploit vulnerabilities like SQL injection and cross-site scripting (XSS).
4. Acunetix
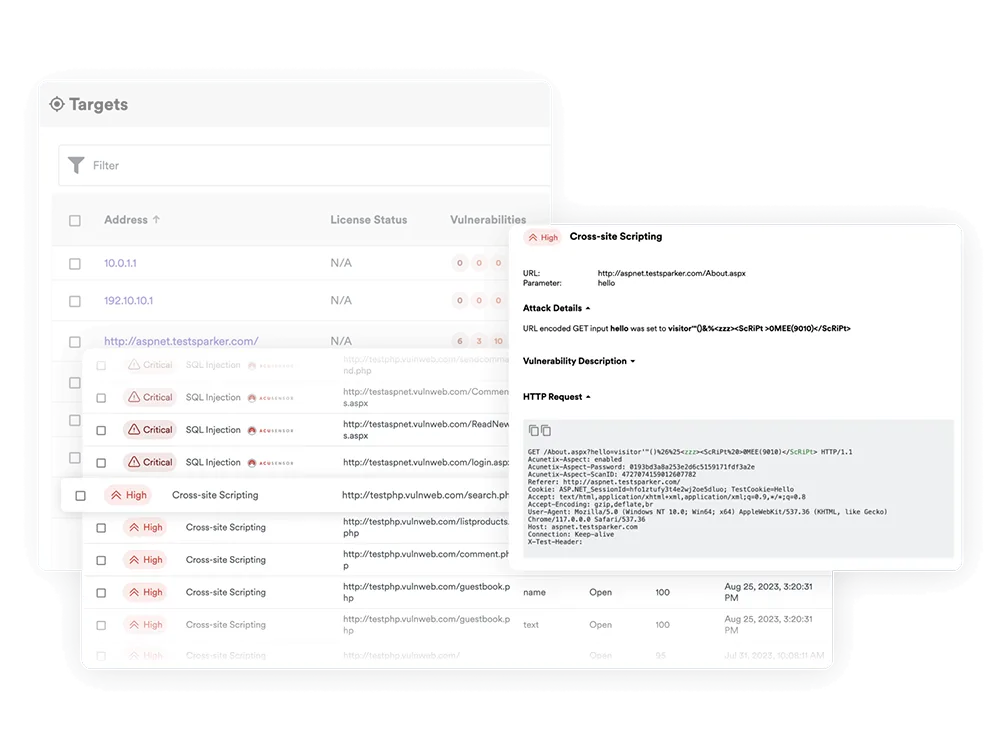
Source: Acunetix
Acunetix is a fully automated web vulnerability scanner that is designed to scan complex, authenticated, HTML5, and JavaScript-heavy websites. It can detect over 4500 types of web application vulnerabilities, including all variants of SQL Injection and XSS. Its DeepScan technology allows for thorough inspection of web applications by emulating a user’s interaction with JavaScript-heavy websites.
Acunetix also comes with a built-in vulnerability management feature to analyze and prioritize risks. It offers the AcuSensor technology that can be deployed inside web applications to increase the detection of underlying vulnerabilities. In addition, it can integrate with popular issue trackers and security systems, providing a seamless workflow for developers and security professionals.
5. Wazuh
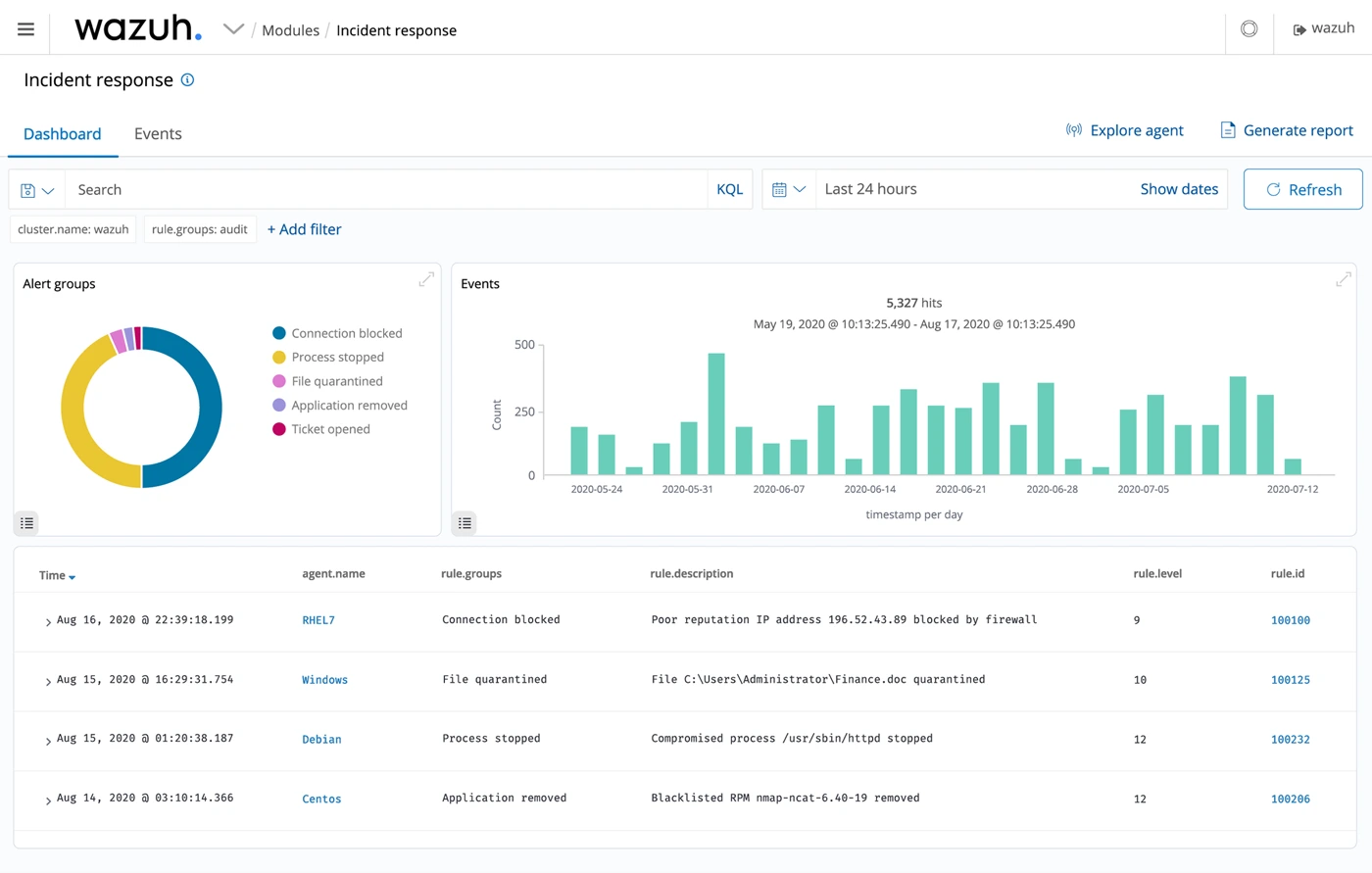
Source: Wazuh
Wazuh is an open-source security monitoring solution that extends its functionality beyond simple vulnerability scanning. It integrates various modules for intrusion detection, log analysis, and file integrity monitoring. Wazuh’s vulnerability detection module continuously scans monitored systems for software vulnerabilities, using databases like the National Vulnerability Database (NVD) and the CVE Compatibility Program.
Wazuh correlates detected vulnerabilities with impacted systems, providing alerts and detailed reports. This approach allows for real-time analysis and rapid response to any security threats. Its integration capabilities with other tools like ELK (Elasticsearch, Logstash, and Kibana) stack enhance its functionality in security data analysis and visualization.
6. Greenbone OpenVAS
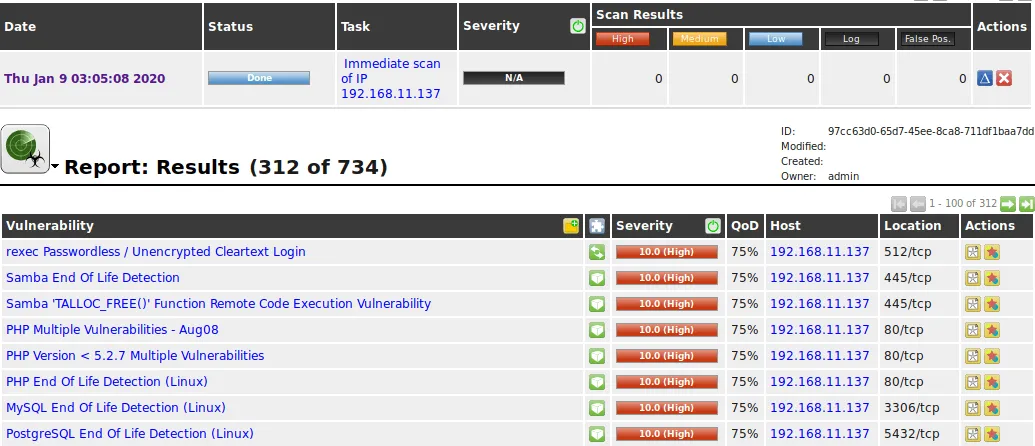
Source: Greenbone OpenVAS
Greenbone OpenVAS (Open Vulnerability Assessment Scanner) is part of the Greenbone Open Source Edition, a suite of tools designed for vulnerability management. OpenVAS is a full-featured vulnerability scanner with a large and continuously updated database of network vulnerability tests (NVTs). It is capable of scanning networks to detect vulnerabilities in servers and network devices.
The tool performs both unauthenticated and authenticated testing. It also includes capabilities for configuration and compliance checking. As an open-source tool, it benefits from community contributions, ensuring it remains relevant and up-to-date with the latest security threats.
7. Nikto2
Nikto2 is an open-source web server scanner that can test web servers for over 6700 potentially dangerous files and programs, check for outdated versions of over 1250 servers, and identify version-specific issues on over 270 servers. It is designed to detect potentially harmful files and programs on a web server, offering a straightforward approach to web server testing.
Nikto2 can scan for server and software misconfigurations, default files and programs, insecure files, and CGI scripts. Its plugin-based architecture allows users to extend its capabilities. Although it is not a stealthy tool and is meant for quick scans, its thoroughness makes it an appropriate choice for routine checks and early detection of common web server vulnerabilities.
8. CloudSploit
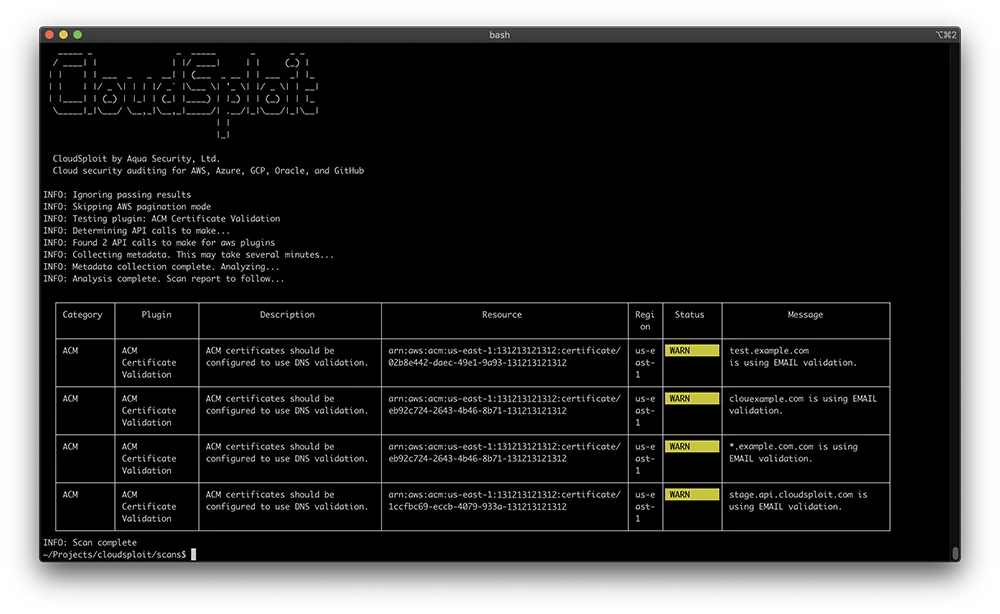
Source: CloudSploit
CloudSploit, also known as Aqua CSPM (Cloud Security Posture Management), is a security and compliance scanning tool specifically designed for cloud environments, including AWS, Azure, and GCP. It automatically assesses cloud accounts for security risks and compliance violations. The tool provides continuous security monitoring for cloud configurations and can identify and report potential exposures, insecure configurations, and non-compliant deployments.
CloudSploit’s scans are non-intrusive, ensuring there is no disruption to cloud services while assessing for vulnerabilities. It provides detailed reports that highlight security risks along with recommendations for remediation.
Vulnerability Management with CyCognito
The CyCognito platform addresses today’s vulnerability management requirements by taking an automated multi-faceted approach to identifying and remediating critical issues based on their business impact rather than focusing on the generic severity of the threat alone. To do this, you need a platform that continuously monitors the attack surface for changes and provides intelligent prioritization that incorporates the organization’s context.
The CyCognito platform uniquely delivers:
- A dynamic asset inventory with classification of the entire external attack surface, including exposed on-premise and cloud-hosted assets like web applications, IP addresses, domains, and certificates, eliminating the need to rely on outdated or incomplete information from collaboration tools, spreadsheets, or emails. This approach significantly reduces the burden of tedious, error-prone, and costly processes.
- Active security testing permits your organization to automatically increase the number and frequency of security assessments without increasing your security team’s workload.
- A broad regimen of IP and web application tests, including dynamic application security testing (DAST), CyCognito identifies exploitable application code, system misconfigurations, exposed data, sensitive files/folders, default credential use, certificate validity issues, common vulnerabilities, PII and exposures (CVEs), and more.
- Prioritization of critical issues, guiding security teams to focus on the most urgent threats. Our unique risk-based prioritization analysis goes beyond the common vulnerability scoring system (CVSS), and incorporates factors like asset discoverability, asset attractiveness, exploitability, business impact, and remediation complexity. Integrated tactical threat intelligence identifies the handful of attack vectors that pose the greatest risk.
- Streamlines communications between remediation teams by providing comprehensive, verifiable evidence for each exploited asset. This evidence includes detailed risk assessments, asset ownership information, and actionable remediation guidance. The platform seamlessly integrates with SIEM, SOAR, and ticketing system tools like Jira, ServiceNow, and Splunk to facilitate information sharing and collaboration.
Learn more about CyCognito for vulnerability management.














