Exposure Management in Cybersecurity: Concepts and Technologies
2,426 views
What Is Exposure Management in Cybersecurity?
Exposure management (EM) is a cybersecurity practice that helps organizations identify and mitigate security risks in real time. It involves identifying access points, digital and physical assets that could be exposed to cyberattacks, mapping the organization’s attack surface, assessing risks, prioritizing and mitigating exposures, and continuously monitoring for new exposures. There are two core component of an exposure management strategy:
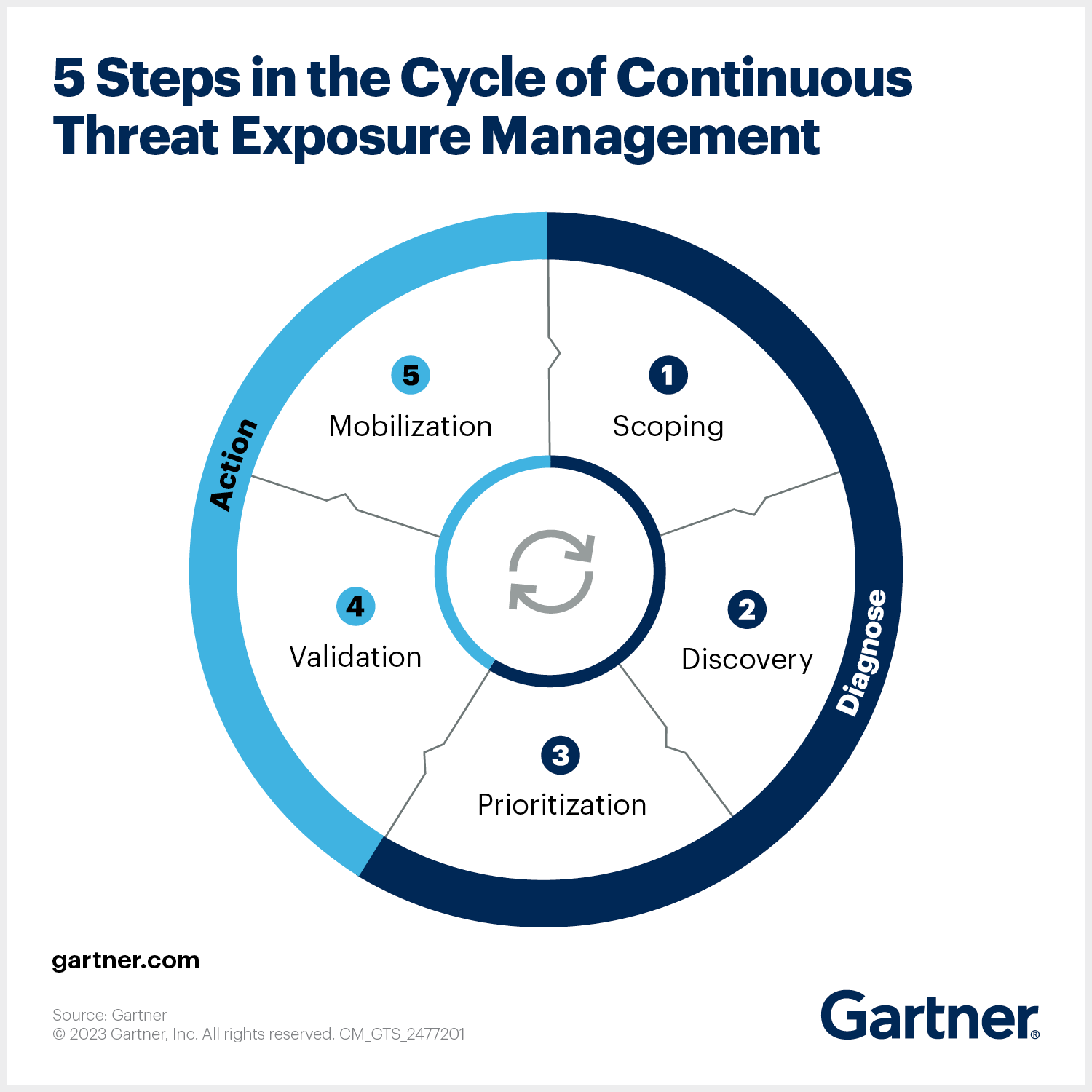
- A Cyber Threat Exposure Management (CTEM) framework: Lays out the organizational structure and process for exposure management. A CTEM framework has five key steps: Scoping, Discovery, Prioritization, Validation, and Mobilization.
- Cybersecurity Mesh Architecture (CSMA): Enables organizations to combine security tools, such as External Attack Surface Management (EASM), application security, cloud security, and Cyber Asset Attack Surface Management (CAASM), to create an exposure management solution. We cover these and other technology components of exposure management in more detail below.
EM goes beyond reactive cybersecurity methodologies to help organizations understand how to respond to an attack and how to prevent one.
This is part of an extensive series of guides about data security.
Services that Manage Exposure
While organizations can develop exposure management capabilities in-house, managed security service providers (MSSPs) are starting to offer exposure management services, providing everything from threat identification to assisting with remediation efforts. There are several types of emerging exposure management services:
- Penetration Testing as a Service (PTaaS): Performs continuous, automated and manual testing for security vulnerabilities within an organization's network and systems. PTaaS providers combine automated tools and human expertise to identify and exploit security weaknesses and provide organizations with remediation guidance.
- Attack surface management services: Focus on providing a comprehensive view of all the accessible points (the attack surface) within an organization's IT environment that could be exploited by attackers, including shadow IT and forgotten or misconfigured components. These services provide insights into potential vulnerabilities and support mitigation strategies for reducing the attack surface.
- Internet of Things (IoT) and Operational Technology (OT) exposure management: Dedicated to managing the unique risks associated with IoT and OT environments. They involve identifying and inventorying IoT and OT assets, assessing their security posture, monitoring for abnormal behavior indicative of a security incident, and providing guidance for securing devices against potential threats.
What Is the Difference Between an Exposure and a Vulnerability?
The terms 'exposure' and 'vulnerability' are often used interchangeably in the context of cybersecurity, but they refer to different concepts.
Exposure refers to the state of being subject to potential harm from external threats. In other words, it reflects the possibility that an organization's systems may be attacked by cybercriminals.
Vulnerability refers to the weaknesses within the system that could be exploited by these external threats.
While it is important to fix vulnerabilities, it is equally important to understand and manage exposure. For example, the owner of a house in a risky neighborhood (equivalent to an exposure in cybersecurity) could take proactive measures like installing a security system or joining a neighborhood watch program, in addition to locking doors and fixing broken windows (equivalent to vulnerabilities). Exposures help an organization think more strategically about their cyber risks and take proactive action to reduce or mitigate them.
Understanding the Exposure Management Lifecycle
Step 1: Scoping
Scoping defines the boundaries of an organization's exposure management efforts. This step involves identifying critical assets, business processes, and potential attack vectors that need protection. Organizations determine the types of threats they face, assess their risk tolerance, and set objectives for exposure management.
A well-defined scope ensures that exposure management efforts remain focused and efficient. Organizations typically classify assets into categories such as cloud infrastructure, on-premises systems, applications, third-party integrations, and employee endpoints. Additionally, regulatory and compliance considerations, such as GDPR, HIPAA, or NIST frameworks, play a role in defining the scope.
Threat modeling is often used at this stage to anticipate attack scenarios and determine which parts of the organization are most at risk. By establishing a clear scope, security teams can align exposure management with business priorities and ensure that the most valuable assets receive the highest level of protection.
Step 2: Discovery
In the discovery phase, organizations conduct a thorough inventory of their attack surface, identifying all assets, systems, and applications that could be exposed to threats. This step includes external and internal discovery, covering known assets as well as shadow IT, unmanaged devices, misconfigured cloud services, and forgotten or abandoned applications.
Discovery methods include automated scanning, asset management tools, penetration testing, and manual security assessments. Organizations often leverage technologies like external attack surface management (EASM) and cyber asset attack surface management (CAASM) to gain visibility into their infrastructure.
The discovery process also involves tracking network connections, software dependencies, and third-party integrations that could introduce vulnerabilities. Since modern IT environments are dynamic, with frequent changes in infrastructure and software deployments, continuous asset discovery is essential to maintaining an up-to-date view of the attack surface.
Step 3: Prioritization
Not all exposures pose the same level of risk. The prioritization step evaluates identified exposures based on their potential impact and likelihood of exploitation. Organizations consider several factors, including asset criticality, known threats, adversary tactics, vulnerability severity, and business impact.
To prioritize effectively, organizations use risk-scoring models such as the Common Vulnerability Scoring System (CVSS) and contextual risk assessment frameworks that incorporate real-world threat intelligence. This step helps determine whether a vulnerability is actively being exploited in the wild or if it remains a theoretical risk.
Security teams also assess the exposure window—how long a vulnerability has been present and whether security controls already mitigate some of the risk. By ranking exposures, organizations can focus resources on addressing the most critical risks first rather than attempting to fix every minor issue.
Step 4: Validation
Validation involves testing and confirming the severity of prioritized exposures. Security teams use techniques such as penetration testing, red teaming, breach and attack simulations (BAS), and exploit proof-of-concept testing to determine whether identified risks can be leveraged by attackers in real-world conditions.
One key goal of validation is to eliminate false positives. Automated scanning tools may flag potential vulnerabilities, but not all findings represent an immediate or exploitable risk. By manually testing high-risk exposures, security teams gain a more accurate understanding of their security posture.
Additionally, validation helps refine risk assessments and improve response strategies. For example, if a vulnerability is difficult to exploit or requires extensive effort from an attacker, it may be deprioritized in favor of addressing a more easily exploitable issue. By validating exposures before remediation, organizations ensure that security efforts are directed where they are most needed.
Step 5: Mobilization
Mobilization is the final step, where organizations take action to remediate or mitigate identified exposures. This step involves applying patches, updating configurations, implementing security controls, or deploying compensating security measures to reduce risk.
Remediation strategies depend on the nature of the exposure. For example, if a vulnerability is discovered in an application, security teams may deploy a software patch. If an exposed cloud service is found, they may apply access restrictions or update security policies. In cases where immediate remediation is not possible, alternative mitigations—such as network segmentation, threat detection rules, or zero-trust architecture—can be used to reduce risk.
Beyond technical remediation, mobilization also involves coordination between IT, security, and business teams to ensure that fixes are implemented without disrupting critical operations. Organizations may also update their exposure management policies, conduct security awareness training, and refine response playbooks to improve their long-term security posture.
Free Dummies Book
External Exposure & Attack Surface Management For Dummies

As your attack surface has grown to cloud infrastructures and across subsidiaries, attackers are looking for and finding unknown and unmanaged assets to serve as their entry points.
Benefits of Exposure Management
Simpler Risk Mitigation
One of the major benefits of exposure management is that it simplifies the process of risk mitigation. By identifying and assessing all potential points of exposure, it becomes much easier to prioritize and address these risks. Instead of reacting to threats as they emerge, organizations can proactively manage their risk exposure and reduce the likelihood of a successful cyber attack.
This proactive approach not only simplifies risk mitigation but also makes it more effective. By addressing potential points of exposure before they can be exploited, organizations can prevent many cyber attacks from happening in the first place. This can significantly reduce the potential impact on the organization, both in terms of financial loss and damage to reputation.
Stronger Operational Resilience
By reducing the likelihood of a successful cyber attack, organizations can ensure that their operations are not disrupted by such attacks. This is particularly important in the modern business environment, where even a minor disruption to IT systems can have a major impact on an organization's operations.
Furthermore, by identifying and addressing potential points of exposure, organizations can also reduce the potential impact of a successful cyber attack. For instance, by implementing robust backup and recovery procedures, organizations can ensure that they can quickly recover from a cyber attack and resume operations with minimal downtime.
Tighter Regulatory Compliance
Exposure management can also help organizations achieve tighter regulatory compliance. Many regulatory bodies now require organizations to have a robust cybersecurity strategy in place, and exposure management is a key part of this. By demonstrating that they are proactively managing their cyber risk exposure, organizations can not only comply with these regulations but also avoid potential fines and penalties.
Furthermore, by complying with these regulations, organizations can also enhance their reputation among customers, partners, and other stakeholders. This can provide a competitive advantage, as customers are increasingly concerned about the security of their data and are more likely to do business with organizations that take cybersecurity seriously.
Long-Term Operational Sustainability
Finally, exposure management can contribute to long-term sustainability. In today's cybersecurity environments, organizations that fail to manage their risk exposure are unlikely to survive in the long term. Exposure management can help organizations continue to operate and thrive, even in the face of growing cyber threats.
Exposure Management Challenges
While exposure management provides a proactive approach to cybersecurity, organizations face several challenges in implementing it effectively:
- Complexity of modern IT environments: Organizations today operate in highly complex IT environments that include on-premises infrastructure, cloud services, hybrid networks, and third-party integrations. This complexity makes it difficult to maintain visibility into all potential exposures. Shadow IT, misconfigured cloud assets, and unmanaged devices can create blind spots that attackers may exploit.
- Volume of security alerts: Security teams are often overwhelmed by the sheer number of alerts generated by security tools. Many of these alerts are false positives, making it difficult to identify real threats. Without efficient prioritization and validation processes, security teams may waste valuable time on low-risk issues while critical exposures remain unaddressed.
- Rapidly evolving threat landscape: Cyber threats are constantly evolving, with attackers developing new techniques to bypass security controls. Traditional vulnerability management approaches may not be sufficient to address emerging attack vectors, such as zero-day vulnerabilities and supply chain attacks. Organizations must continuously update their exposure management strategies to stay ahead of evolving threats.
- Integration with existing security tools: Many organizations use a variety of security tools for asset management, vulnerability scanning, identity governance, and threat detection. However, integrating these tools into a cohesive exposure management framework can be challenging. Without seamless integration, security teams may struggle to correlate data from different sources and gain a comprehensive view of their attack surface.
- Regulatory and compliance challenges: Organizations must align their exposure management strategies with regulatory requirements such as GDPR, HIPAA, and NIST frameworks. However, navigating the complex and ever-changing landscape of cybersecurity regulations can be difficult. Compliance requirements often vary by industry and region, adding another layer of complexity to exposure management efforts.
Despite these challenges, organizations can improve their exposure management capabilities by leveraging automation, integrating threat intelligence, and adopting a risk-based approach to prioritization.
What Is External Attack Surface Management (EASM)?
External attack surface management (EASM) is a foundational component of exposure management, which helps organizations identify and manage risks associated with Internet-facing assets and systems. The goal is to uncover threats that are difficult to detect, such as shadow IT systems, so organizations can better understand your organization’s true external attack surface.
EASM processes, tools, and managed services can help detect threats across servers, public cloud services, credentials, and third-party partners. Ideally, an EASM solution should help identify cloud misconfigurations, software vulnerabilities, exposed credentials, shadow IT, and various other security weaknesses that threat actors can exploit.
What Does Exposure Management Involve?
Identification of Exposed Assets
The first step in exposure management is identifying all assets that could be exposed to cyber threats. This includes digital assets like servers, applications, databases, and cloud services, as well as physical assets such as hardware and network devices. The identification process should also consider shadow IT assets—those not formally managed by the IT department but still connected to the network. Comprehensive asset inventories and continuous discovery tools are crucial to ensure all potential points of exposure are accounted for.
Attack Surface Mapping
Once the exposed assets are identified, the next step is to map the attack surface. This involves creating a detailed visualization of all access points, interconnections, and potential vulnerabilities within the organization's IT environment. Attack surface mapping helps organizations understand how different assets interact and where security gaps might exist. This mapping should be dynamic, regularly updated to reflect changes in the environment, such as new deployments, updates, or configuration changes.
Risk Assessment
With a clear understanding of the attack surface, organizations can assess the risks associated with each exposure. Risk assessment involves evaluating the potential impact and likelihood of different types of cyber threats exploiting the identified vulnerabilities. This process often uses a combination of automated tools and expert analysis to assign risk scores to various exposures, helping prioritize which issues need immediate attention and which can be monitored over time.
Prioritizing Exposures
After assessing the risks, the next step is prioritizing exposures based on their risk scores. Organizations should focus on high-risk exposures that pose the greatest threat to critical assets and operations. Prioritization helps allocate resources effectively, ensuring that the most significant threats are addressed promptly. This process should also consider regulatory requirements and business priorities, aligning cybersecurity efforts with overall organizational goals.
Mitigating Exposures
Mitigation involves implementing measures to reduce or eliminate the risks associated with identified exposures. This can include applying patches to fix vulnerabilities, reconfiguring systems to enhance security, implementing access controls, and using encryption. In some cases, it might involve removing or isolating high-risk assets. Effective mitigation strategies often combine technical solutions with process improvements, such as staff training and incident response planning, to enhance overall security posture.
Continuous Monitoring
Exposure management is an ongoing process that requires continuous monitoring to detect new exposures and changes in the threat landscape. Organizations should implement automated monitoring tools that provide real-time visibility into their security posture. These tools can alert security teams to new vulnerabilities, configuration changes, or unusual activities that might indicate a new exposure. The process then repeats in identification of exposed assets, assessing and prioritizing risk, and mitigating it.

Tips from the Expert
Rob Gurzeev
CEO and Co-Founder
Rob Gurzeev, CEO and Co-Founder of CyCognito, has led the development of offensive security solutions for both the private sector and intelligence agencies.
In my experience, here are tips that can help you better enhance your exposure management strategy:
- Automate asset discovery with machine learning: Use machine learning algorithms to automate the discovery and classification of assets, including shadow IT and orphaned resources. This ensures continuous visibility and reduces the risk of overlooked exposures.
- Integrate exposure management with identity governance: Align exposure management with identity and access management (IAM) to ensure that only authorized personnel have access to critical assets. This reduces the risk of insider threats and misconfigurations that could expose sensitive data.
- Prioritize high-value asset protection: Focus your exposure management efforts on protecting high-value assets, such as intellectual property, customer data, and critical infrastructure. Use a risk-based approach to allocate resources effectively.
- Incorporate external threat intelligence feeds: Augment your exposure management platform with external threat intelligence feeds. This allows you to stay informed about emerging threats and adapt your defenses to mitigate risks before they impact your organization.
- Regularly review and update your exposure management framework: Cyber threats evolve rapidly, so it’s crucial to continuously review and update your exposure management framework. Incorporate lessons learned from incident responses and threat assessments to refine your processes and tools.
How EASM Works with Other Security Solutions to Enhance Exposure Management
Cyber Asset Attack Surface Management (CAASM)
CAASM is a security solution that mainly addresses asset visibility and exposure. Via API integrations with existing tools, organizations can view all assets (both internal and external), query consolidated data, pinpoint vulnerabilities and gaps in security controls and address them.
CAASM and EASM both strive to enhance the visibility of an organization's assets and their associated threats. However, EASM focuses purely on external assets and identifies those assets through active internet scanning. EASM can be a data source to provide external visibility within CAASM.
Application Security Testing (AST)
Application security testing focuses on tools and resources used to identify weaknesses in software applications. EASM enhances AST by automating the identification process for insecure software, including applications not actively supervised by security teams. These can be services in use by developers, but unknown to security teams, software deployed in the past and currently unused, or public code repositories. Unprotected applications and APIs can pose potential threats to companies.
Cloud Security
Cloud security solutions offer technologies to safeguard cloud-based workloads and data. EASM can empower these cloud security solutions by spotting an organization's assets across different cloud providers, thereby improving security management and governance in the cloud. This support is vital because, although cloud security solutions protect cloud properties effectively, they require organizations to be aware of their existing cloud assets.
Specifically, EASM complements Cloud Security Posture Management (CSPM) solutions. CSPM employs standard frameworks, enterprise policies, and regulatory requirements to proactively and reactively analyze and ascertain the risk/trust of cloud service configurations and security settings. In combination with EASM, CSPM can be used to protect cloud assets wherever they are deployed, even without the knowledge or permission of the organization.
Threat Intelligence (TI) and Digital Risk Protection Services (DRPS)
DRPS helps to keep an eye on the surface web, deep web and dark web to detect potential threats to pivotal digital assets. It gives a detailed picture of how threat actors operate and the tactics they employ.
DRPS is mainly focused on threats to company's brands, customer information, data, and executives, preventing fraud, theft and impersonation attempts, while EASM has a wider asset discovery capability. Combining EASM and DRPS provides a more comprehensive overview of a company's digital assets and associated risks.
Vulnerability Management Platforms
Vulnerability management platforms find, classify, prioritize, and coordinate the resolution or reduction of security issues in assets managed by the organization. EASM supplements vulnerability management by identifying risks deriving from an organization’s internet-visible assets and systems, including those that may not be well-managed by the organization or undiscovered.
Best Practices for Exposure Management
Here are a few best practices for implementing exposure management in your organization:
- Encourage collaboration across departments, to enable faster, more informed decisions and more effective response to newly discovered threats.
- Centralize data from across the organization. This helps spot trends, weak-spots, and concealed threats that might evade detection in isolated data silos.
- Focus on severe vulnerabilities, using EASM capabilities to prioritize vulnerabilities by their potential impact. This ensures you allocate resources to the most important risks.
- Use metrics for continuous improvement. Metrics such as time to detection (MTTD), mean time to repair (MTTR), and time to mitigate (TTM) can help assess and improve the value of the EASM solution and integrated technologies.
Cyber Exposure Management with CyCognito Attack Surface Management Platform
The CyCognito platform addresses today’s vulnerability management requirements by taking an automated multi-faceted approach in identifying critical issues based on their business impact rather than focusing on the generic severity of the threat alone. To do this, you need a platform that continuously monitors the attack surface for changes and provides intelligent prioritization that incorporates organization's context.
The CyCognito platform addresses today’s vulnerability management requirements by:
- Maintaining a dynamic asset inventory with classification of the entire external attack surface, including exposed on-premise and cloud-hosted assets like web applications, IP addresses, domains and certificates, eliminating the need to rely on outdated or incomplete information from collaboration tools, spreadsheets, or emails. This approach significantly reduces the burden of tedious, error-prone and costly processes.
- Actively tests all discovered assets to identify risk. Active testing, including dynamic application security testing, or DAST, uncovers complex issues and validates known issues, with low false positives. Each exploited asset is assigned a security grade based on its criticality to the business.
- Prioritizing critical issues, guiding security teams to focus on the most urgent threats. Our unique risk-based prioritization analysis goes beyond the common vulnerability scoring system (CVSS), and incorporates factors like asset discoverability, asset attractiveness, exploitability, business impact and remediation complexity. Integrated tactical threat intelligence identifies the handful of attack vectors that pose the greatest risk.
- Streamlining communications between remediation teams by providing comprehensive, verifiable evidence for each exploited asset. This evidence includes detailed risk assessments, asset ownership information, and actionable remediation guidance. The platform seamlessly integrates with SIEM, SOAR and ticketing system tools like Jira, ServiceNow and Splunk to facilitate information sharing and collaboration.
Learn more about CyCognito Attack Surface Management.
See Additional Guides on Key Data Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of data security.
Object Storage
Authored by Cloudian
- [Guide] What is Object Storage: Definition, How It Works and Use Cases
- [Guide] Object Storage vs. File Storage: What's the Difference?
- [Product] Cloudian | Enterprise-Class, S3-Compatible Object Storage Software
Splunk Architecture
Authored by Cloudian
- [Guide] Splunk Architecture: Components and Best Practices
- [Guide] Splunk Data Analytics: Splunk Enterprise or Splunk Hunk?
- [Whitepaper] TCO Report: Cloudian HyperStore File
- [Product] HyperStore Object Storage
PostgreSQL
Authored by Instaclustr
Free Dummies Book
External Exposure & Attack Surface Management For Dummies

As your attack surface has grown to cloud infrastructures and across subsidiaries, attackers are looking for and finding unknown and unmanaged assets to serve as their entry points.
 White Paper
White Paper