What Is Microsoft Defender EASM?
Microsoft Defender External Attack Surface Management (EASM) is a cybersecurity solution designed to secure digital environments by managing the external attack surface. This tool provides visibility into assets visible to potential attackers.
Defender EASM supports security postures by uncovering hidden threats and vulnerabilities. As organizations grow, their digital footprint increases. Microsoft Defender EASM aids in managing these assets, ensuring they are monitored and protected against external threats.
Key Features of Microsoft Defender EASM
Microsoft Defender External Attack Surface Management (EASM) offers the following capabilities:
- Discovery and inventory: Helps identify assets connected to the organization, including previously unknown or unmonitored ones. The discovery process includes domains, IP blocks, hosts, email contacts, ASNs, and WHOIS organizations. It indexes and categorizes these assets.
- Risk insight dashboards: Dashboards provide an at-a-glance view of the organization's online infrastructure, highlighting critical risks such as vulnerabilities and compliance gaps.
- Asset management and custom filtering: Allows users to filter and customize the inventory view based on specific needs, such as isolating assets linked to deprecated infrastructure or identifying new cloud resources.
- Role-based user permissions: Owners and Contributors can create, modify, and delete resources, while Readers can only view data, maintaining strict control over sensitive information.
- Data residency and compliance: Microsoft adheres to strict compliance standards, with customer-specific data stored in regions chosen by the customer. Data retention policies ensure that customer data is securely deleted after 180 days if they cease to be a customer.
- Global and customer-specific data integration: Integrates global Microsoft data with customer-applied labels to offer a unified view of the attack surface.
How Microsoft Defender EASM Works
Microsoft Defender External Attack Surface Management (EASM) provides a systematic approach to identify and manage the assets within an organization’s external attack surface. Its discovery process ensures comprehensive visibility, addressing risks associated with unmonitored or unknown digital properties.
Here’s how it operates:
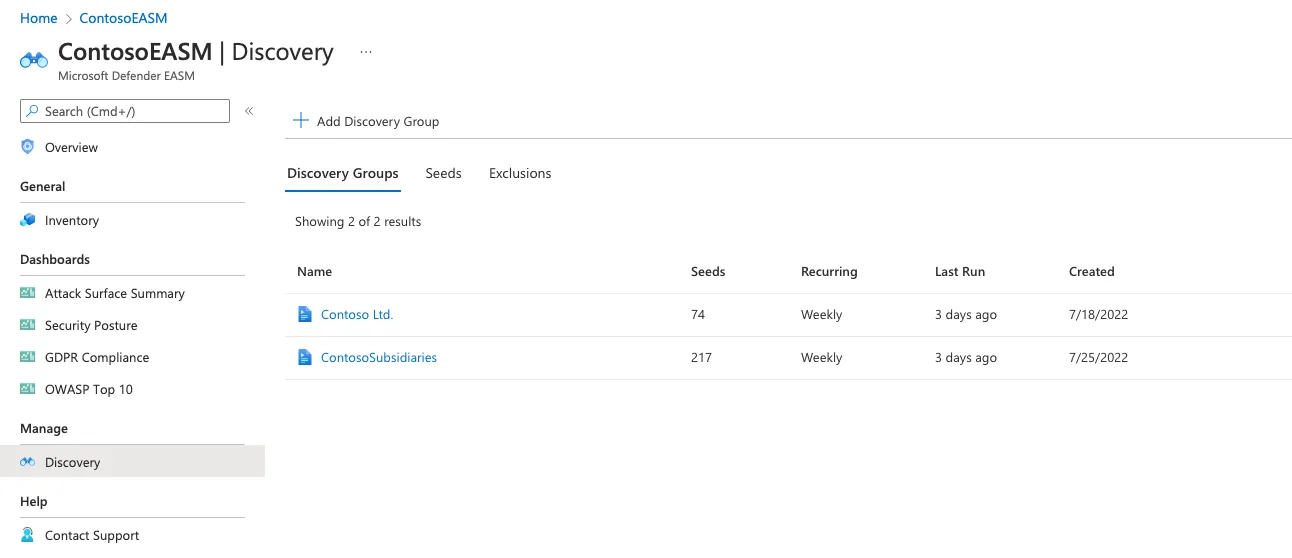
- Discovery capabilities: The system begins with "seeds," which are known assets like domains, IP blocks, hosts, email contacts, ASNs, or WHOIS organizations. These seeds serve as starting points for recursive scans, identifying associated infrastructure and revealing additional assets that are connected to the organization.
- Recursive asset mapping: The discovery engine uses each seed to explore first-level connections, such as domains registered with the same contact email or hosts resolving to shared IP blocks. These connections expand into second-level and third-level links, creating a detailed map of the attack surface. The process continues until the system reaches the boundaries of assets the organization is responsible for managing.
- Automated and customized inventories: Organizations can start with prebuilt inventories derived from Microsoft’s existing data or create customized inventories using Discovery Groups. These groups allow users to manage seed lists and schedule recurrent discoveries, tailoring the process to their needs.
- Dynamic asset classification: Discovered assets are categorized into several states, including approved inventory, dependencies, candidate assets, “monitor only” assets, and items requiring investigation.
- Continuous monitoring: Once the inventory is populated, Defender EASM repeatedly scans the assets using virtual user technology. This process gathers data on asset behavior and content, uncovering vulnerabilities, compliance issues, and other risks.
- Unified management: All discovered assets are indexed in a centralized inventory, providing a dynamic system of record.
Tutorial #1: Create a Defender EASM Azure Resource
This guide explains how to set up a Microsoft Defender External Attack Surface Management (Defender EASM) Azure resource using the Azure portal. Instructions in this tutorial and the following one are adapted from the Defender EASM documentation.
Prerequisites
Before proceeding, ensure the following:
- You have an Azure subscription or have created a free Azure account.
- You hold a Contributor role in Azure.
- Familiarize yourself with the Azure portal.
Steps to Create a Defender EASM Azure Resource
- Create a resource group
- Log in to the Azure portal and select Resource Groups from the homepage.
- Click Create.
- Fill in the following Subscription, Resource Group, and Region fields.
- Click Review + Create to confirm the details and then select Create.

Source: Azure
- Create a Defender EASM resource
- In the Azure portal search bar, type Microsoft Defender EASM and press Enter.
- From the results, click Create to start creating a Defender EASM resource.
- Fill in the Subscription, Resource Group, Name, and Region fields.
- Click Review + Create to validate the entries, and then select Create.
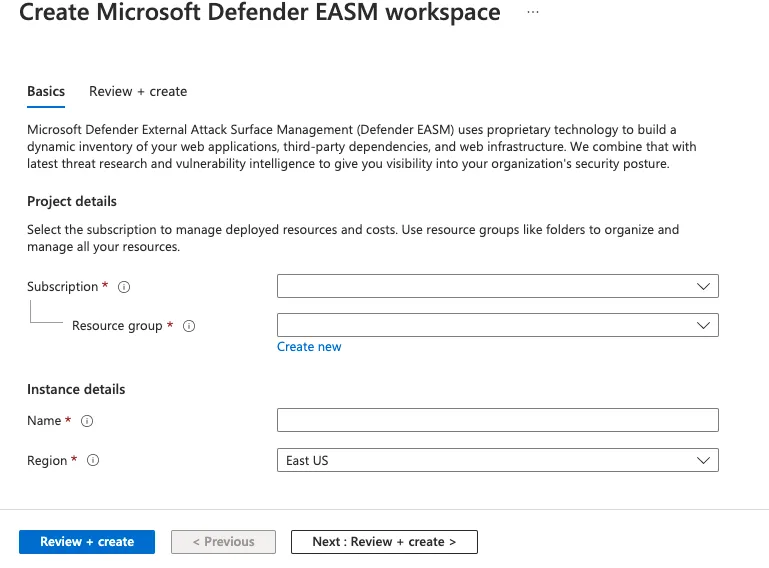
Source: Azure
Once the resource is successfully created, you can navigate to it and begin using Defender EASM to manage and secure your external attack surface.
Product Limitations
As you evaluate Microsoft Defender EASM, you should be aware of the following limitations, reported by users on the G2 platform:
- Complex setup and integration: Initial configuration and integration can be challenging, particularly for organizations with diverse IT environments. The learning curve for new users may require significant time and effort.
- Interface and navigation challenges: The user interface could benefit from enhancements to improve navigation and usability. Users sometimes report getting lost while navigating the tool, indicating a need for a more intuitive flow.
- Performance issues: The tool may experience slower performance during peak usage times, and its processing power and storage requirements can be high compared to similar solutions.
- False positives: Defender EASM occasionally generates false positives, requiring additional manual checks to validate findings. This can impact the efficiency of vulnerability management processes.
- UI and data management enhancements needed: The data placement, filtering options, and overall user experience could be more refined to meet user needs effectively.
- Stability issues: Some users report occasional software bugs, especially following Windows updates, which can disrupt operations.
- Overblocking and configuration complexity: The solution can sometimes enforce overly simplistic blockings, potentially leading to unnecessary interruptions. Additionally, its configuration is perceived as more complex than competing tools.
- Cost considerations: While pricing is generally reasonable, it may be on the higher side for some organizations, especially smaller ones with limited budgets.







 Complimentary Report
Complimentary Report