What Are API Security Tools?
API security tools are software designed to protect application programming interfaces (APIs) from various security threats. These tools help enforce security policies, detect and mitigate attacks such as SQL injection, and ensure secure data transfer between systems. API security is critical in today's interconnected software environment, where APIs serve as the primary method for system integration and data exchange.
These tools offer a range of features including authentication, authorization, traffic management, and encryption. By monitoring API traffic, security tools can identify and block malicious activities, ensuring that only legitimate users and applications have access to sensitive functions and data. This is essential in preventing data breaches and maintaining system integrity.
Key Features of API Security Solutions
Authentication and Authorization
Authentication verifies the identity of a user or system using an API, typically through credentials like tokens. This security layer ensures that only authenticated users can access an API. After authentication, authorization determines the user's permissions, limiting access to various parts of the API based on roles or policies. This prevents unauthorized access to sensitive data and functions within the system.
Implementing effective authentication and authorization protocols is fundamental to API security. Modern API security solutions usually support various authentication methods such as OAuth, API keys, and JWTs, providing robust security by aligning with the latest standards and practices.
Rate Limiting and Throttling
Rate limiting controls the number of API requests a user or service can make within a specific timeframe, while throttling adjusts the speed of incoming requests. These features protect APIs from overload, ensuring the API’s availability and performance remain stable even under high traffic conditions. This is particularly important to mitigate denial-of-service (DoS) attacks, where attackers attempt to flood the API with an excessive amount of requests.
Throttling and rate limiting both serve as practical approaches to manage and distribute server resources efficiently. By limiting how often users can call an API, these mechanisms help maintain service quality and prevent abuse, ensuring that all users receive fair access to the API.
Logging and Monitoring
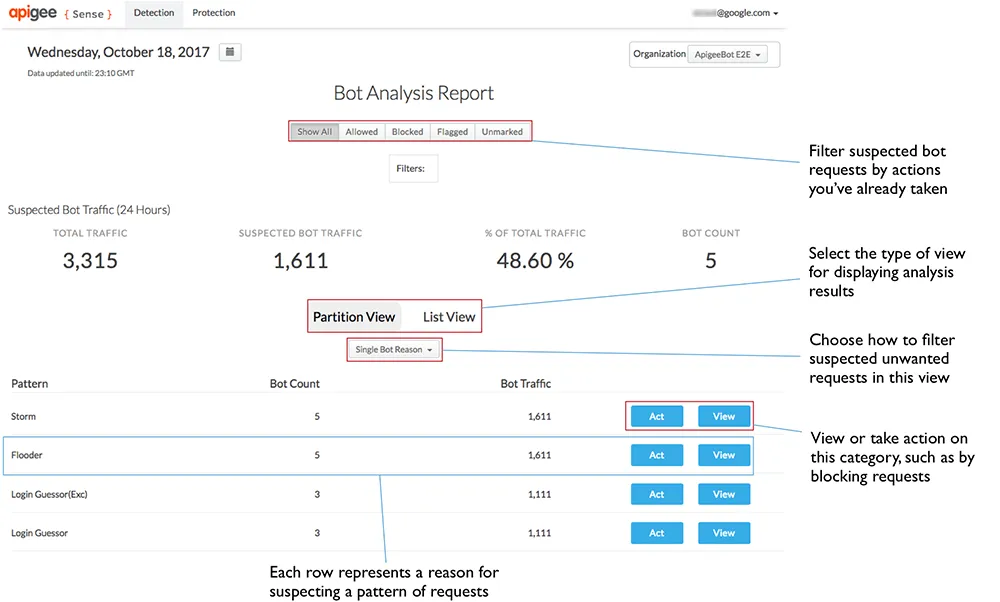
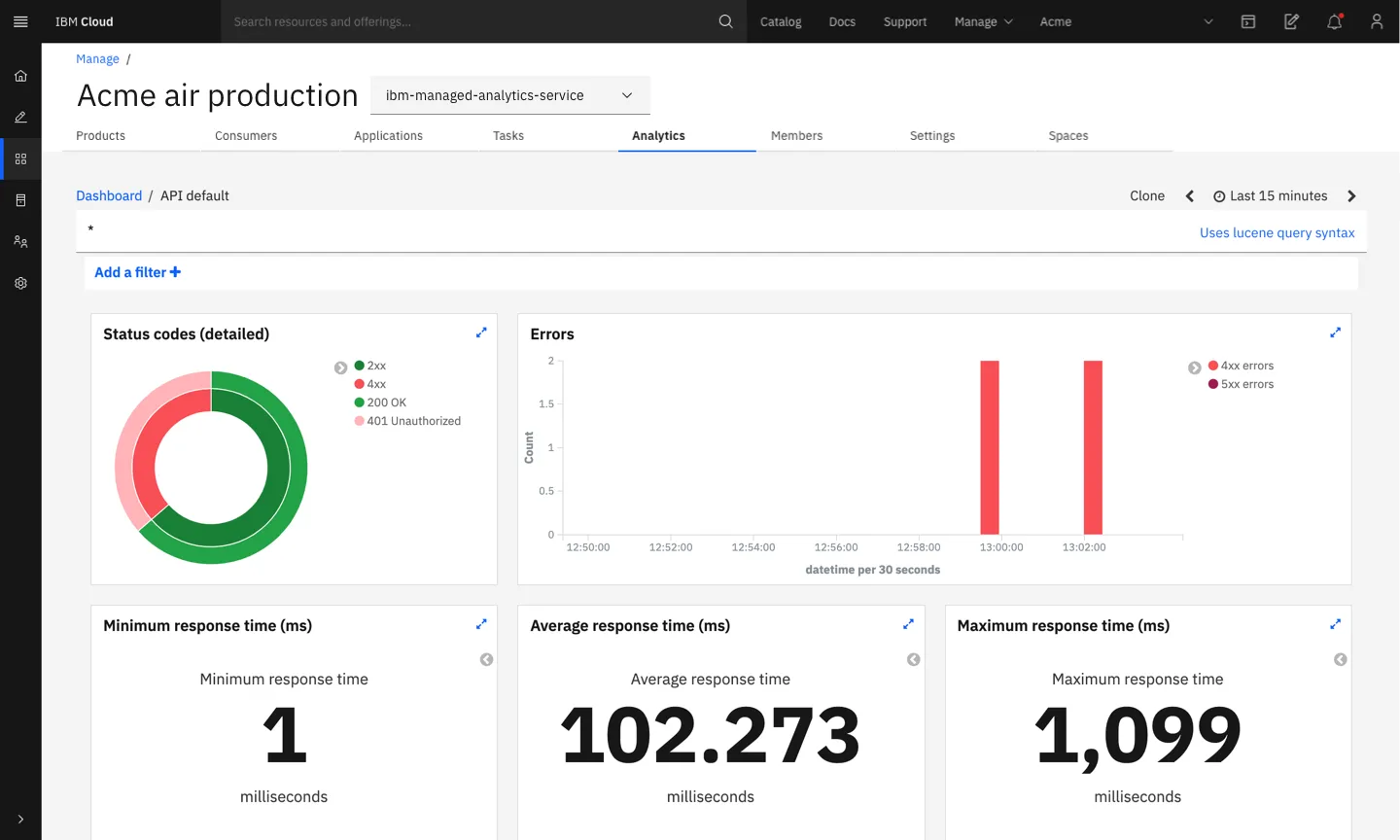
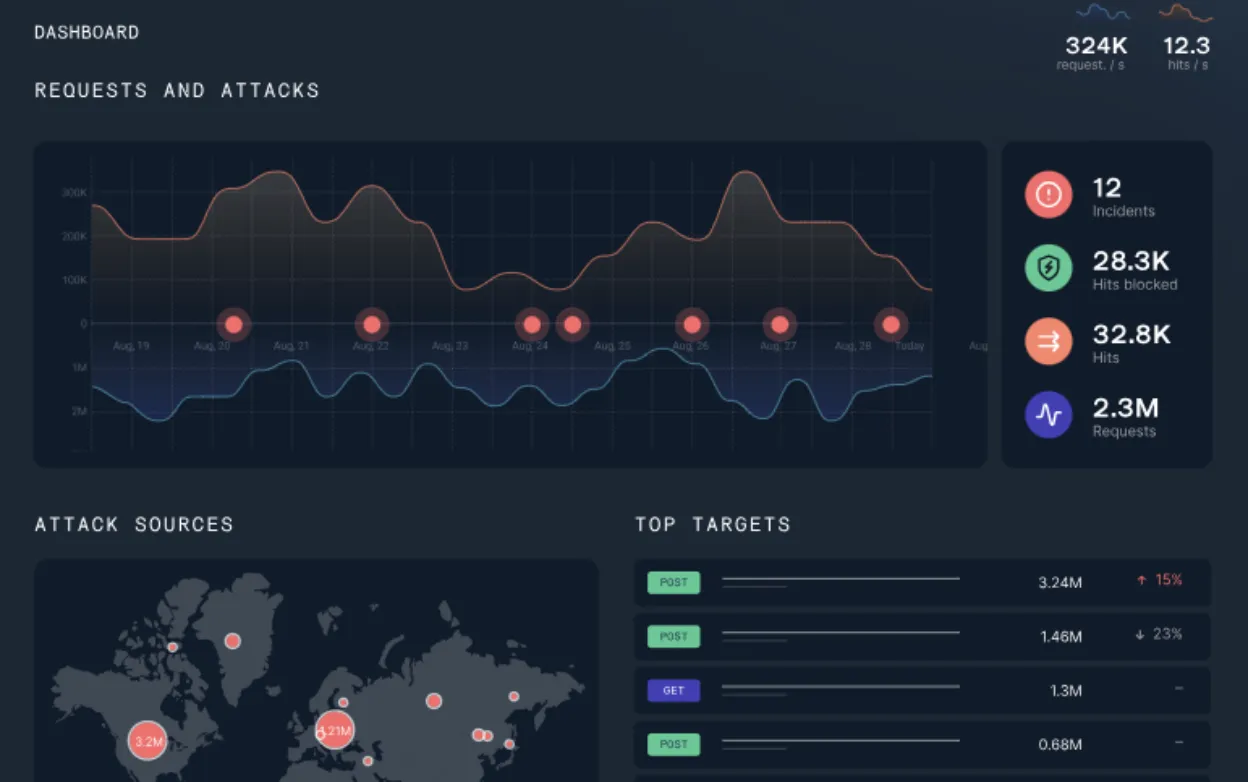
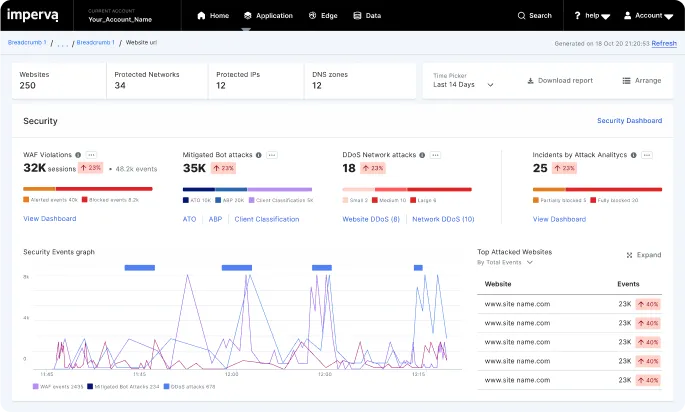
Logging involves recording API usage data, while monitoring is the continuous review of this data to identify unusual or harmful activities. Effective logging and monitoring can provide comprehensive visibility into API performance and security, identifying potential security incidents as they happen. This allows organizations to respond promptly to threats, minimizing potential damage.
Logs typically include details about API requests such as the source, destination, and payload. Monitoring these logs helps in diagnosing issues, performing audits, and understanding user behavior. Together, logging and monitoring form a critical part of API security, enabling proactive management and security assurance.
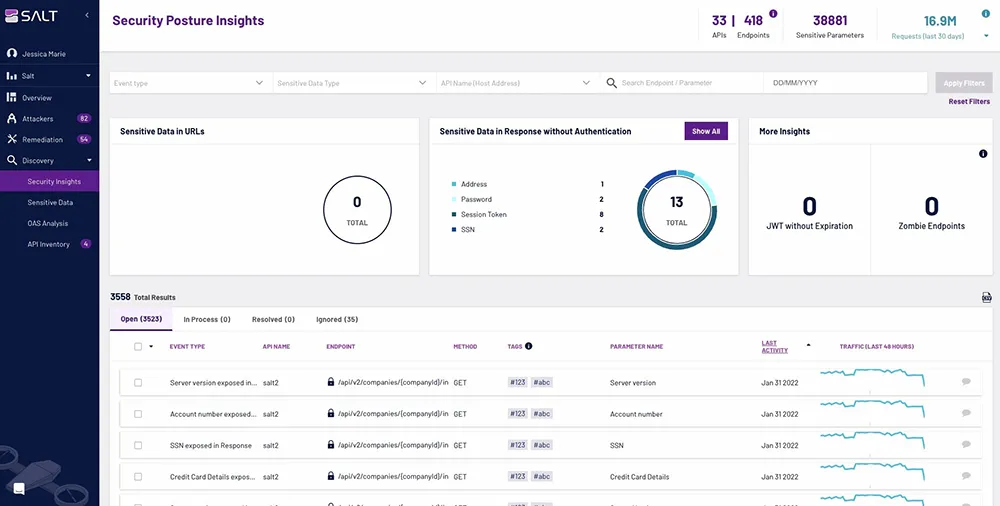
Vulnerability Testing and Security Assessments
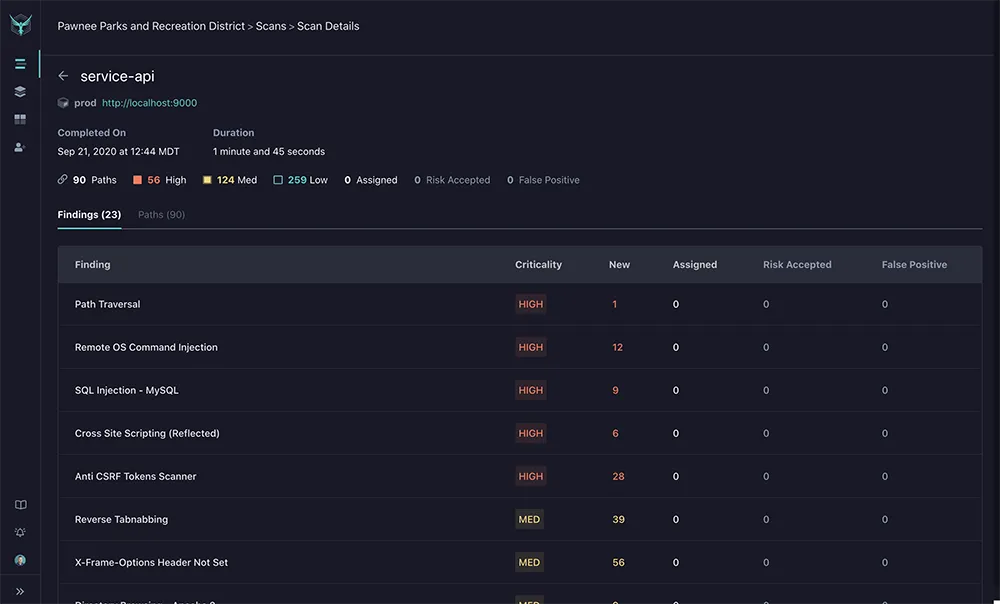
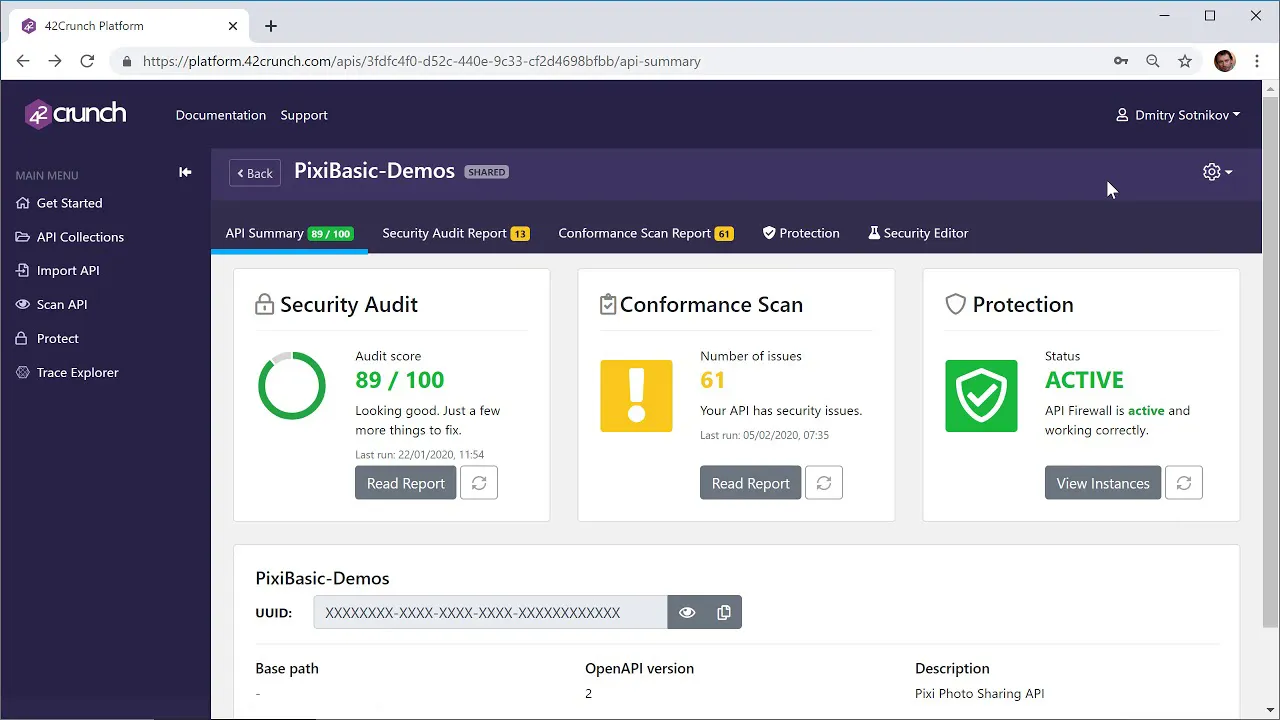
Vulnerability testing involves probing an API for security weaknesses, while security assessments evaluate the overall security posture of an API setup. Regular testing and assessments ensure that APIs remain secure against evolving threats.
Automated tools can perform vulnerability testing, simulating attacks and reporting potential weaknesses. Security assessments might involve manual review and comparison against security best practices. Both activities are fundamental in maintaining robust API security frameworks and safeguarding data.
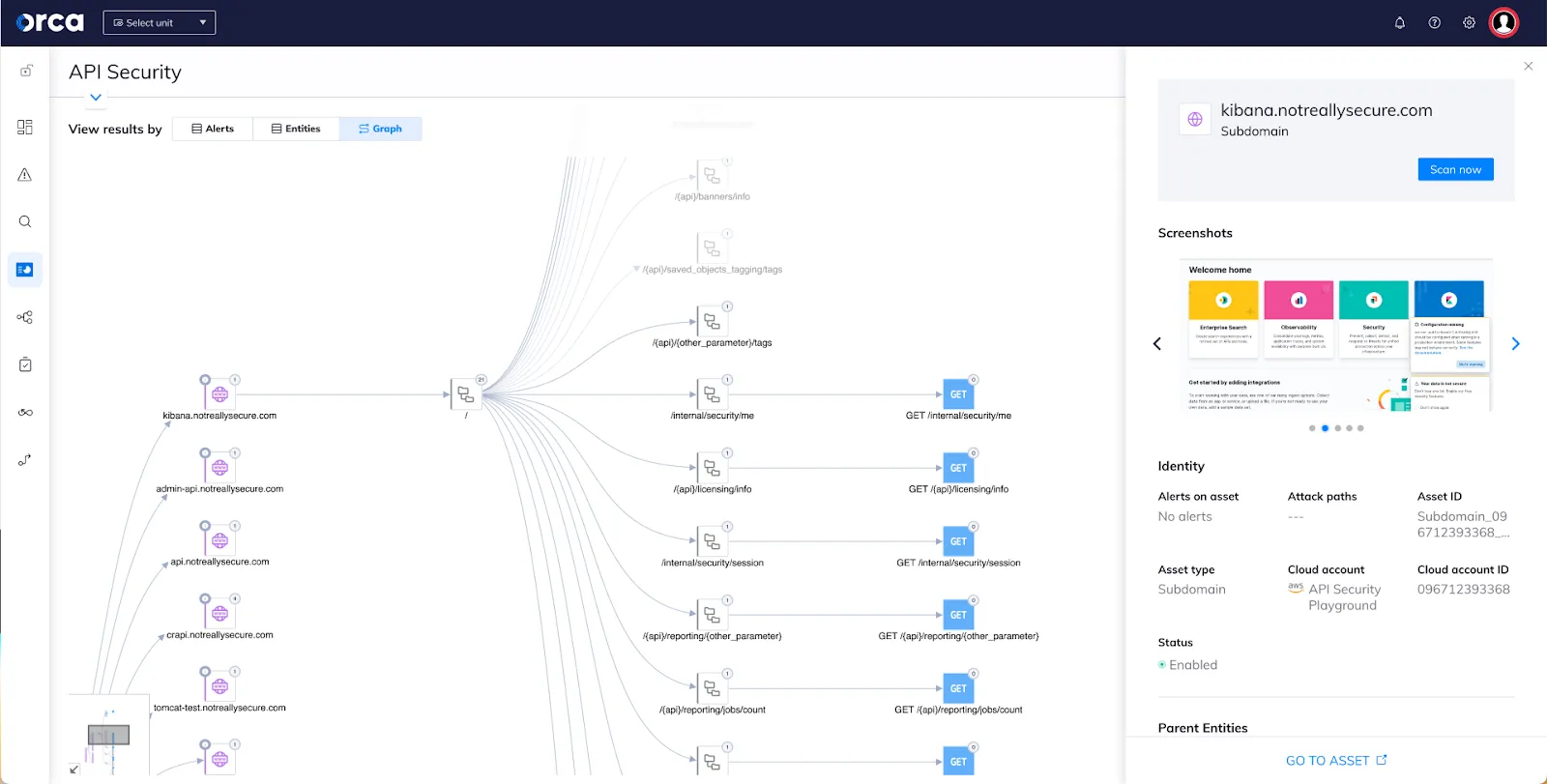
API Gateway
An API gateway acts as a managing point in the API ecosystem, facilitating secure and efficient interactions between clients and services. It provides a single entry point for all API traffic, incorporating security, routing, and other management functions. The gateway can enforce SSL/TLS encryption, authenticate requests, and apply policies uniformly, enhancing security across all services.
Besides security, API gateways optimize service delivery by handling request routing, load balancing, and caching. This not only improves security but also enhances the performance and scalability of API services. An API gateway simplifies API management and is a key component of modern API architecture.
Related content: Read our guide to API discovery.







 Complimentary Report
Complimentary Report