



The effects of a cyber-attack are becoming increasingly difficult to predict and control due to the fact that cybercriminals are constantly developing new and sophisticated techniques to exploit vulnerabilities and gain access to systems and today’s systems are highly interconnected.
CyCognito Exploit Intelligence provides threat intelligence on actors in the wild that can be used to prioritize issues by providing insights into the adversary's capabilities, motivations, and tactics. This information can be used to identify the most significant threats to your organization and provide prescriptive and intelligent remediation guidance with supporting evidence so that organizations can focus their resources on the most critical threats and vulnerabilities and improve their overall security posture.
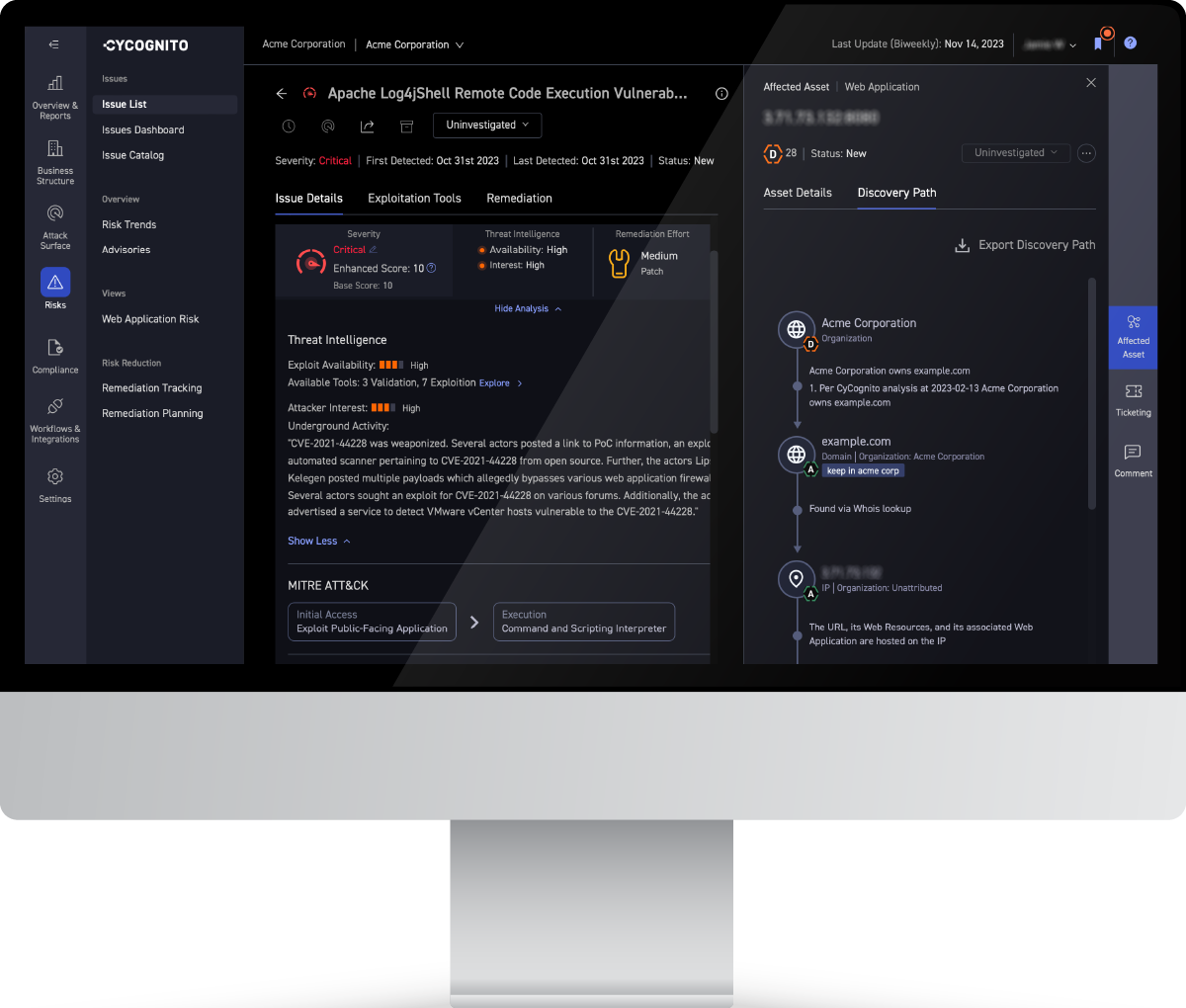
Experience how CyCognito integrates targeted threat intelligence to enhance the results of active testing. Explore Exploit Intelligence features like the dedicated threat intelligence advisory dashboard and easy-to-use validation instructions that speed research and remediation efforts.
CyCognito's Exploit Intelligence gives you a unique perspective on threat actors' tactics, techniques, and procedures (TTPs). Use this information to see your external attack surface from an attacker's point of view, so you can protect against common TTPs. Exploit Intelligence also provides intelligence on evolving tactics, enabling you to proactively respond to threats before they materialize.
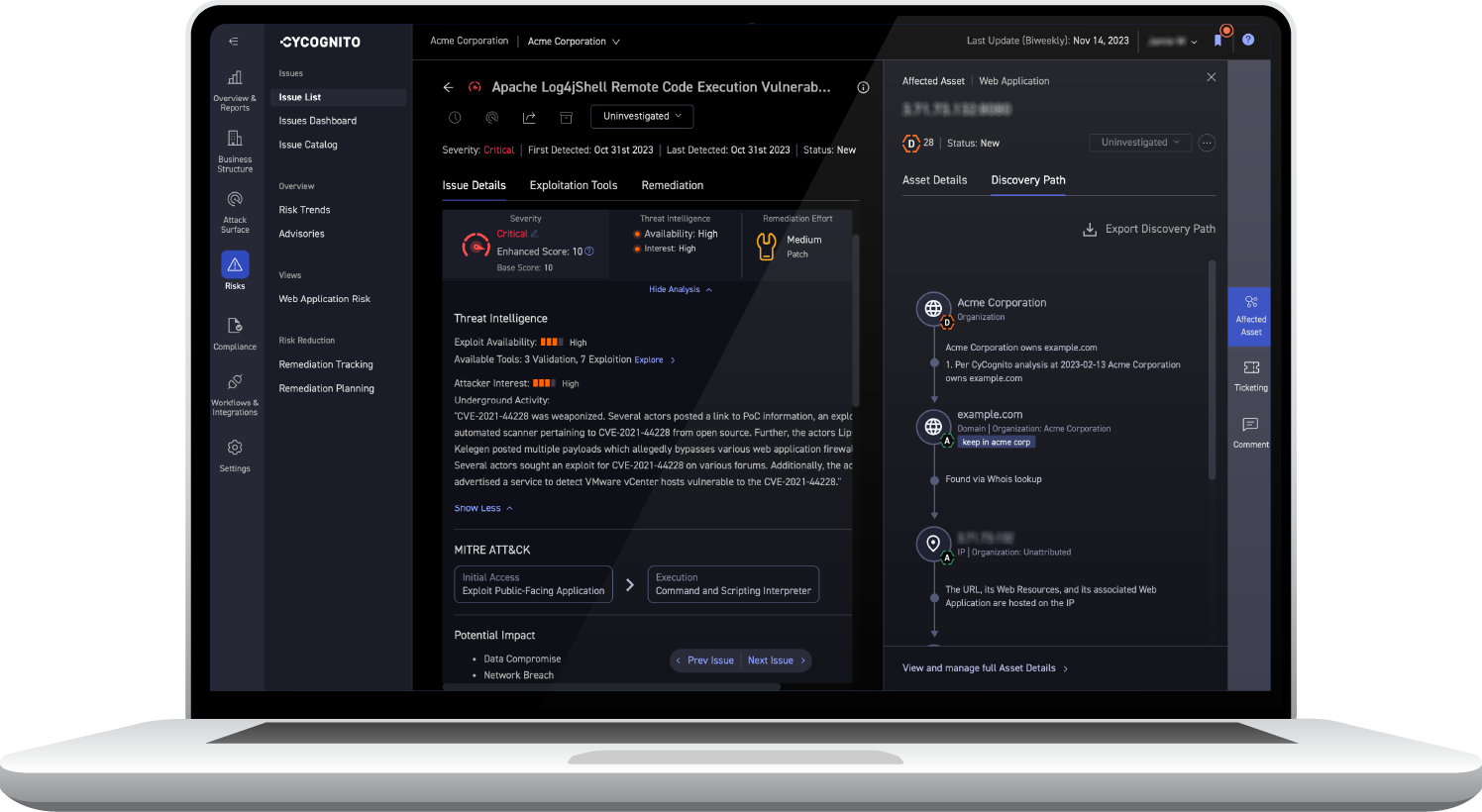
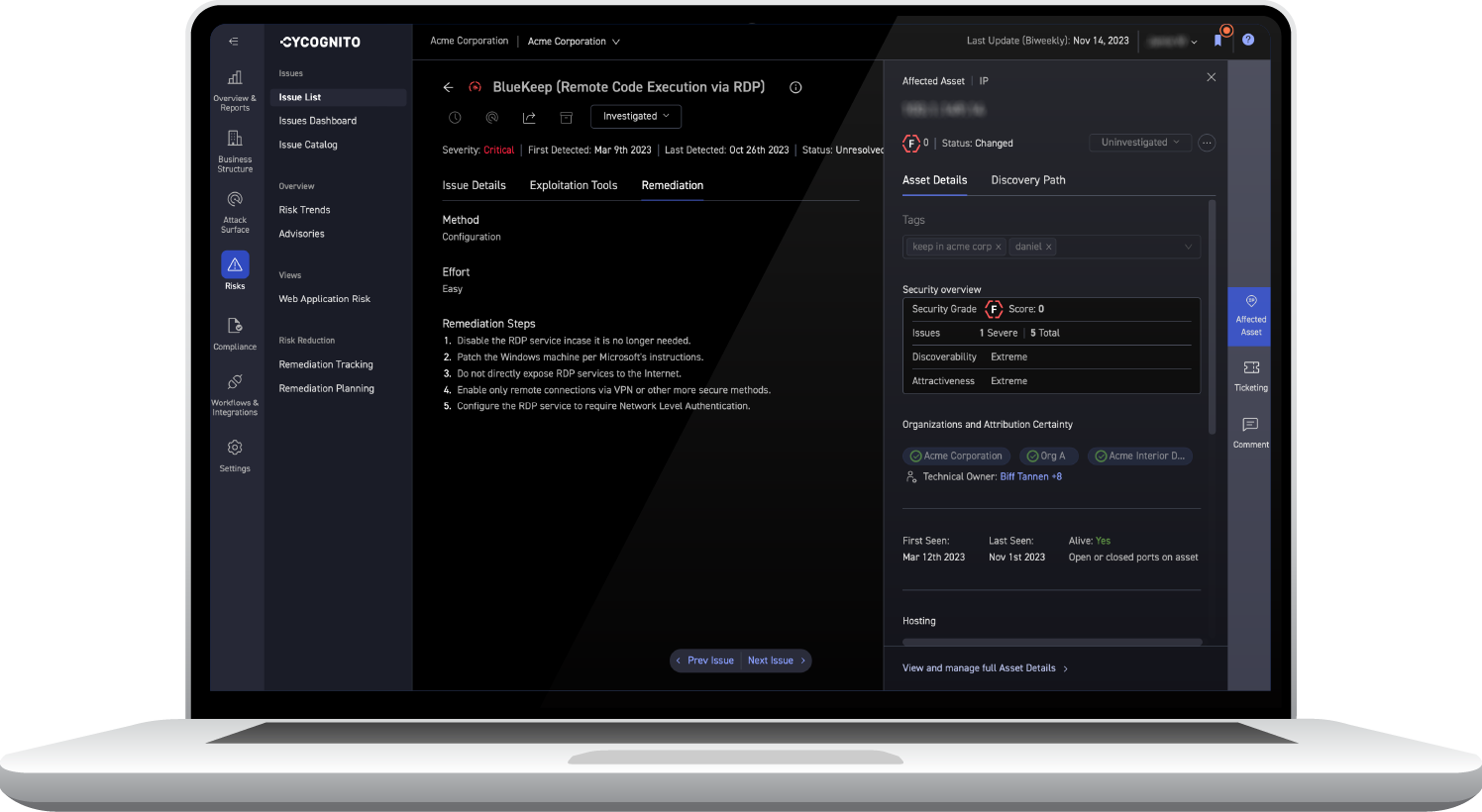
Exploit Intelligence provides strategic prioritization to address the vulnerabilities that pose the most significant risk to your organization. Once issues are prioritized, CyCognito provides step-by-step instructions for simulating exploits, as well as remediation guidance. This information can be shared with resolution teams through integration with the tools they use, helping to accelerate the remediation process.
Cybersecurity advisories provide the latest data and strategies on vulnerabilities being exploited in the wild. Cycognito's Exploit Intelligence helps you understand how these advisories impact your organization's attack surface by tagging assets that are vulnerable, and those that are not. When asked if your organization is impacted by a new threat, you can immediately share this information with your stakeholders.
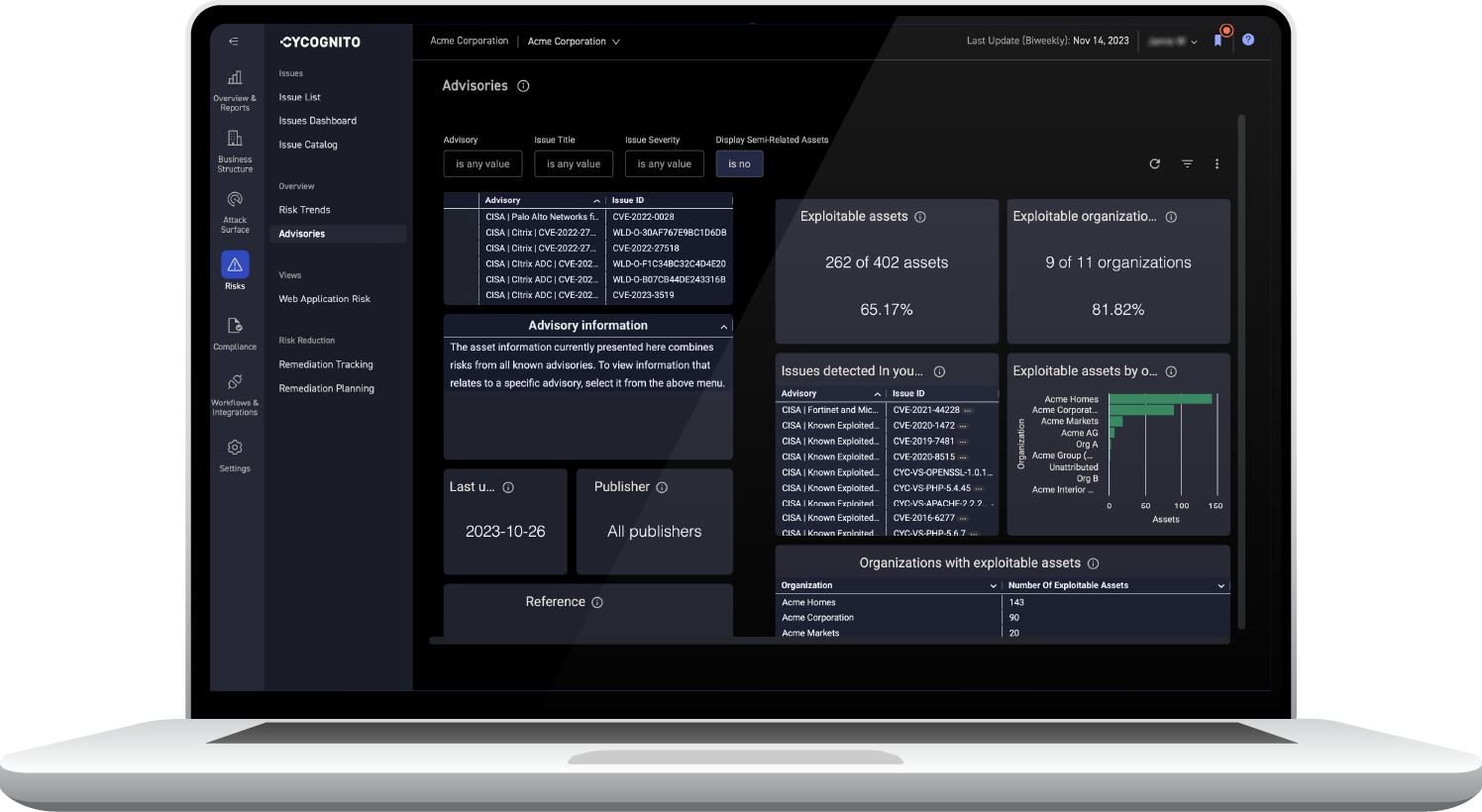
The CyCognito platform’s Exploit Intelligence capability gives teams all they need to perform comprehensive security testing and attack exercises.
Learn the strengths of Exploit Intelligence and compare them against traditional threat intelligence platforms.
Close your security gaps with CyCognito's zero-input discovery, automated testing, and risk-based prioritization of your attack surface.
Answer a few questions and receive an instant custom report sharing how you can reduce costs and boost your efficiency with CyCognito.
Learn more about key cybersecurity topics and how CyCognito addresses the challenges of managing risk across your external attack surface in the resources below.

Threat intelligence can feel like a firehose of data to security teams who are already struggling to keep their heads above water patching, fixing and hardening networks.
 DRPS
DRPSA digital risk protection service (DRPS) offers visibility and defense against cybersecurity threats to an organization's digital attack surfaces.

Equipping defenders with exploit intelligence is a way CyCognito helps defenders learn the offensive security side of things.
 Vulnerability Assessment
Vulnerability AssessmentVulnerability assessment is the process of identifying, quantifying, and prioritizing vulnerabilities in a system.