



Palo Alto Cortex Xpanse is an active attack surface management (ASM) solution. It helps organizations discover, understand, and mitigate risks across their entire digital ecosystem. By continuously scanning the internet, it identifies and addresses vulnerabilities in connected systems and exposed services before attackers can exploit them. This ensures organizations can respond swiftly to risks from unknown or unmanaged assets.
Cortex Xpanse automates the discovery and remediation of security blind spots, scanning over 500 billion ports daily and indexing all IPv4 addresses multiple times a day. This allows it to provide comprehensive visibility into internet-exposed assets.
Cortex Xpanse uses discovery, learning, and response mechanisms to help organizations identify and mitigate risks. Its key features include:
Pricing for Cortex Xpanse is not publicly disclosed and varies based on factors such as the number of assets monitored and specific organizational requirements. According to eSecurityPlanet, a web-based subscription covering up to 999 assets with basic customer support is priced at $95,000 per year.
Cortex Xpanse has some limitations that organizations should consider. These include challenges related to integration, usability, and functionality. These limitations were reported by users on Gartner Peer Insights:
Related content: Read our guide to attack surface analysis.

Access the GigaOm Radar for Attack Surface Management 2025 to get an overview of the available ASM solutions, identify leading offerings, and evaluate the best solution for you.
In light of the above limitations, organizations should consider Cortex XPanse alternatives. Here are a few popular alternatives.

Source: CyCognito
The CyCognito platform addresses today’s exposure management requirements by taking an automated multi-faceted approach in identifying and remediating critical issues based on their business impact, rather than focusing on the generic severity of the threat alone. To do this you need a platform that is continuously monitoring the attack surface for changes and provides intelligent prioritization that incorporates organizations context.
The CyCognito platform addresses today’s vulnerability management requirements by:
Learn more about the Cycognito Attack Surface Management Platform.
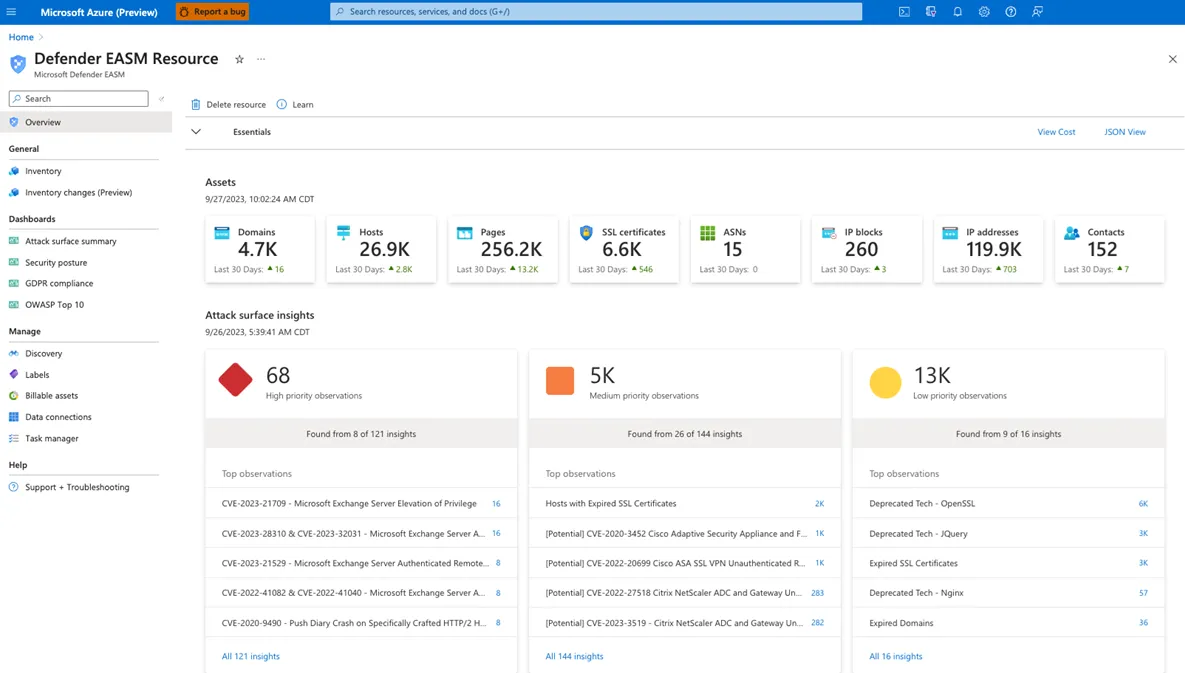
Source: Microsoft
Microsoft Defender EASM offers tools for managing and mitigating risks associated with external attack surfaces. It helps organizations maintain continuous visibility into unmanaged and shadow IT resources in dynamic, hybrid environments. Its AI-driven capabilities enable cloud security teams to discover, classify, and prioritize vulnerabilities.
Key features include:
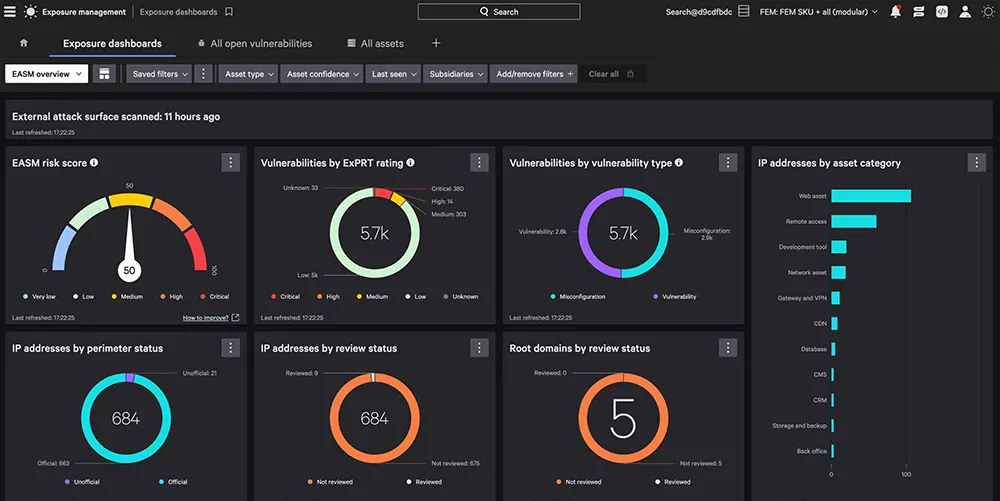
Source: CrowdStrike
CrowdStrike Falcon Surface provides external attack surface management (EASM) capabilities, helping organizations to discover, assess, and secure their internet-facing assets. By leveraging adversary-driven insights, it allows teams to identify and mitigate risks from exposed and unmanaged resources.
Key features include:
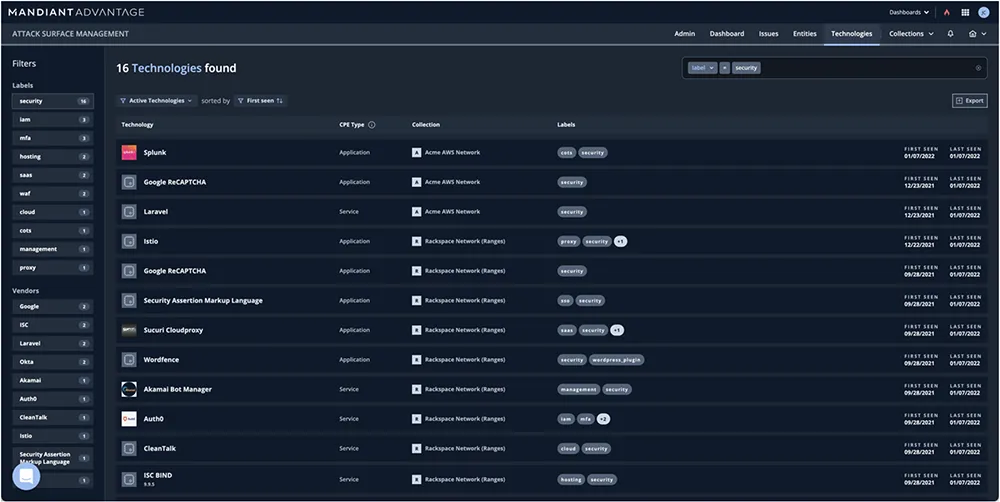
Source: Google Cloud
Mandiant Attack Surface Management offers organizations the ability to see their attack surface from an adversary's perspective. By automating asset discovery and analysis, it identifies vulnerabilities, misconfigurations, and exposures across dynamic, distributed, and hybrid IT environments.
Key features include:
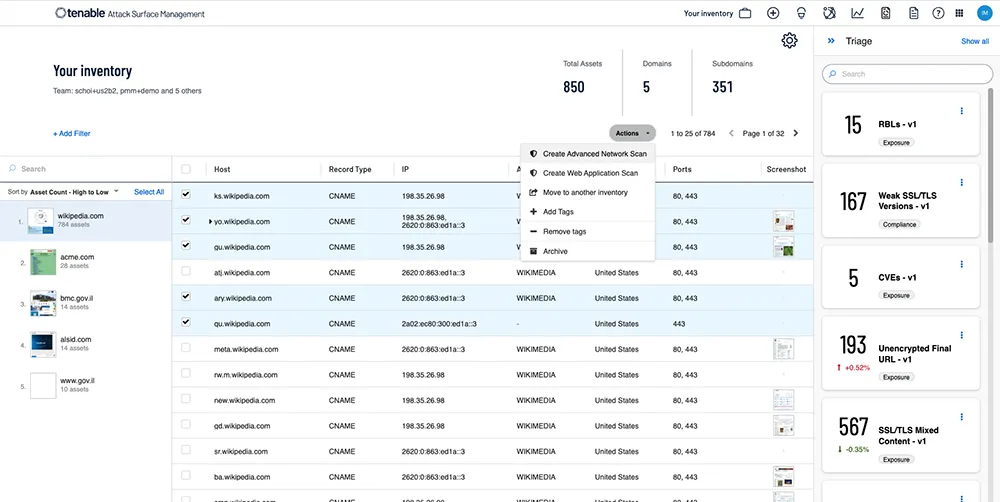
Source: Tenable
Tenable Attack Surface Management provides organizations with a view of their internet-connected assets, services, and applications, enabling proactive risk management. By mapping the internet, the tool uncovers known and unknown assets and integrates with Tenable's broader suite of security tools for attack surface visibility and mitigation.
Key features include:
Organizations seeking external attack surface management solutions can choose from a variety of tools tailored to their needs. These alternatives provide capabilities such as continuous asset discovery, risk prioritization, shadow IT identification, and multicloud visibility, often integrating with existing security workflows. By leveraging automated analysis and actionable insights, these tools enable businesses to mitigate risks and improve their overall security posture.

Access the GigaOm Radar for Attack Surface Management 2025 to get an overview of the available ASM solutions, identify leading offerings, and evaluate the best solution for you.