A series of exposed MOVEit Transfer vulnerabilities have affected 520 organizations and over 32 million individuals. This post reviews what we know to date about the vulnerabilities and then describes how organizations can use CyCognito to understand and remediate their exposure.
MOVEit Transfer, a product of software company Progress, is used by many companies to share sensitive information and adhere to regulatory compliance standards. Rather than using email, companies use MOVEit Transfer to securely share large troves of very sensitive data.
The victims of these exploited risks include well-known brands like PWC, Ernst & Young, SONY and Johns Hopkins University. Other victims were compromised because they were customers of a hacked vendor, including the BBC, British Airways, Aer Lingus, and the popular UK-based retailer Boots. These organizations were affected when popular payroll service provider Zellis was hacked through a MOVEit exploit.
The Exposed Risk and Exploited Victims
Impacted versions of MOVEit Transfer are vulnerable to Structured Query Language (SQL) injection attacks. SQL injection attacks are common enough that they consistently remain on the OWASP Top 10 list of web application security risks. Essentially, an application with this type of vulnerability is susceptible to an attacker inputting a nefarious command (the injection) that will allow the attacker to view, alter, or steal information on that application. In the case of MOVEit Transfer, it would be sensitive data customers were expecting to be tightly secured.
NIST identified five CVEs related to this incident: CVE-2023-34362, CVE-2023-35708, CVE-2023-36932, CVE-2023-36933, and CVE-2023-36934. Three of the vulnerabilities can be exploited externally, without any necessary authentication to the MOVEit application. Progress has issued patches for the five vulnerabilities, but organizations that have not yet applied the patches across all instances are still at risk.
An SEC 8-K filing by Maximus, a government contractor that manages programs like Medicare and Medicaid, called the MOVEit exploit a “critical zero-day vulnerability.” As a result of an investigation with forensic and data experts, the organization believes hackers obtained Social Security numbers, protected health information (PHI) and other personal information of at least 8 to 11 million individuals.
Who is Responsible and What’s Their Motive?
The Russian-speaking ransomware gang CL0P has claimed responsibility for the MOVEit hacking spree, which dates back to May 2023 and continued through June.
“This is crime as a service, it’s organized crime” as described by CyCognito’s CSO, Anne Marie “AMZ” Zettlermoyer on a recent Cyber Ranch Podcast. On the podcast, AMZ explained “this was not necessarily a destructive attack but it is highly espionage since it is data and not necessarily systems that could be shut down or used to harm.” She went on to explain that given the type of information that’s at risk, the attackers could have any number of motives, including financial gain, espionage, or embarrassment. Researchers believe that extortion is the motive in the MOVEit campaign and that it may end up impacting over 1,000 companies. And while very few victims may end up paying a ransom, the CL0P gang may ultimately extract $75-100 million dollars through this attack campaign.
The Recovery and Perspective
According to the 8-K filing from Maximus, it expects the investigation and remediation of this MOVEit-related incident will cost an estimated $15 million.
On the previous mentioned podcast, AMZ’s focus was on “reasonableness of care” when it comes to the difficult task of cleaning up from a breach. She described this standard with an example.
“If you have a critical vuln that’s exposed to the internet and you haven’t patched that within a period of time that is acceptable,” AMZ explained, “then that’s something you are going to have to answer to.” She continued, “it’s more about response and making sure you know you weren’t sloppy, you weren’t cutting corners, you weren’t saying, ‘you know, I’m not investing in security, I don’t care what my attack surface looks like.’”
Most organizations, as AMZ described, are trying to do the right thing and it’s a matter of assessing your risk tolerance and how to move forward, especially for those who have been breached. Even if you just realized you had MOVEit in your organization but were not exposed, it’s fair to reassess your risk tolerance. This could mean setting a goal of reducing your team’s response time from 30 to 15 days or acknowledging and resolving a blind spot in your attack surface.
Cleaning Up and Taking Action
Ernst & Young “immediately launched an investigation” into their use of the MOVEit Transfer product and “took urgent steps to safeguard any data.” They also stated that they are “manually and thoroughly investigating systems where data may have been accessed.”
Some might wonder, “how can I be sure I know everywhere MOVEit is being used at my organization?” This is where the CyCognito platform comes in; it helps you understand your entire external attack surface and identify where you have exposed risks.
The CyCognito platform helps customers to find where MOVEit Transfer is being used across their attack surface, including by subsidiaries, branch offices and other related parts of the business. If CyCognito finds an exposed risk, the platform provides easy-to-understand details about the version and provides guidance to remediate the issue. Users can easily understand how the instance of MOVEit transfer was discovered and which part of the business it belongs to.
CyCognito’s Response & Finding MOVEit-Exposed Risks
CyCognito alerted customers to the MOVEit vulnerability through an in-platform announcement in addition to other direct contact methods. This alert (Figure 1 below) also provided easy access for users to find assets across their attack surface.
Figure 1: The alert sent by CyCognito for the MOVEit Transfer series of vulnerabilities.
The CyCognito platform uses both passive scanning and active testing to assess the vulnerability of assets. Passive scanning will scan for fingerprints of known vulnerabilities including the CVEs related to MOVEit. The vulnerable versions of MOVEit are susceptible to SQL injection attacks. CyCognito’s active security testing deploys payloads tailored to system, services and operating systems to validate the exploitability of the vulnerability. These tests, which discover attack vectors including SQL injection and Cross Site Scripting (XSS), are designed for minimum impact and interaction. In the case of a vulnerability like the ones impacting MOVEit, CyCognito’s active security testing validates the SQL injection vulnerabilities.
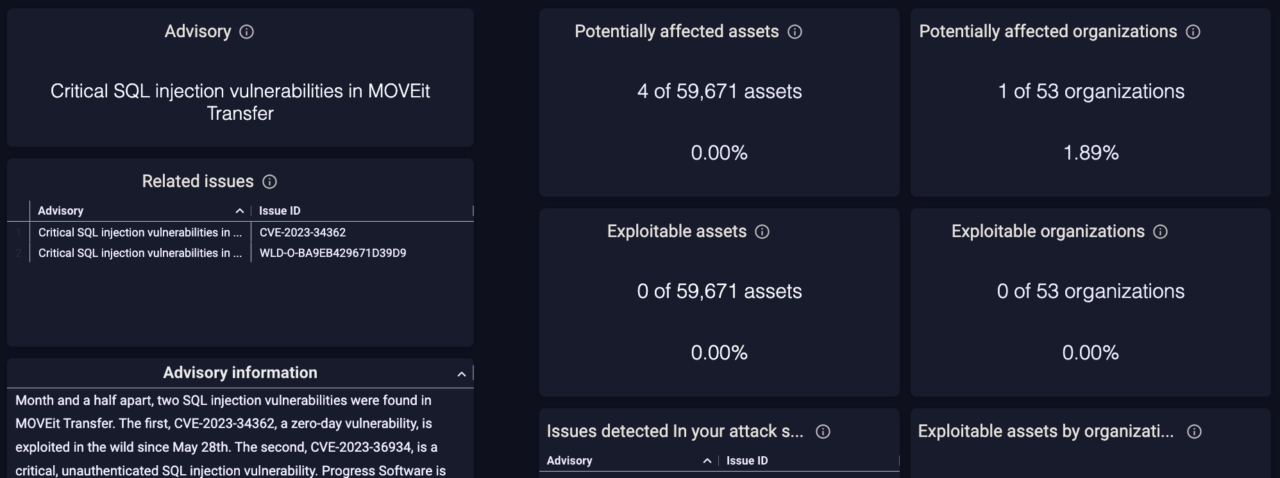
The CyCognito platform displays important contextual information, including the date the issue was discovered, an impact analysis including the criticality and effort for remediation. Users can verify the findings by looking at the evidence provided with the version number and more. Figure 2 below shows the results of this testing – users see which assets are potentially vulnerable, how many subsidiaries have potentially vulnerable assets, and whether these assets are actually in danger of being exploited.
Figure 2: CyCognito’s Advisory dashboard shows the number of subsidiaries in an organization that have MOVEit in their environment (top left), even if the specific instances are not exploitable (bottom center).
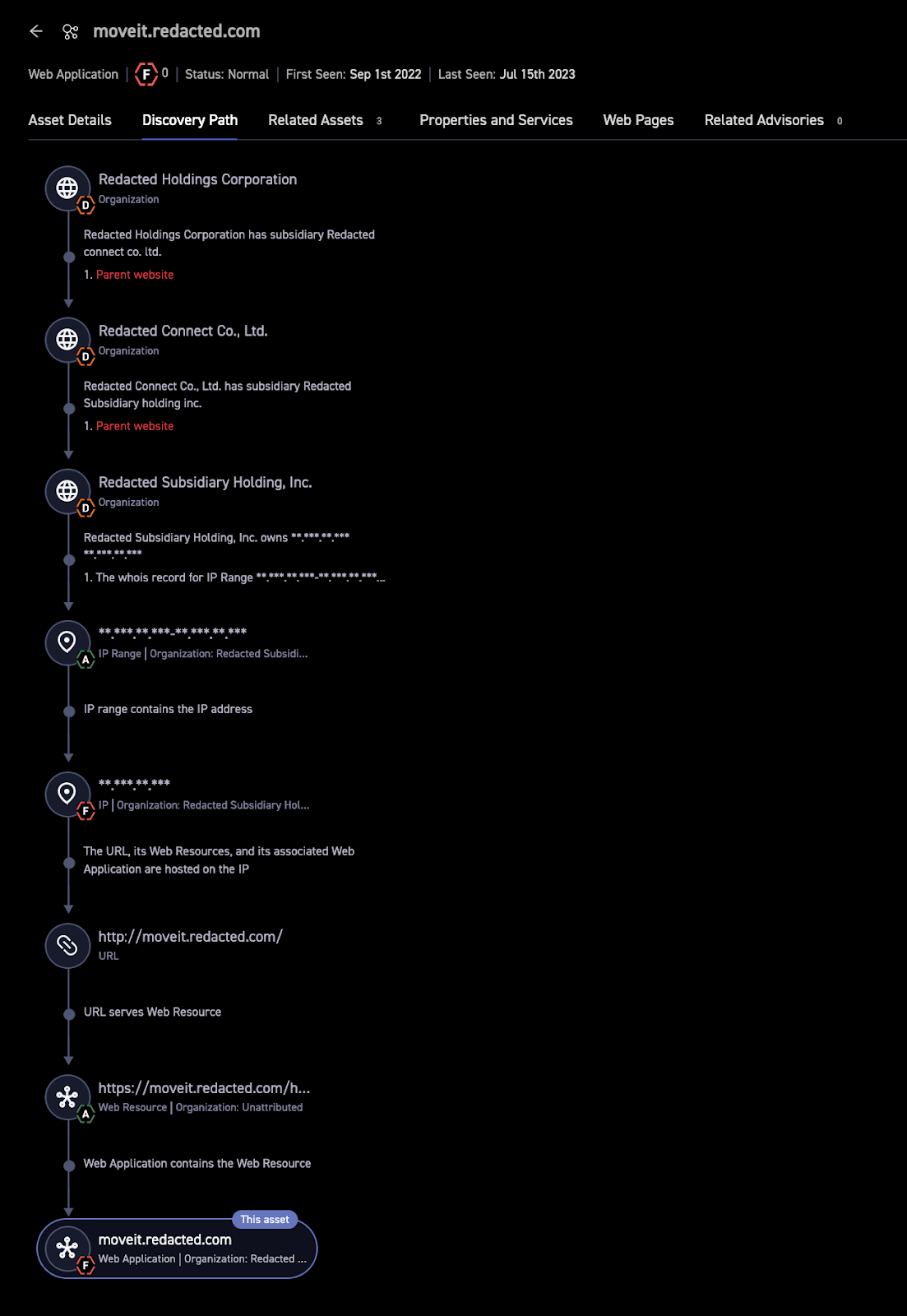
CyCognito also provides a detailed asset discovery path to show how the asset was found and which part of the organization is responsible for administering it. In Figure 3 below, customer data has been redacted with the word “redacted” and other data anonymized.
Figure 3: Discovery Path shows how the MOVEit Transfer instance was found and provides users with insight about the owning entity.
Using the CyCognito platform, customers can use the MOVEit Transfer alert available in the dashboard to learn more about the series of vulnerabilities. From within the alert or by filtering their inventory, customers can use custom filters to review MOVEit instances across their entire external attack surface. CyCognito actively assesses all MOVEit Transfer instances for the existence of these vulnerabilities and provides step-by-step remediation guidance to share with technical owners.
Want to see how it works? Check out our website and explore our platform with a self-guided, interactive dashboard product tour. To learn how CyCognito can help you understand your external attack surface and exposed risks, please visit our Contact Us page to schedule a demo.
Greg Delaney, a former senior product marketing manager at CyCognito, has been helping to bring new technologies to market in security for over 13 years including the areas of cybersecurity, machine learning-based threat detection, encryption, network security and mobile app security.










 Attack Surface
Attack Surface