What is Attack Surface Protection?
518 views
Eliminate cybersecurity risks before attackers can exploit them.
Digital transformation is changing the scope of your attack surface. Advanced attackers are constantly looking for a way in. Organizations need to go beyond legacy attack surface management approaches to eliminate risks before an attacker can exploit them.
The CyCognito platform does far more than just discover and inventory your organization's entire internet-exposed attack surface. It also tests and prioritizes what needs to be fixed first, automatically validating remediation and delivering true attack surface protection.
Manage and Protect Your Entire Attack Surface
Core Capabilities of CyCognito Attack Surface Protection
Graphs Business & Asset Relationships
Finds all of your exposed assets and tells you which business unit or team owns them.
Determines Business Context
Evaluates risk by determining the business purpose and data residing in each asset.
Tests Security
at Scale
Automatically detects and validates all potential attack vectors across your entire external IT ecosystem.
Prioritizes
Risk
Focuses operations teams on fixing the most impactful risks first.
Accelerates Remediation
Decreases remediation time by sharing relevant guidance so you can take immediate action.
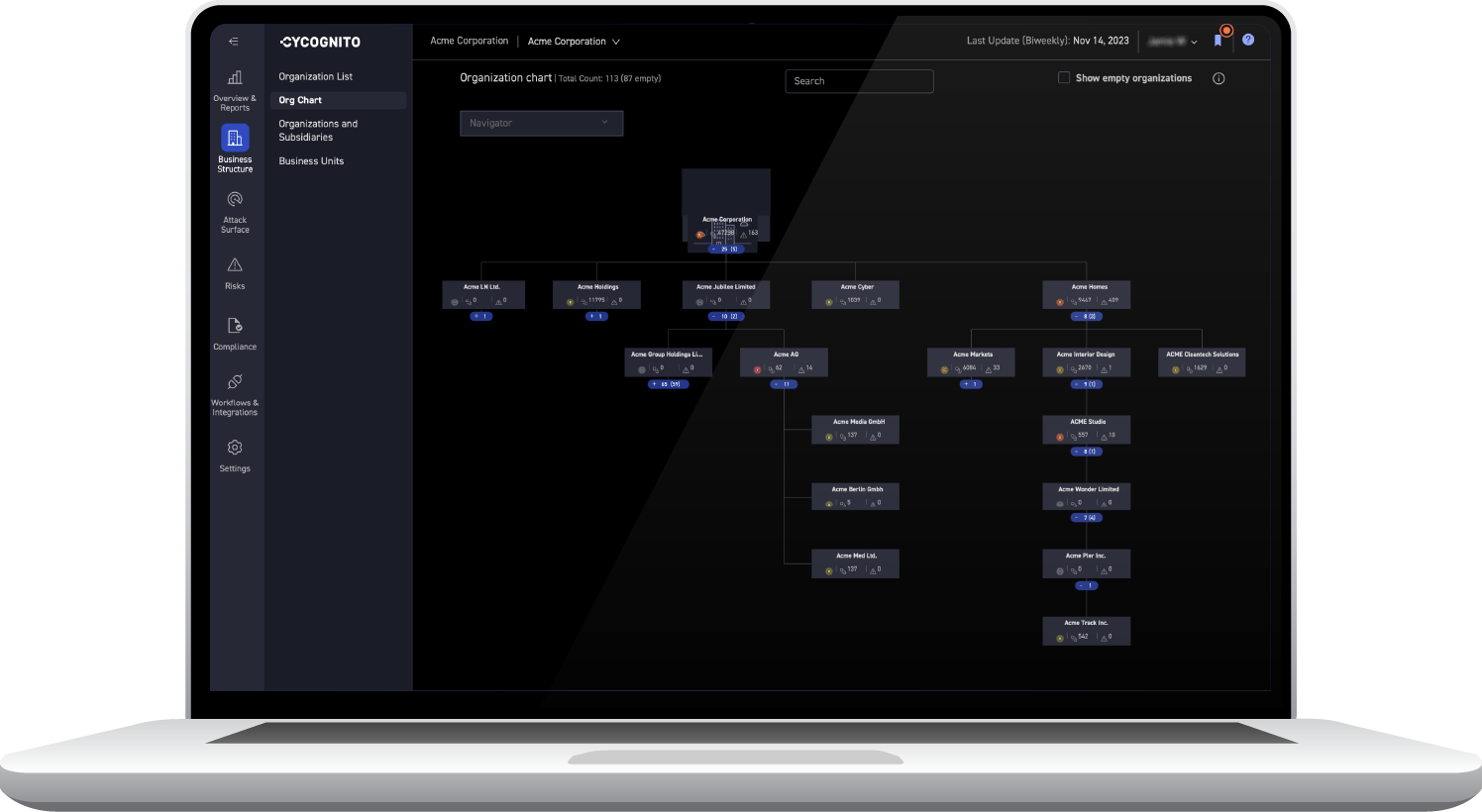
Effortless Discovery & Asset Attribution
Understand asset relationships and owners
Our platform uses natural language processing and advanced algorithms to analyze open source intelligence, identifying assets in your digital attack surface for complete visibility and control. Eighty-four percent of assets are attributed automatically with zero input, configuration, or training.
Advanced Attack Vector Detection
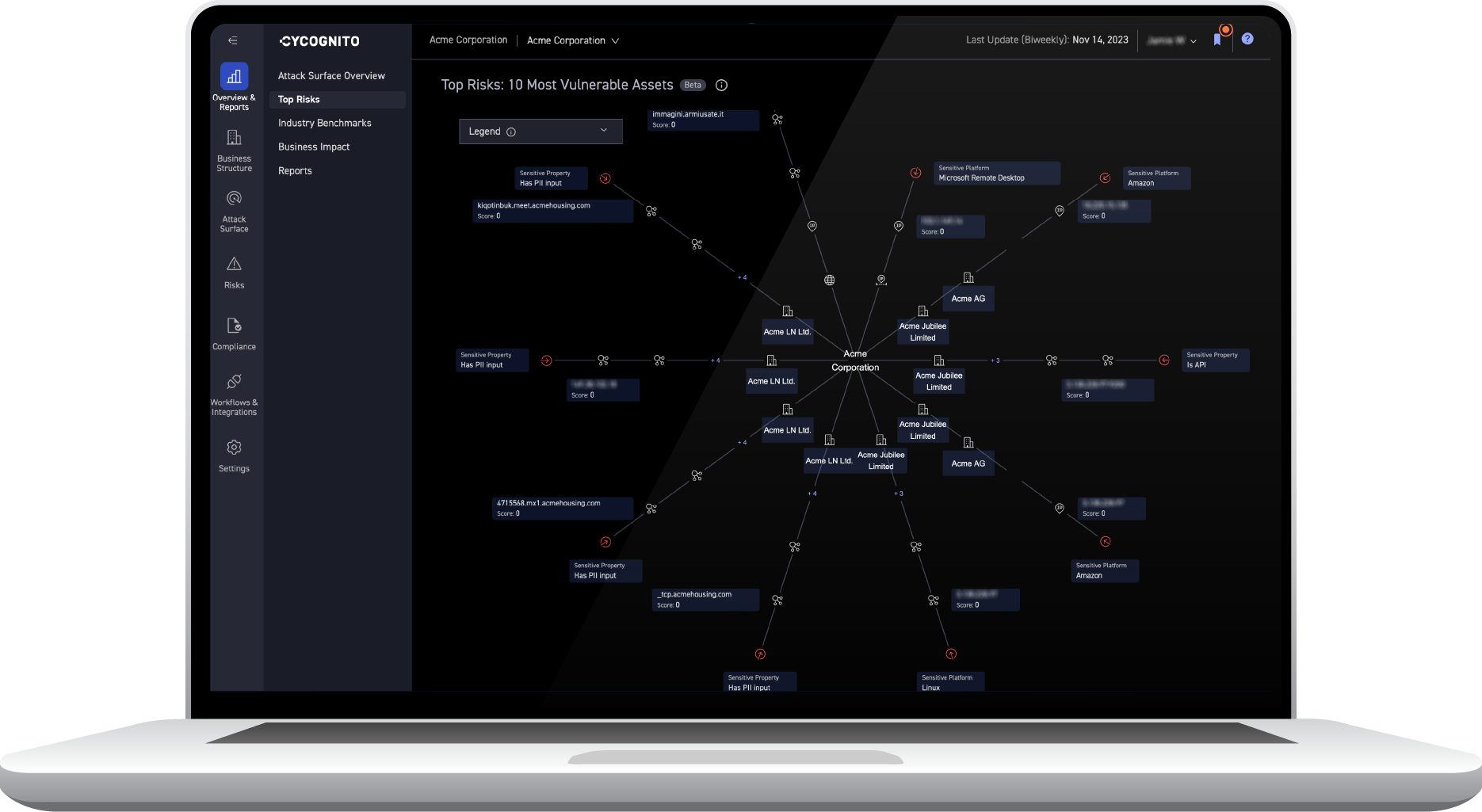
Detect security gaps across your entire Internet-facing perimeter
The platform goes further than scanning active external IPs and vulnerable software, as legacy vulnerability assessment (VA) solutions do. It searches beyond common vulnerabilities and exposures (CVEs) to detect data exposures, misconfigurations and even zero-day vulnerabilities.
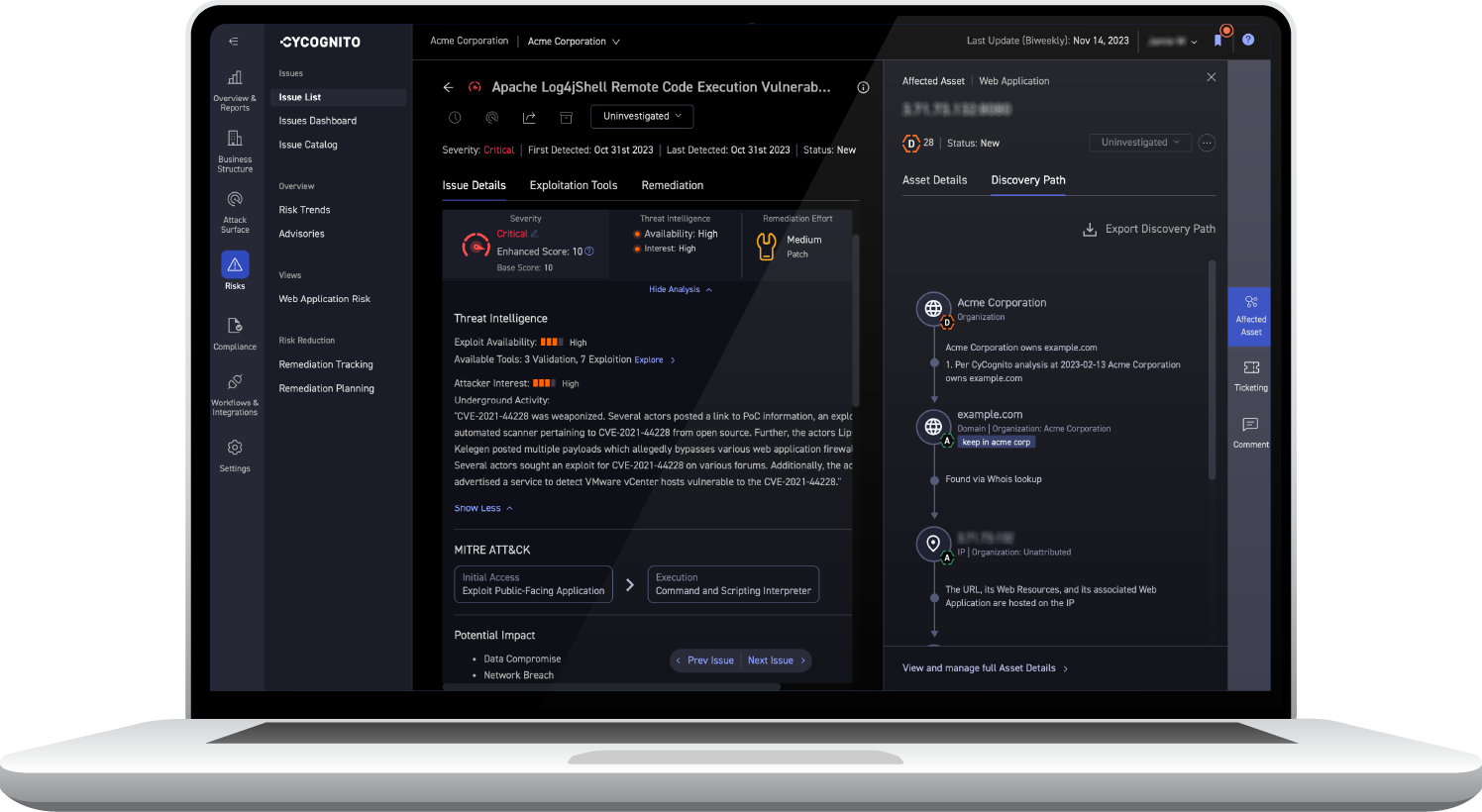
Powerful Risk Prioritization
Prioritize high-risk threats first
The CyCognito platform automatically prioritizes attack vectors based on attacker priorities, business context, discoverability, ease of exploitation, and remediation complexity. This gives you clear and effective prioritization to cut through the noise and identify your most critical risks.
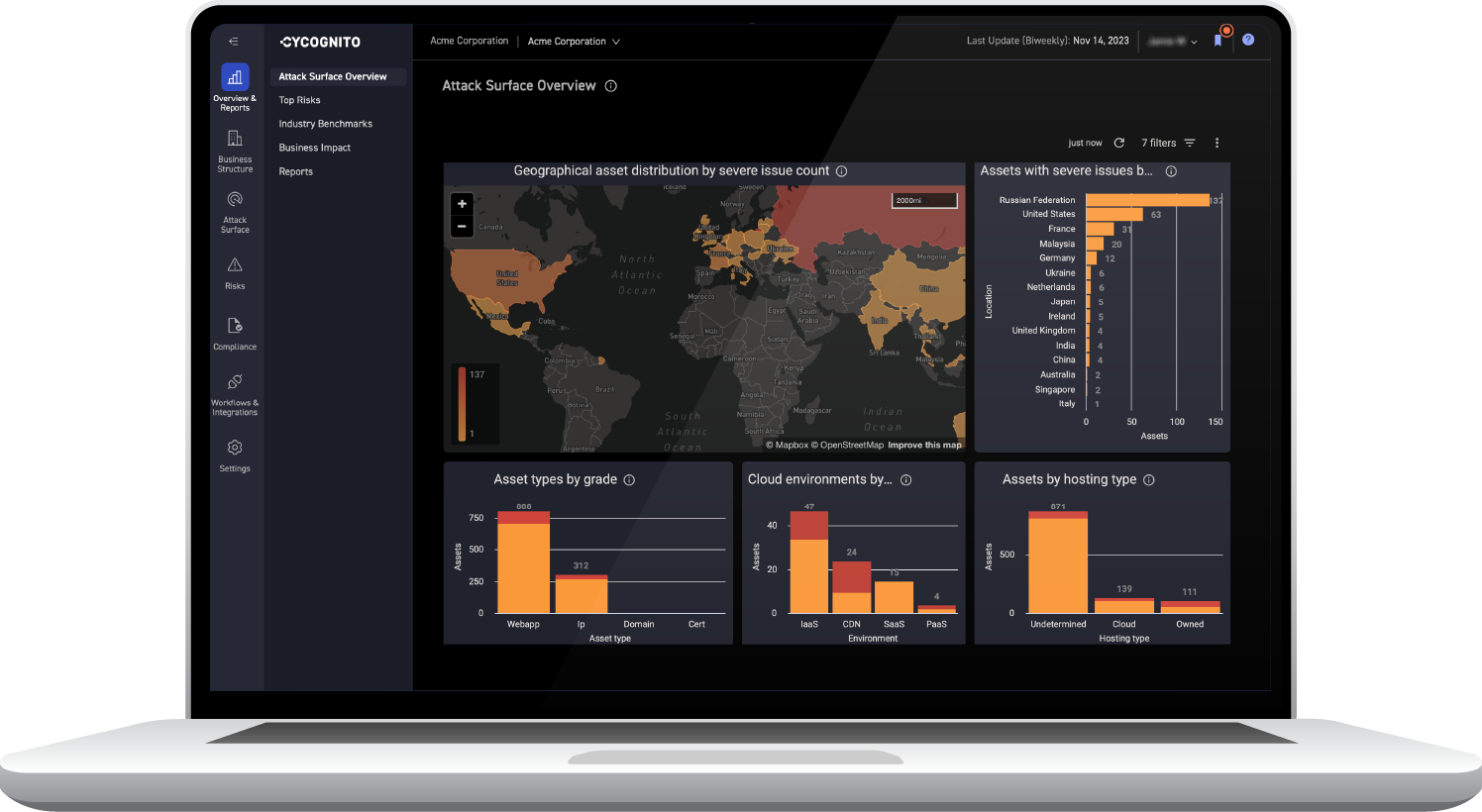
Actionable Analytics
Get ahead of attackers with attack surface analytics
The CyCognito platform automatically prioritizes attack vectors based on attacker priorities, business context, discoverability, ease of exploitation, and remediation complexity. This gives you clear and effective prioritization to cut through the noise and identify your most critical risks.
Robust Workflow Recipes
Integrate with your existing workflows
The CyCognito platform offers a rich library of no-code, pre-built, and custom RESTful integrations and workflows that enrich and unify asset management, security operations, and risk management processes. This streamlines and enhances IT workflows, while improving security posture.
CyCognito Research Report
State of External Exposure Management, Summer 2023 Edition
Download CyCognito’s State of External Exposure Management Report to learn key recommendations that your Security teams can implement to improve their exposure management strategy and minimize risk.
External Attack Surface Management
Frequently Asked Questions
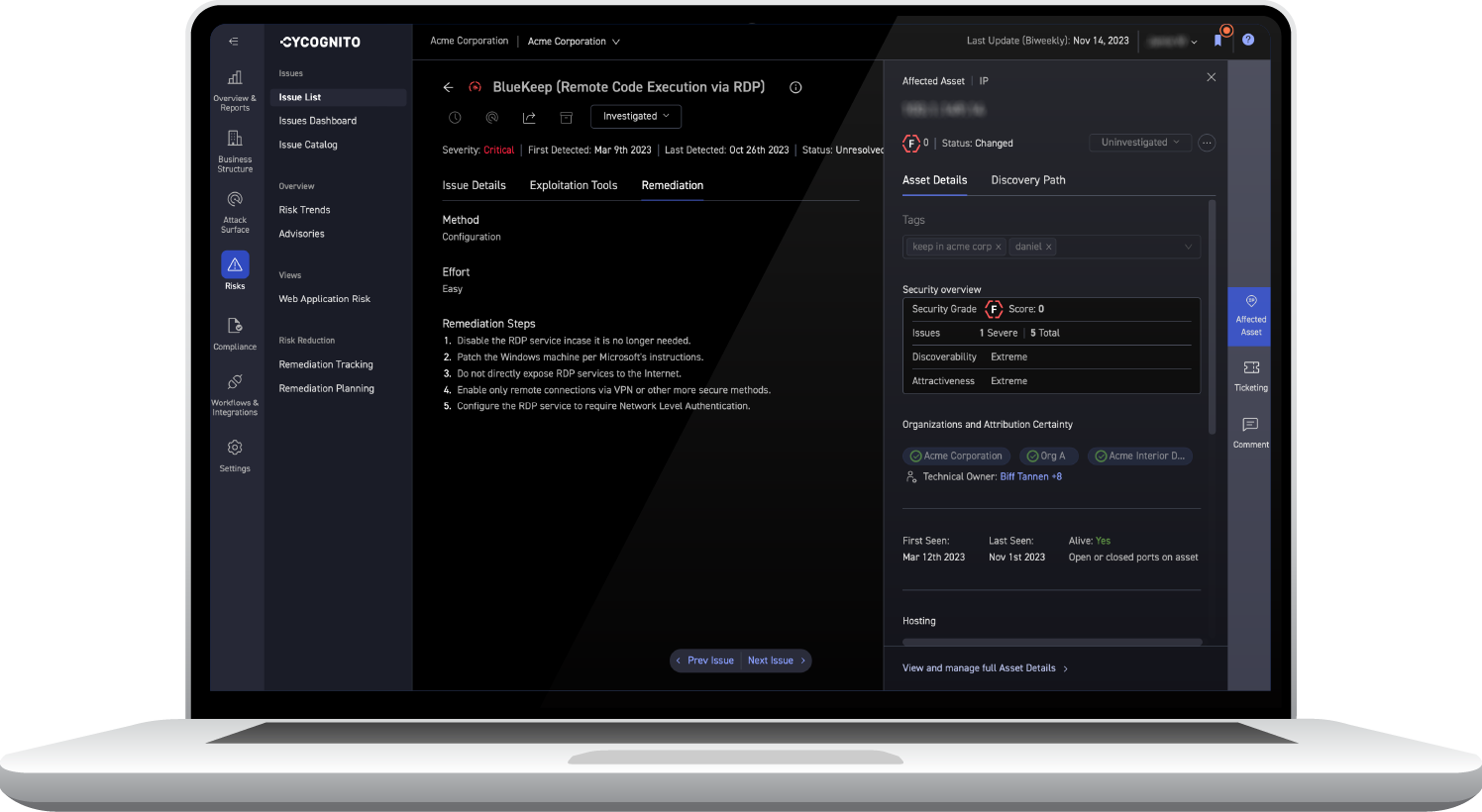
How does the CyCognito platform analyze the attack surface?
The CyCognito platform discovers and tests all assets discoverable via the internet. This process finds assets that were previously unknown, unmonitored, and exposed to attack. The platform continuously monitors and tests all assets associated with an organization. It alerts to new, existing, or recurring issues, and provides remediation guidance to fix those issues and eliminate the risk presented by that asset.
What are attack vectors?
Attack vectors are paths into an organization’s network via issues detected in the attack surface. Sometimes these attack vectors are single steps (like an exposed remote access protocol which provides direct access to a system), or multi-step (like a vulnerability which must be exploited to allow for privilege escalation that gives an attacker control)
What are the benefits of attack surface protection?
Organizations cannot remove all of their assets from the internet, otherwise they would be unable to do business in today’s digital world. Attack surface protection delivers more than just a digital asset inventory, it ensures that an organization’s exposed and connected IT assets are known, secure, monitored for issues and defended against attacks.
What are the implications of having no attack surface protection in place?
Without attack surface protection, an attacker can access systems, steal or ransom user data, plant malware, move laterally in your supply chain, and change configurations. Those actions can disrupt business, impact company reputation, and pose physical dangers in the case of IT and IOT systems. For good examples of what happens when attack surface protection is neglected, you can read more from SANS.
How do you compare with Qualys or Tenable?
Legacy vulnerability assessment (VA) tools are focused on scanning targets within the perimeter with authenticated scans against known IP ranges. The CyCognito platform differs by approaching the attack surface as an attacker would, from the outside. We automatically discover all of the organization’s internet-exposed attack surface to establish a complete picture of the attack surface. We then evaluate the security posture of those internet-exposed assets (both known and unknown to the business), without authentication, and provide prioritized remediation guidance based on business impact.
What IT Tools do you integrate with?
CyCognito seamlessly shares information, such as alerts and issue evidence, through frictionless workflow integrations with over 400 popular IT tools, including ticketing systems, SIEMs, SOARs, XDR platforms such as ServiceNow, Jira, QRadar, ZenDesk, Tenable, and Splunk.
What Open Source Intelligence is used?
A variety of sources are used, including passive DNS, Wikipedia, public financial data, whois, and certificate databases.
How can CyCognito help with attack surface protection and reduction?
The platform provides the continuous visibility necessary to understand and truly know your attack surface, even when that attack surface grows and changes daily due to the proliferation of cloud and SaaS applications. The platform also provides the guidance needed by security operations teams to identify high risk areas, monitor threats, and secure those exposed assets.
What are some attack surface reduction and protection best practices?
Attack surface protection best practice includes continuous asset discovery across the entire internet looking for new and existing internet-exposed assets that belong to your company, developing business context about how assets relate to the business, active security testing of those assets, and providing IT teams guidance to expedite remediation.
How do you compare with BitSight or SecurityScoreCard?
Generally security rating services present simple personal credit-like scores for the entire attack surface but do not provide detailed evidence. The CyCognito platform performs multi-factor testing of those assets and issues, providing actionable intelligence on what needs to be fixed first, and how to do it.
How do you compare with RiskIQ or Expanse?
Generally speaking, legacy attack surface management vendors focus on the discovery and inventory of internet-exposed assets. They don’t answer the question, “What do I do with this information?”
CyCognito does. As a foundation, we provide that comprehensive, complete inventory, and go a step beyond legacy solutions to automatically associate discovered assets with their business context, such as what processes they’re a part of.
Then, the platform actively tests the security of that inventory to show where exposed vulnerabilities, security gaps, or misconfigurations could be used by an attacker.
We use all of this together, along with exploitability and attractiveness of those issues to attackers, to guide security operations teams to remediate the 10 issues that present 90% of risk first.
Take the next step.
Close your security gaps with CyCognito's zero-input discovery, automated testing, and risk-based prioritization of your attack surface.
Calculate Your Savings
Answer a few questions and receive an instant custom report sharing how you can reduce costs and boost your efficiency with CyCognito.
 Live CyCognito Demo
Live CyCognito Demo