What Are DAST Tools?
Dynamic Application Security Testing (DAST) tools are software testing tools used to identify security vulnerabilities in a web application during runtime. They are designed to analyze your application in a realistic environment, interacting with the web interface just like an attacker would, and attempting to find exploitable vulnerabilities. DAST tools do not need access to the application’s source code, which also means they are language- and platform-agnostic.
DAST tools play a critical role in the software development lifecycle, particularly in the testing phase, where they help to identify and rectify security vulnerabilities before the application is deployed. This not only helps to ensure the security of production applications, but also saves time and resources, because vulnerabilities can be remediated earlier in the development lifecycle.
This is part of a series of articles about application security.
Features of DAST Tools
Black-Box Testing Approach
DAST tools use a black-box testing approach. Unlike white-box testing, where the tester has complete knowledge of the application’s source code, black-box testing involves testing the application without knowledge of its internal workings. This approach mirrors the situation of an attacker who identifies and exploits vulnerabilities without access to the application’s source code.
DAST scans can be unauthenticated, meaning they simulate a user who does not have access credentials for the target web application. They can also be run in authenticated mode, to simulate an attacker who has taken over a user account, and see what vulnerabilities are exposed in this state.
Detection of Runtime Issues
While static testing tools analyze the application’s source code for potential vulnerabilities, DAST tools take it a step further by examining the application during its operation. This allows them to identify issues that might not be visible in the source code but could become apparent during the application’s runtime.
This is particularly beneficial in identifying vulnerabilities related to user inputs, session management, misconfigurations, and data leakage. By simulating user behavior and examining the application’s responses, DAST tools can identify weaknesses that could be exploited by attackers to gain unauthorized access or extract sensitive information.
Crawling and Attack Simulation
Crawling involves systematically navigating through the application’s web interface to identify possible entry points. Once these entry points have been identified, DAST tools then simulate a variety of attacks to check for weaknesses.
This combination of crawling and attack simulation provides a comprehensive assessment of the application’s security by exploring every visible aspect of the application and testing each surface for vulnerabilities.
Severity Assessment and Reporting
Once a weakness has been identified, DAST tools categorize it based on its potential impact. This helps developers prioritize their remediation efforts and focus on the most critical vulnerabilities first.
In addition to severity assessment, DAST tools also generate detailed reports of their findings. These reports include information about the identified vulnerabilities, their potential impact, and recommendations for remediation. This helps developers understand the issues and provides a clear roadmap for fixing them.
Benefits of DAST tools
Here are some of the benefits of DAST tools for development and security teams:
- Low false positives, high precision: False positives, or instances where a tool incorrectly identifies a vulnerability, can be a significant drain on resources as they require unnecessary investigation and remediation efforts. DAST tools minimize the occurrence of false positives because they actively validate exposed vulnerabilities.
- Can be run frequently: DAST can enable realistic security testing throughout the software development lifecycle, as soon as the application is deployed to a staging environment. By identifying and fixing vulnerabilities in early testing stages, DAST tools help to reduce the cost and time required for remediation.
- Detection of complex risks: DAST tools are effective in detecting complex security risks such as SQL Injection (SQLi), Cross-Site Scripting (XSS), and use of default admin credentials.
- Detection of business logic attacks: DAST tools are capable of detecting business logic attacks, which involve exploiting flaws in the normal functioning of an application to carry out unauthorized activities. These attacks can be particularly difficult to detect as they do not involve code injection or manipulation.
Tips from the Expert

Dima Potekhin, CTO and Co-Founder of CyCognito, is an expert in mass-scale data analysis and security. He is an autodidact who has been coding since the age of nine and holds four patents that include processes for large content delivery networks (CDNs) and internet-scale infrastructure.
In my experience, here are tips that can help you better leverage DAST tools in your security strategy:
- Use DAST in pre-production and production environments: While DAST is typically used in pre-production, running it against production environments (with proper precautions) can uncover configuration issues and vulnerabilities missed earlier.
- Perform out-of-band testing: Many vulnerabilities, like certain SSRF (Server-Side Request Forgery) attacks, might not manifest in direct responses. Implement out-of-band techniques with your DAST tools to catch these hidden threats.
- Monitor and adapt to application changes: DAST tools should be reconfigured to adapt to significant application updates or architecture changes. Ensure scans reflect the latest application state to avoid missing new attack surfaces.
- Use parallel testing in complex applications: Break down large applications into segments and run DAST scans in parallel. This approach can significantly reduce the time to detect vulnerabilities across complex, large-scale applications.
- Exploit chaining: Instead of looking at each vulnerability in isolation, consider the possibility of chaining multiple low-risk vulnerabilities identified by DAST to execute a more impactful attack.
These tips aim to optimize the effectiveness of DAST tools, ensuring a robust security posture for your applications.

2024 State of Web Application Security Testing
Are you confident your web application security measures are keeping pace with evolving threats?
Discover how your web app security compares. Learn about average testing frequency, the prevalence of web application security incidents and breaches, and the increasing adoption of automation to improve testing efficiency.

Notable DAST Tools
1. CyCognito
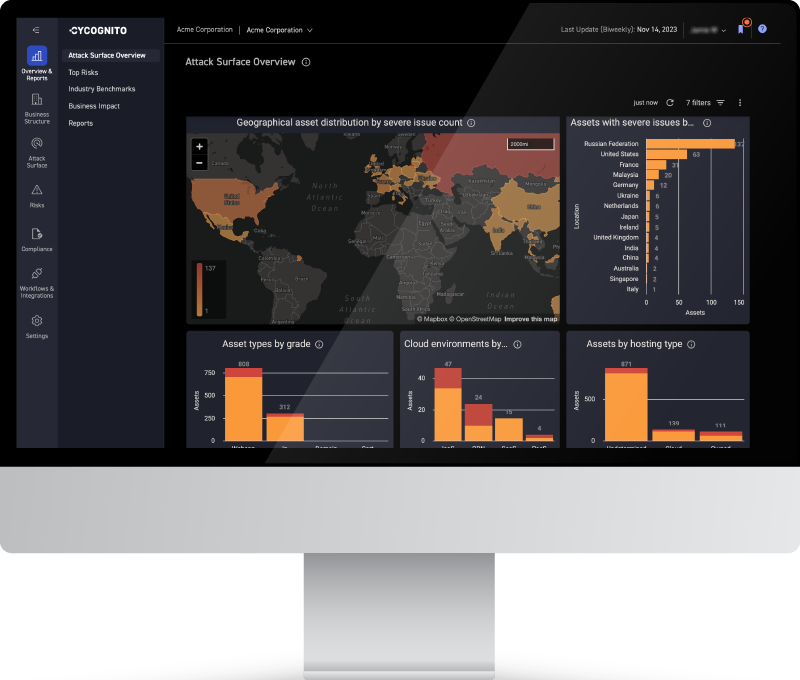
The CyCognito platform continuously conducts tens of thousands of active security tests, including DAST, across all exernally-exposed web applications, to uncover complex issues and validate known issues. This includes risks such as active injection vulnerabilities, default credentials, sensitive exposed data, vulnerable Javascript libraries, vulnerable content management systems (WordPress, Joomla, etc.) and more.
Combined with the CyCognito platform’s asset inventory – built to uncover both organizational business structure and the assets within it – it ensures IT security teams have the information they need to remediate issues efficiently. This enables organizations to expand security testing coverage (often from less than 10% of internet exposed assets) to greater than 90%.
2. Invicti (formerly Netsparker)

Source: Invicti
The Invicti DAST scanner is designed to identify vulnerabilities in websites and web applications. It offers automated application discovery, and integrates with CI/CD solutions and issue management systems. It can function as a desktop application, a server installed in an on-premise data center, or a managed service. Upon discovering a vulnerability, the Invicti scanner produces a “proof of exploit”, which can reduce false positives.
3. Acunetix
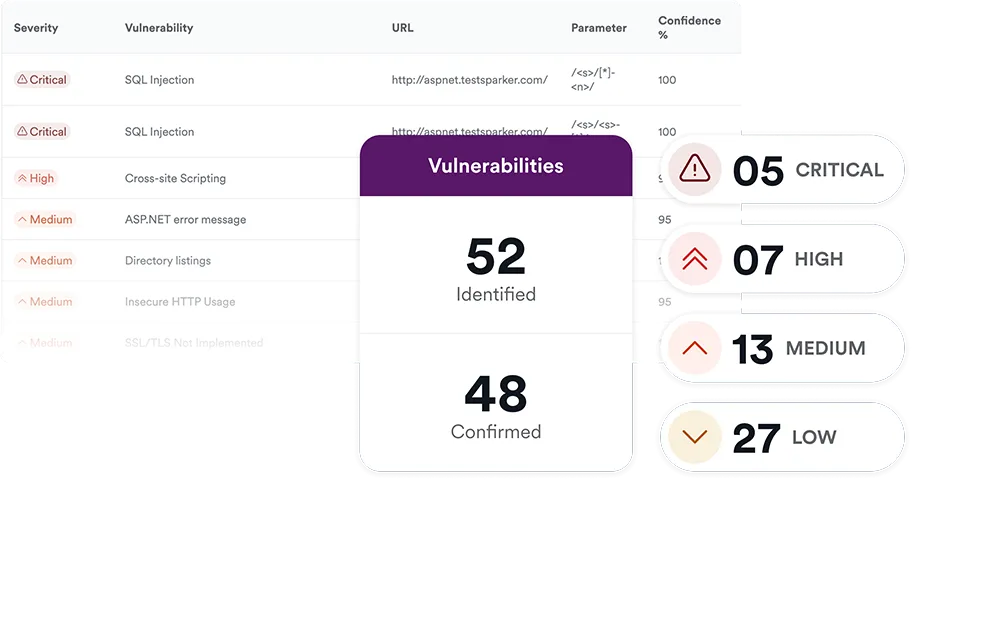
Source: Acunetix
Acunetix is a web application security tool that can identify more than 7,000 security weaknesses, including exposed databases, misconfigurations, and SQL injection. It integrates with CI/CD, issue trackers, and web application firewalls (WAFs). Acunetix combines Dynamic (DAST) and Interactive (IAST) application security testing, enabling a gray-box testing approach. It can automatically discover a business’s APIs, applications, and websites. The tool can effectively test single-page applications, websites with extensive JavaScript and HTML5 scripting, and password-protected zones.
4. ZAP
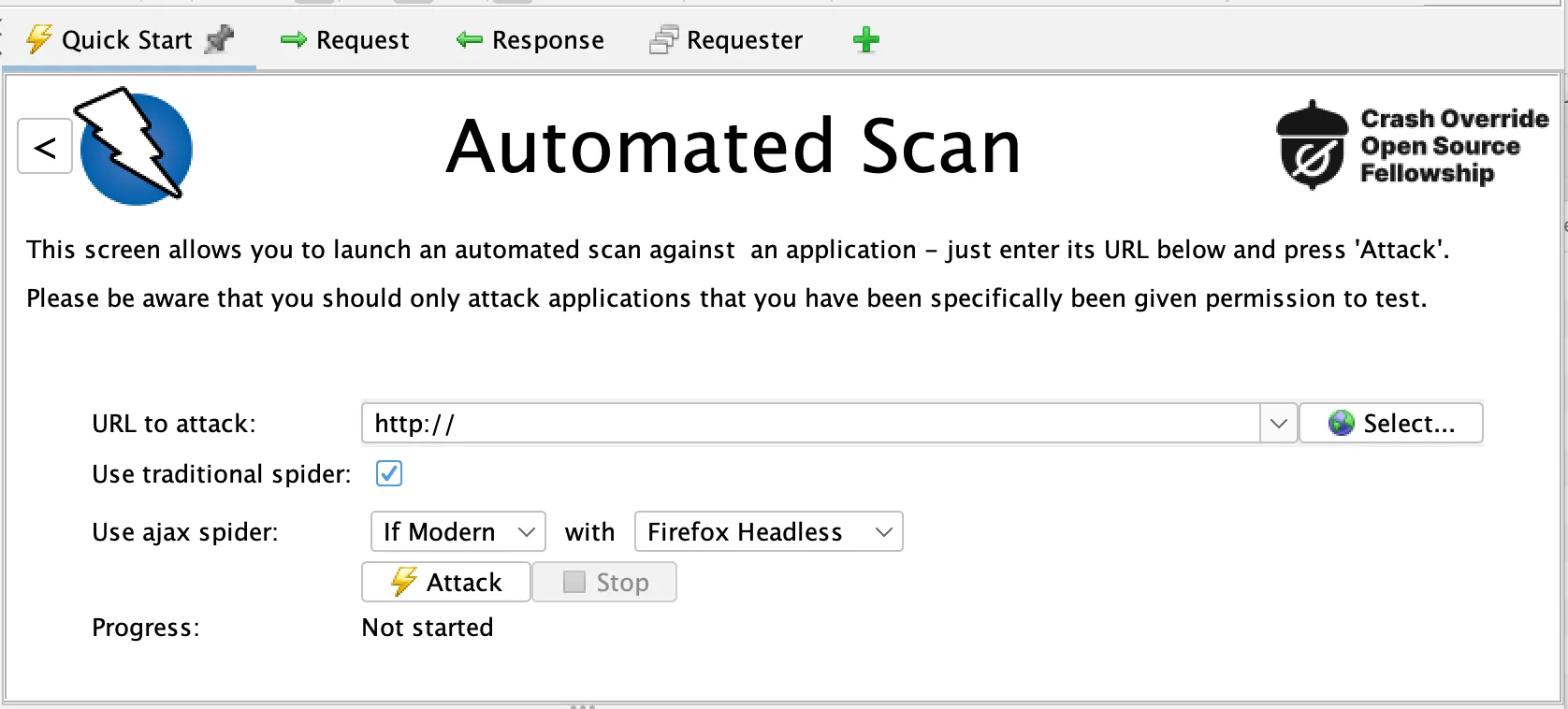
Source: ZAP
ZAP is a free DAST tool, originally developed by OWASP and now a standalone open source project. It includes various components like spiders for crawling web applications to discover new URLs, and a proxy server for observing and manipulating the traffic between the browser and the web application. This functionality is particularly useful for understanding and testing how user inputs are handled and how sessions are managed.
ZAP provides a set of scanners to detect vulnerabilities like SQL Injection, Cross-Site Scripting (XSS), and many other common security flaws. Additionally, it supports a range of scripts and plugins, allowing customization and extensibility to fit specific testing needs. It can also be integrated into CI/CD pipelines for automated security testing.
5. Rapid7 InsightAppSec
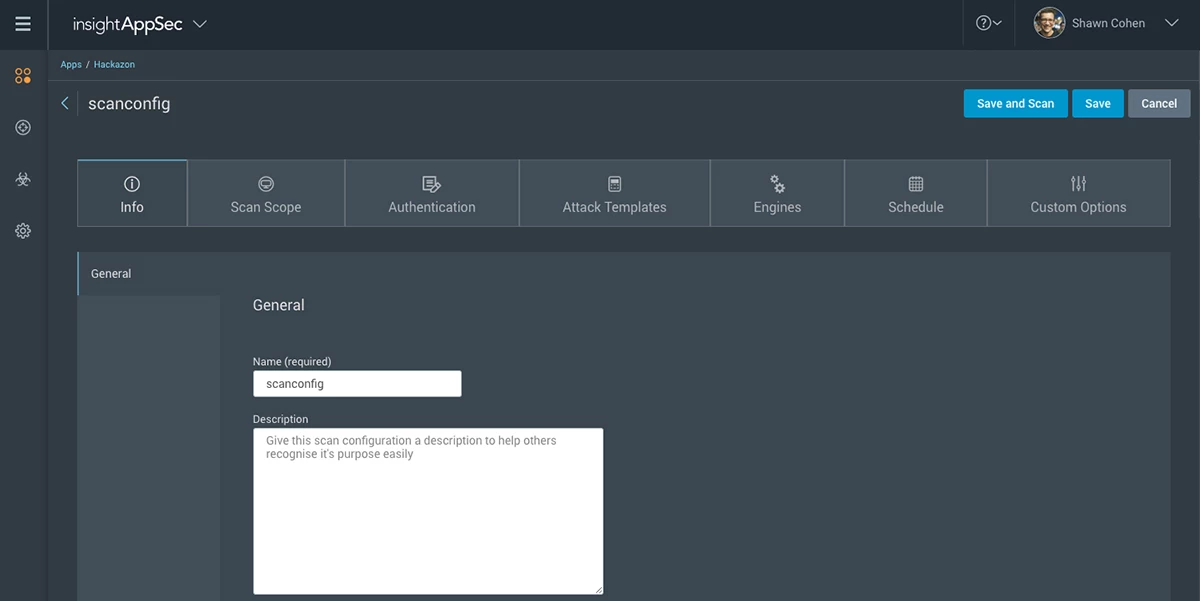
Source: Rapid7
Rapid7 InsightAppSec is a platform that aims to integrate security into the entire software development lifecycle. As part of the platform, it provides DAST scans to detect and remediate vulnerabilities in web applications. A key feature is its universal translator technology, which standardizes how data is rendered and analyzed, enhancing the accuracy of vulnerability detections. InsightAppSec also provides an interactive query language (IQL) for customized reporting and analytics.
6. Tenable Web App Scanning
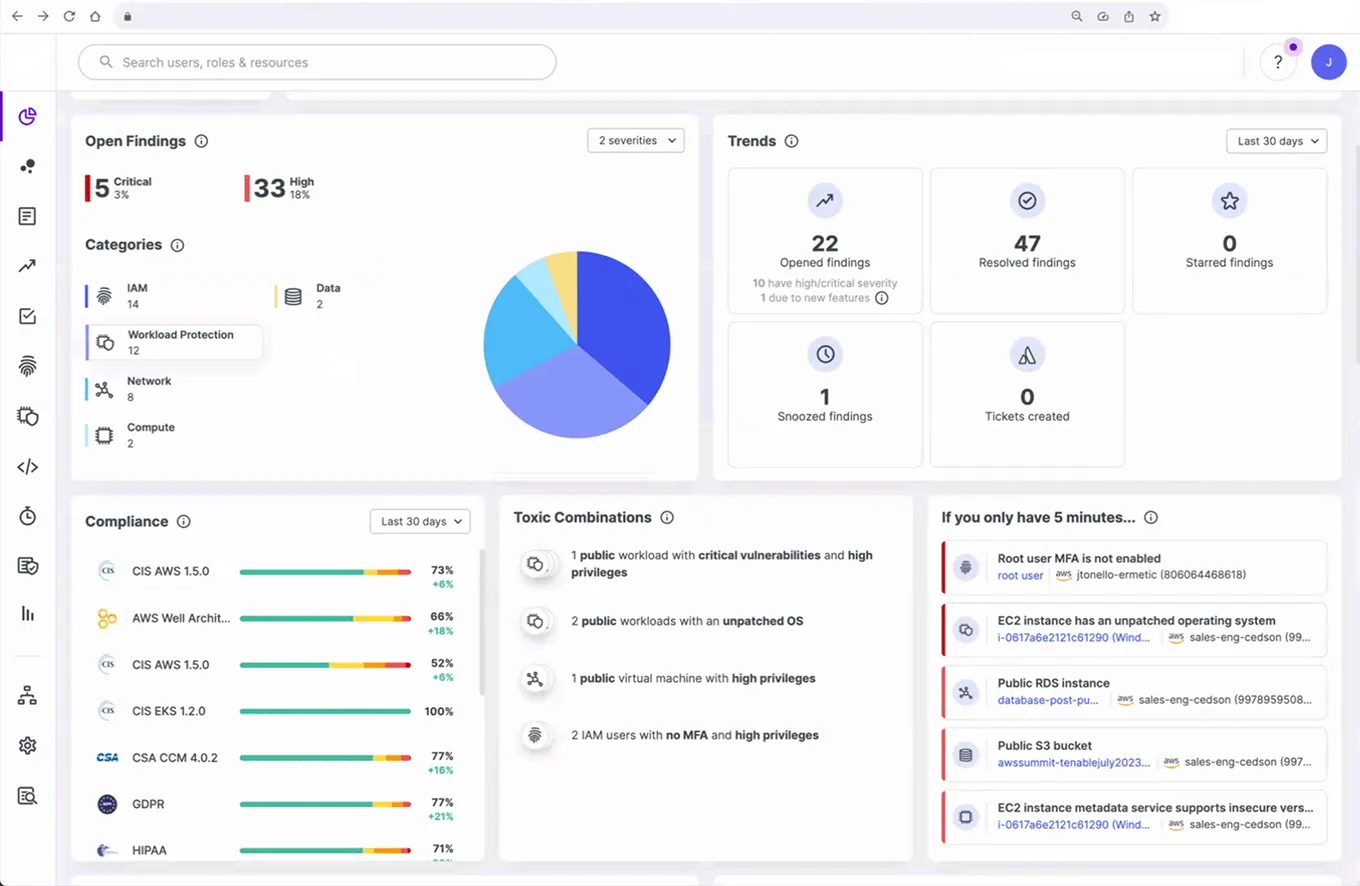
Source: Tenable
Tenable Web App Scanning, part of the Tenable.io platform, is a DAST solution designed to identify vulnerabilities in web applications. Key features of Tenable Web App Scanning include its ability to accurately scan modern web applications, including those that heavily rely on JavaScript and AJAX frameworks. It is effective in identifying a variety of vulnerabilities, including OWASP Top 10 risks, misconfigurations, and other web application weaknesses.
Tenable Web App Scanning supports integration with other Tenable products and various DevOps tools, enabling organizations to embed security into their continuous integration and delivery pipelines.
7. Qualys Web Application Scanning
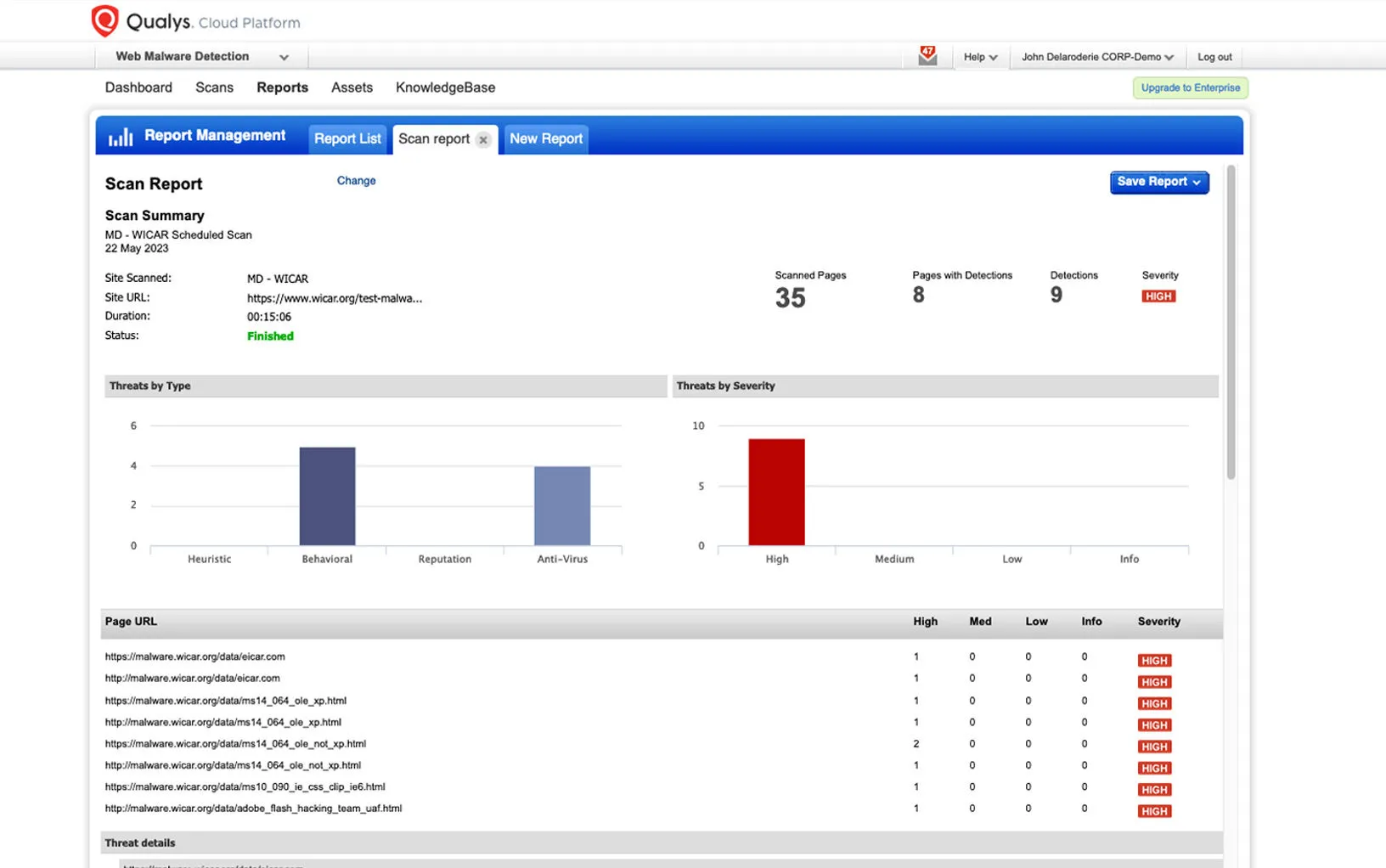
Source: Qualys
Qualys Web Application Scanning (WAS) offers automated DAST scanning for web applications and REST APIs to identify vulnerabilities. It covers a broad range of security issues, from OWASP Top 10 risks to out-of-date libraries. Qualys WAS is highly scalable and can perform consistent, repeatable scans across a large number of applications. The tool offers a progressive scanning feature, which means it can learn from previous scans to optimize future ones.
8. w3af
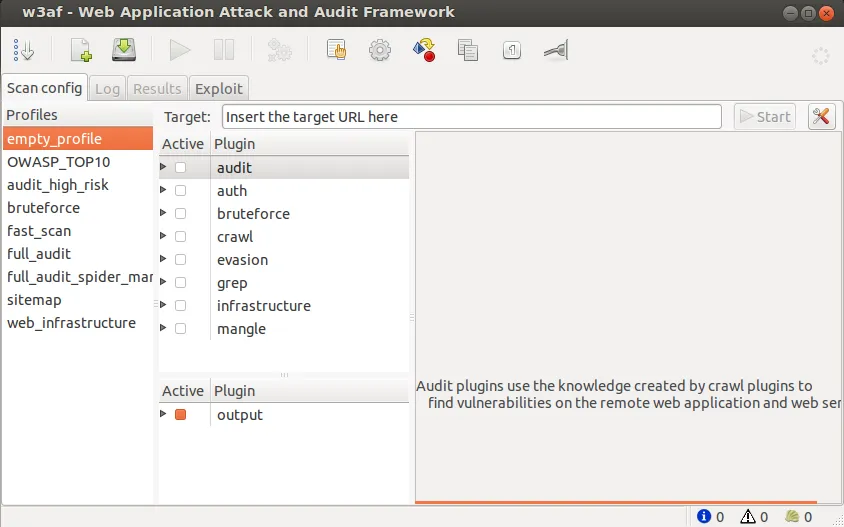
Source: w3af
w3af is a popular open source web application attack and audit framework, written in Python. It was designed as a penetration testing platform for web applications. It is able to identify and automatically exploit more than 200 kinds of web application vulnerabilities, including SQL injection and cross-site scripting.
9. Detectify
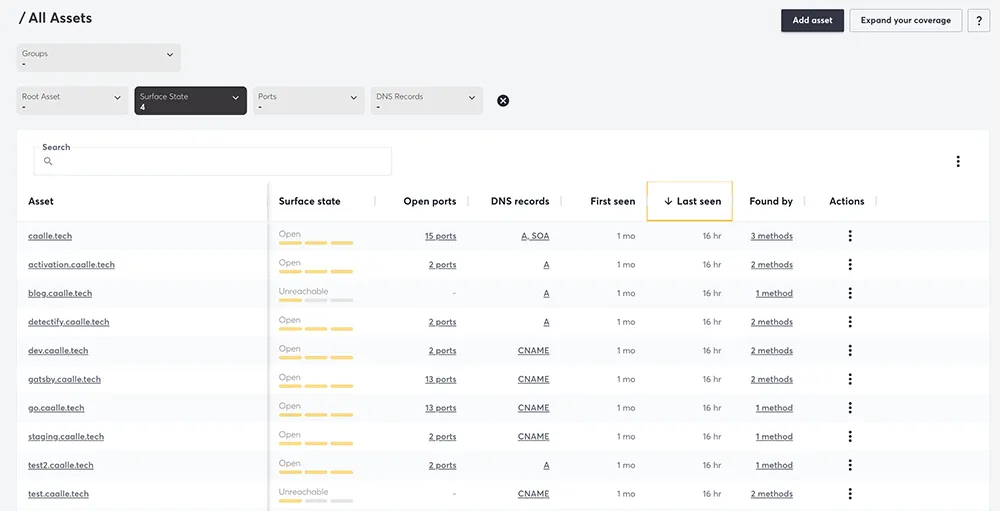
Source: Detectify
Detectify encodes the knowledge of ethical hackers into a scalable, continuous scanning tool. It performs external scans to detect over 1500 vulnerabilities, including those listed in the OWASP Top 10. One of its key features is the ability to integrate the latest research findings, from its network of ethical hackers. It excels in identifying misconfigurations, subdomain takeovers, and content management system (CMS) vulnerabilities.
Conclusion
In conclusion, Dynamic Application Security Testing (DAST) tools represent an essential component in safeguarding web applications from various security threats. By simulating real-world attack scenarios, these tools effectively identify vulnerabilities during runtime, without the need for source code access. This makes them versatile and applicable across different languages and platforms.
The key strengths of DAST tools lie in their black-box testing approach, the ability to detect runtime issues, and comprehensive crawling and attack simulation capabilities. They offer precise vulnerability detection with low false positives, making them a reliable resource in the software development lifecycle. Furthermore, DAST tools facilitate an earlier integration of security testing, thus promoting a proactive stance in vulnerability management.
The market offers a range of DAST tools, each with unique features and capabilities. We reviewed several popular options, which provide developers and security teams with the necessary insights to address vulnerabilities effectively, enhancing the overall security posture of web applications. As cyber threats become more sophisticated, the role of DAST in maintaining robust application security will continue to grow, making these tools a vital asset for any organization focused on safeguarding its web applications.
Learn more about the CyCognito Attack Surface Management Platform

2024 State of Web Application Security Testing
Are you confident your web application security measures are keeping pace with evolving threats?
Discover how your web app security compares. Learn about average testing frequency, the prevalence of web application security incidents and breaches, and the increasing adoption of automation to improve testing efficiency.














