Prioritization in vulnerability management is not just about fixing problems but fixing the right problems at the right time.
Not all vulnerabilities have the same level of risk. But gathering details to understand vulnerability impact takes time, a huge challenge for already overworked staff. Many are forced to work backward, taking critical issues obtained from 3rd party sources like CISA KEV or a Reddit forum and then search for assets that it may apply to.
This post will explore core elements of a sound vulnerability management program and how CyCognito Attack Surface Management (ASM) empowers response teams to act swiftly and decisively.
Common Approaches That Aren’t Working
“Work faster and close more tickets.” is a mantra when leadership treats proactive security as an line-item expense. Closing more tickets doesn’t always lead to risk reduction.
On the opposite end of the spectrum, some organizations choose to ignore issues completely, relying instead on system hardening and periodic patching cycles (monthly or quarterly) to manage updates. This “hope for the best” approach leaves large gaps of risk open for long periods of time.
For both, when a critical vulnerability (like those in CISA’s KEV) makes the news, the teams work backward, searching for assets in their inventory that match the target criteria. These are remediated immediately, often within the day, which is a testament to the team’s capabilities. Unfortunately, it is also reactive, opportunistic, disruptive, and exhausting.
CVSS Improvements - Helpful but Difficult
First.org, the organization that manages CVSS, is listening. CVSS version 4 was released in late 2023 and includes environmental metrics for business impact and five severity levels instead of three. This delivers higher fidelity scores and help SecOps teams prioritize more accurately.
On paper, it's progress. In practice, it requires security teams to do more math (and gather more data) in a workflow that they already don’t have enough time to do.
A simpler approach is required.
Core Elements of a Sound Prioritization Strategy
Stepping back for a moment, let's look at what a prioritization strategy should incorporate:
- Validated vulnerabilities – False positives waste time and increase frustration. You need to be confident that a presented issue exists on an asset your organization owns.
- Business context - An asset’s business purpose and owner will directly affect remediation priority and effort.
- Meaningful scores and grades – Severity scores must represent both an attacker’s thought process and impact on your business.
- Timely results – Data should be updated frequently to keep the mean time to remediation (MTTR) low.
Easier said than done. Which is why the last item on the list is perhaps the most important:
- Automation
Given the size of the external attack surface and rate of change (up to 10% each month, according to our research), prioritization (and vulnerability management overall) won’t be successful without tools that perform the required research and validation for you.
Using CyCognito to Discover and Prioritize Your Issues
The CyCognito platform automatically combines asset criticality, security test results and threat intelligence to assess which assets pose the greatest risk to your organization. Figure 1 shows a list of issues ranked in order of importance. This view can be filtered or reordered based on any context or tag.
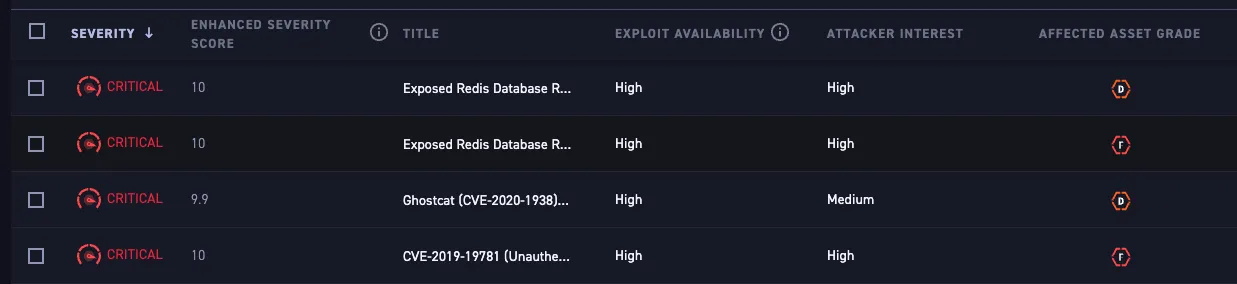
Figure 1: List of Top Issues
Organizations chartered with a “close more tickets” approach to risk remediation can shift to CyCognito and immediately know:
- All exposed assets have been identified, validated and actively tested
- The issues represent true risk to their organization
- They have the evidence to support risk scoring
- The team that owns the asset
- The steps needed to remediate
- If remediation was successful
CyCognito significantly outperforms vulnerability management solutions in prioritizing critical issues, with only 0.1%-0.01% classified as critical compared to ~3%.
Walkthrough of CyCognito’s Issue Prioritization Pipeline
Let's take a look at the steps CyCognito uses to build the issue list.
Step 1: External Asset Inventory
A good vulnerability management service is a good asset management service. This critical component is difficult (and time-consuming) to accomplish, which is why CyCognito automatically builds an inventory of exposed assets, without seed data or configuration (read more in this blog).
CyCognito inventory data is fed into the testing and prioritization engine. The results are accessed through CyCognito’s “Attack Surface Dashboard,” your external attack surface view for all divisions of your company. Figure 2 shows 49 environments (for example, web server, web application firewall, database, etc.), the number of assets, and the number of assets at risk. Different cuts of the data are available based on what you need.
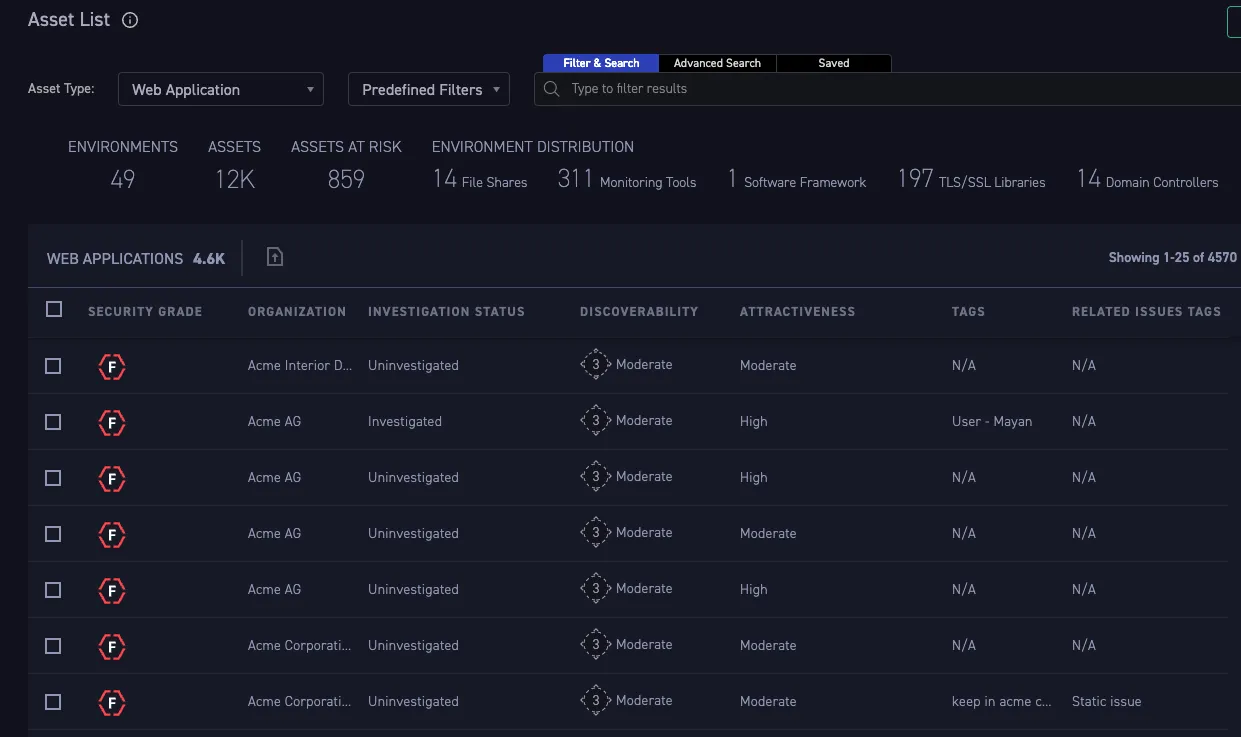
Figure 2: Attack Surface Summary
Step 2: Business Context
Business context, including ownership (attribution), is added to each asset. Evidence – as shown in Figure 3, a linked Wikipedia page – and certainty scores are attached to every decision. This makes it simple to validate decisions for cross-functional communication.
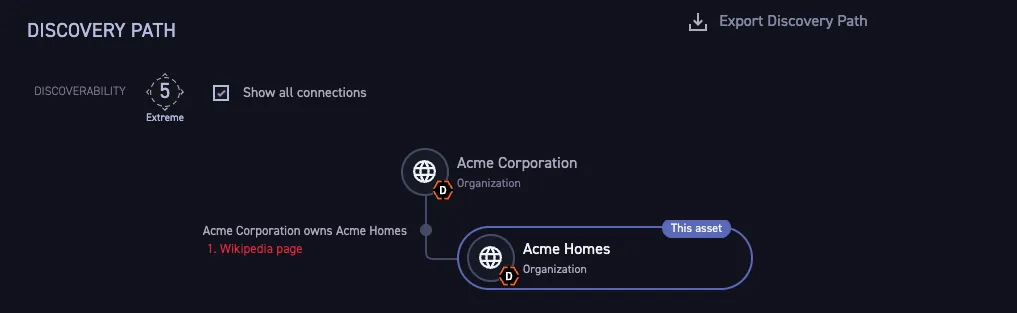
Figure 3: Discovery Path of Asset
Step 3: Security Test Results
Active security test results, including dynamic application security testing (DAST) for web applications, are added to each asset. Tests are multi-pass and multi-engine to ensure high precision and accuracy. Figure 3 presents a domain takeover risk example. More details are available by clicking into the issue.
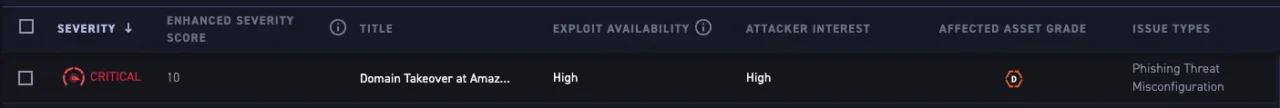
Figure 4: Critical Domain Takeover Issue
Step 4: Threat Intelligence
Third-party sources like CISA's Known Exploited Vulnerabilities (KEV) and dark web intelligence are layered on the asset for real-time insight into exploitation. Figure 5 shows a summary of impact analysis, including threat intelligence which indicates this issue is both highly available and of high interest.
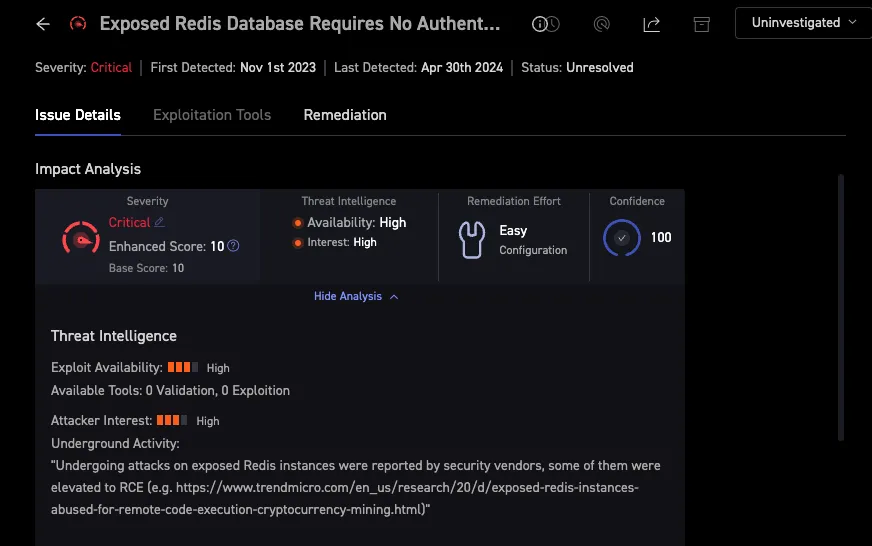
Figure 5: Impact Analysis Summary
Step 5: Risk Context
Discoverability (ease of being found by attackers) and attractiveness (potential value to attackers) context are added to provide a view into an attacker’s mindset. Figure 6 shows the security overview of an asset in the inventory. With both discovery and attractiveness at extreme level, the issues should be resolved immediately.
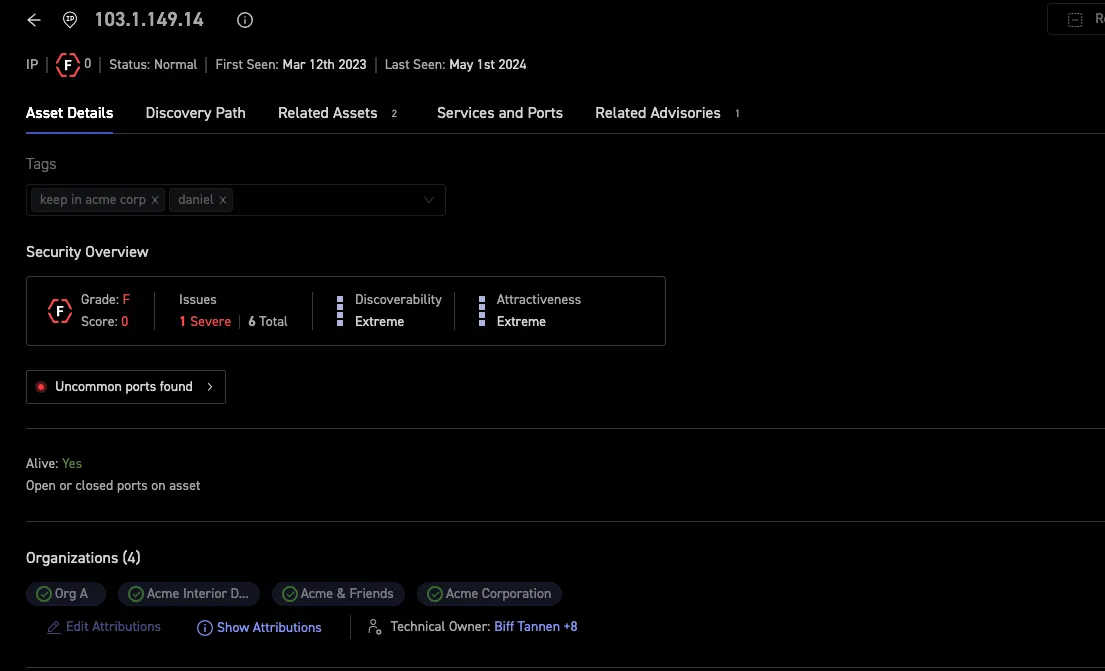
Figure 6: Security Overview
More about CyCognito’s Attractiveness and Discoverability Context
CyCognito understands that not all assets are equal in the eyes of attackers. For example, consider the two assets in Figure 7 with an identical number of severe issues. While they might initially appear to have the same risk level, their attractiveness to an attacker can significantly differentiate their risk. An asset using remote desktop protocol (RDP) might be more appealing to attackers due to its location in the network and ability to gain rapid access. Another asset with similar issues but less strategic importance might pose a lower risk.
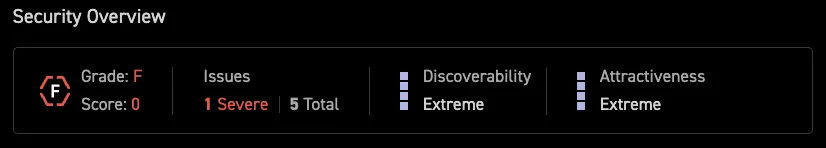
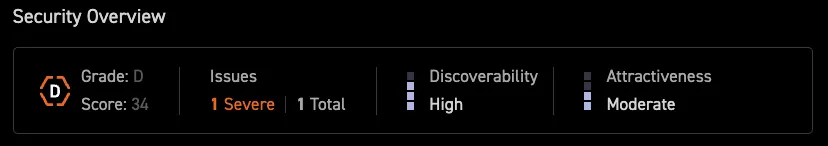
Figure 7: Comparison of Two Assets with Different Scores
CyCognito automatically sets the priorities so that you can move immediately into remediation. Have a question about the data? All supporting evidence is available for your review at any time.
CyCognito Remediation Planner Makes it Easy to Align Goals with Actions
Want to move your e-commerce division in Germany from a grade of D to a C? Use CyCognito’s remediation planner tool to create explicit directions on how to get there and measure progress during the journey.
CyCognito’s remediation tracker and remediation planning dashboards, a partial view shown in Figure 8, allows you to visualize remediation progress across division, geography, team, asset type and more. In this example the organization would need to address 425 issues to meet their goals. Click a link to get the full list with remediation steps.
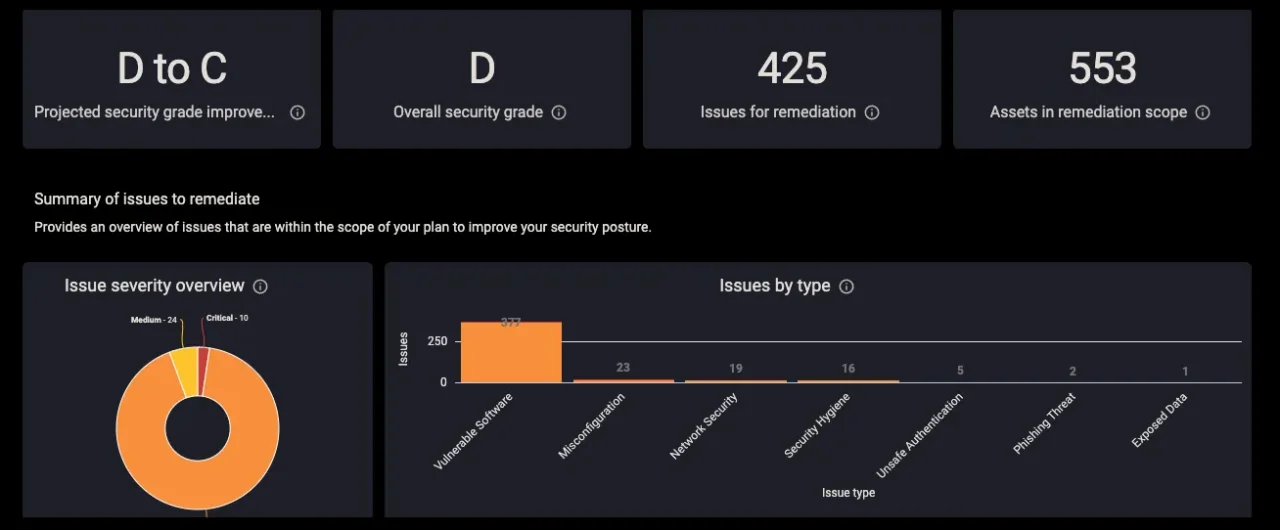
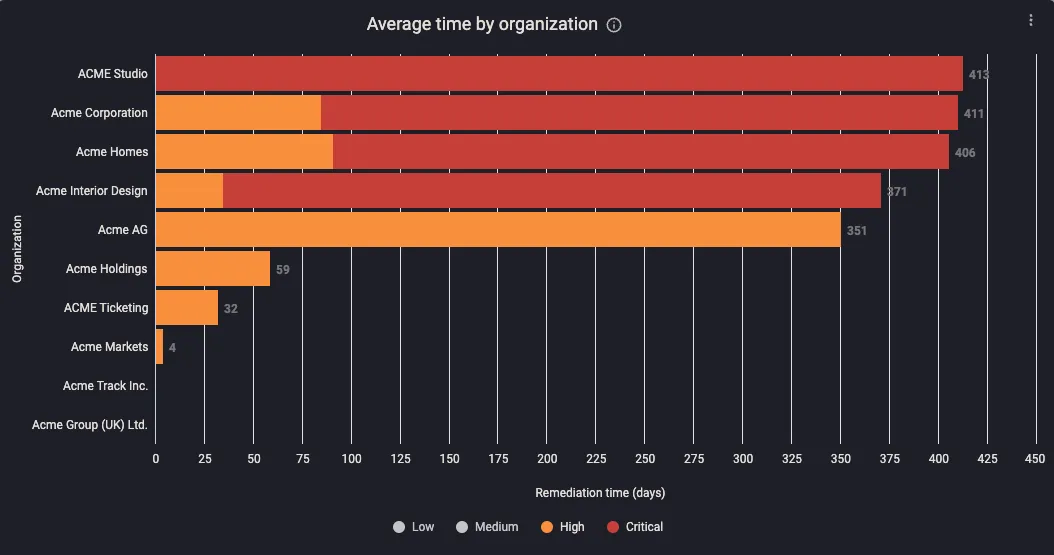
Figure 8: A Snapshot of CyCognito Remediation Planner
Let CyCognito Deliver Your Prioritization Workflow
Traditional prioritization requires manual effort and many assumptions, making it prone to inaccuracies. An automated prioritization workflow is required to maintain pace and enable your team to work efficiently.
CyCognito’s fully automated issue prioritization and remediation workflows allow your team to convert an operationally complex process into a simple service model. Contact us at [email protected] to discover how we can help automate prioritization across your entire attack surface.



