Network and Information Security Directive v2 (NIS2)
In January of 2023, the European Union adopted a new version of the Network and Information Security Directive. NIS2 goal is to establish a higher level of cybersecurity and resilience for EU organizations as compared to the original NIS1 implementation in July 2016.
NIS2 must be implemented into law by the seventeen member EU states by October 17, 2024. Member EU states must identify entities within each scope by April 17, 2025.
NIS2 changes include:
- Initial incident reporting accelerated to within 24 hours and full reporting within 72 hours. The final report must be within 1 month of the incident's end.
- Increase focus on continuous monitoring and improvement of cybersecurity operational practices.
- Scope increased to eighteen industries (also called sectors), expanded from the original seven sectors.
- The new sectors are broken into two entities: essential (e.g. transportation, banking and financial markets) and important (e.g., digital providers, food production and manufacturing)
- Three tiers of industries - large organizations (>=250 employees and >€50M revenue), medium organizations (50-249 employees and >€10M revenue) and small/micro organizations. Each have different requirements.
- Top management is held accountable for non-compliance.
NIS2 lacks technical control specificity, common for any congressional statues in the United States like Sarbanes-Oxley, HIPAA and Dodd Frank, or any parliamentary acts in the EU including GDPR. To proactively meet NIS2 requirements, organizations are following guidance from established international frameworks such as ISO27001, ISO27002, CIS, and NIST 800-53.
Additional NIS2 details can be found in multiple locations, including a NIS2 quick guide published by the National Cyber Security Centre.
How CyCognito Helps
The CyCognito platform automatically identifies violations for major security and compliance frameworks such as NIST, CIS and PCI-DSS. Continuous monitoring and testing addresses the new rapid response timelines and more. Automatic organizational reconnaissance, asset discovery and risk profiling provide the continuous visibility required for EU organizations to meet NIS2 requirements.
International Organization for Standardization ISO/IEC 27000 Series
One of the most widely known security standards, ISO/IEC 27000 series is a mature international framework focused on information security. Developed by the International Organization for Standardization (ISO), it is the cybersecurity equivalent of the ISO 9000 quality standards for manufacturers and operational excellence. ISO 27001 is comprehensive and broad and can be used across a wide range of types and sizes of businesses. ISO 27002 is a subset of ISO 27001, providing best-practice guidance on selecting and implementing the security controls listed in ISO 27001.
How CyCognito Helps
The CyCognito platform contributes to addressing ISO 27001:2013 sections “6.1.2 Information Security Risk Assessment,” “9.1 Monitoring, Measurement, Analysis and Evaluation” and “10.1 Nonconformity and Corrective Action.” Of the 14 Categories in the Annex A controls, the CyCognito platform contributes significantly to three; A.8 Asset Management, A.12 Operations Security, and A.13 Communications Security.
Center for Internet Security (CIS) Critical Security Controls (CSC)
The CIS guidelines consist of 20 key actions, called critical security controls (CSC), that organizations should implement to block or mitigate known attacks. The controls are designed so that primarily automated methods can be used to implement, enforce and monitor them. These controls give pragmatic, actionable recommendations to reduce cyber security risk.
How CyCognito Helps
The CyCognito platform maps to 14 CIS controls. CyCognito provides extensive coverage around the inventory of assets, vulnerability and penetration testing, and security of ports and services.
NIST Cybersecurity Framework (CSF)
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is voluntary guidance based on existing standards, guidelines, and practices for organizations to better manage and reduce cybersecurity risk. In addition to helping organizations manage and reduce risks, it was designed to foster risk and cybersecurity management communications among both internal and external organizational stakeholders.
How CyCognito Helps
The CyCognito platform helps organizations follow this standard by mapping closely to the Identify and Protect functions and contributing to Detect, Respond and Recover functions.
NIST Risk Management Framework (SP 800-53)
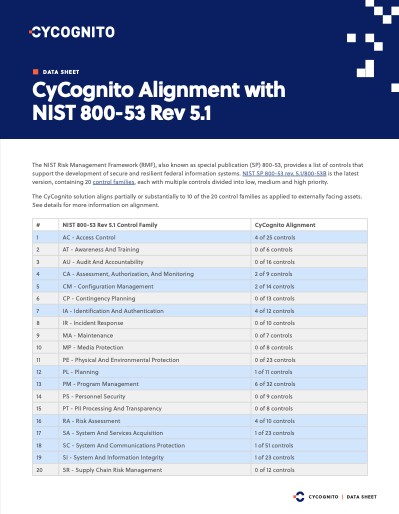
The NIST Risk Management Framework (RMF), also known as special publication (SP) 800-53, provides a list of controls that support the development of secure and resilient federal information systems. NIST SP 800-53 rev. 5.1/800-53B is the latest version, containing 20 control families, each with multiple controls divided into low, medium and high priority.
How CyCognito Helps
The CyCognito platform aligns partially or substantially with 10 of the 20 control families as applied to externally facing assets.
To learn more about how CyCognito aligns with NIST 800-53, download the datasheet:
NIST Guidelines for Protecting Sensitive Information (SP 800-171)
NIST provides guidelines regarding the protection of controlled unclassified information (CUI), which includes such sensitive data as health information, critical energy infrastructure information and intellectual property, in NIST 800-171. Revision 2 is the most current version.
How CyCognito Helps
The CyCognito platform provides guidance on assets with violations to NIST 800-171, helping organizations understand issues and remediate them promptly.
GDPR and Other Data Privacy Regulations
Europe’s General Data Protection Regulation (GDPR) affects all organizations doing business with European natural citizens and is arguably the most stringent data privacy regulation in the world.
The CyCognito platform helps organizations maintain GDPR compliance and other data privacy regulations with continuous risk assessments that identify where sensitive data, including PII, is exposed. The platform’s automatic risk prioritization and remediation guidance make it efficient to build compliance adherence into security operations workflows.
How CyCognito Helps:
The CyCognito platform helps your organization comply with other data privacy regulations around the globe that include protections for the way that PII is obtained, processed and stored. These include:
- California Consumer Privacy Act (CCPA)
- Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA)
- Germany’s Bundesdatenschutzgesetz (BDSG)
- South Africa’s Protection of Personal Information (POPI) Act