Research Reports
Security research reports and views from industry analysts on CyCognito’s products and the company.
Featured Reports
GigaOm Radar for Attack Surface Management
GigaOm Research Report
The expansion of an organization's attack surface continues to present a critical business challenge. Download the GigaOm Radar for Attack Surface Management to get an overview of the available ASM solutions, identify leading offerings, and evaluate the best solution for you.
State of External Exposure Management, Summer 2024 Edition
CyCognito Research Report
Download the report now to stay ahead of emerging threats and strengthen your organization’s security posture for 2024.
2024 State of Web Application Security Testing
CyCognito Research Report
The 2024 State of Web Application Security Testing report analyzes responses from hundreds of cybersecurity professionals in both the US and the UK, providing valuable insights into the current state of web application security testing.
Recent Reports
State of External Exposure Management, Summer 2023 Edition
CyCognito Research Report
Download CyCognito’s State of External Exposure Management Report to learn key recommendations that your Security teams can implement to improve their exposure management strategy and minimize risk.
The Total Economic Impact™ of The CyCognito Platform
Forrester Research Report
Read The Total Economic Impact™ of The CyCognito Platform — a Forrester study. Cost Savings And Business Benefits Enabled By The CyCognito Platform.
Attack Surface Management: The Foundation of Risk Management
IDC Technology Assessment Guide
Download the IDC EASM buyers guide and understand the key capabilities to look for when selecting an External Attack Surface Management solution with expert guidance and selection criteria from analyst firm IDC.
Teamwork Shines A Light On Hidden External Risk
Forrester Research Report
Download Forrester Consulting’s thought leadership paper “Teamwork shines a light on hidden external risks” to uncover what your organization can do to improve its risk management strategy.
Gaps in Attack Surface Monitoring and Security Testing for Cyber-risk Mitigation
Enterprise Strategy Group Research Report
Download the report to learn why security testing and attack surface monitoring work hand in hand.
Security Hygiene and Posture Management
Enterprise Strategy Group Research Report
Are your legacy vulnerability and asset management and penetration testing practices keeping your organization safe? Download the report to find out.
The State of External Attack Surface and Risk Management
Aimpoint Research Report
Learn how leveraging automation through modern EASM technology can help bridge the gap between attackers and defenders, making it possible for defenders to improve their security and risk posture.
External Risk Insights
CyCognito Research Report
Download this study to learn how to protect your most critical assets from being easily exploited by attackers as your enterprise expands to include more subsidiary brands and web applications.
Benefits of External Attack Surface Management (EASM) Across Both Security and IT
TAG Cyber Research Report
Download the report to learn how modern External Attack Surface Management and CyCognito enable value across enterprise security and IT teams.
Advice on External Attack Surface Management (EASM) Selection: Pure Play vs. Bundled
TAG Cyber Research Report
Download this report to receive guidance intended to serve as a starting point for making the best security decision for each unique organization.
The Danger of Subsidiary Sprawl and Unknown Unknowns in External Attack Surface Management
Solution Brief
What you don’t know can hurt your organization. Download the report to learn the dangers of subsidiary sprawl and other unknowns.
Infographics
Think Your External Attack Surface is Covered? Let’s Look at the Numbers.
Infographic
Organizations utilize vulnerability scanning, app security and pen testing. Despite this, it is easy to have a security testing gap of 45% from ideal.
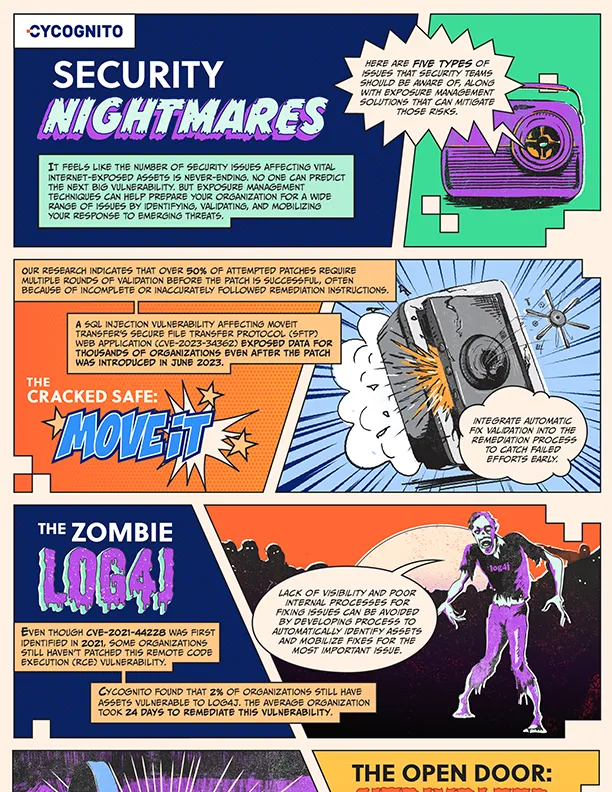
Security Nightmares of 2023 and How to Avoid Them in 2024
Infographic
CyCognito shares insights showing how security teams can learn from previous incidents and leverage exposure management techniques to stay ahead of attackers.
Cyber Monday is Just Once a Year – Active Security Testing Shouldn’t Be
Infographic
Cyber Monday is filled with urgency, but cybercriminals take advantage of this urgency to exploit misconfigurations and vulnerabilities. This can cause massive reputational damage to inattentive organizations in the process.