Effective asset management and rapid incident response are crucial for maintaining cybersecurity defenses. To address these needs, and building on its previous Vulnerability Response module integration, CyCognito has announced a new certified integration with ServiceNow's Configuration Management Database (CMDB). This integration enhances asset visibility and streamlines management, offering a significant boost to organizations' security postures by facilitating quick assessment and response to configuration and asset changes.
The Integration
Historically, CMDB solutions have only provided visibility into internal assets and their configuration. The integration between CyCognito and ServiceNow CMDB brings end-to-end synchronization for managing an organization's complete asset inventory. By synchronizing CyCognito assets with ServiceNow Configuration Items (CIs) in the CMDB, organizations can now automatically create, update, and delete CIs based on the status of external assets acquired through the CyCognito CMDB Integration. This dynamic synchronization ensures that the CMDB is always up-to-date with the latest asset information, facilitating quick assessment and response to configuration and asset changes.
Features and Benefits
The CyCognito CMDB Integration facilitates the periodic retrieval of external assets from the CyCognito platform and populates them into ServiceNow CMDB. It also displays the relationship between the related assets, providing a comprehensive view of the asset ecosystem.
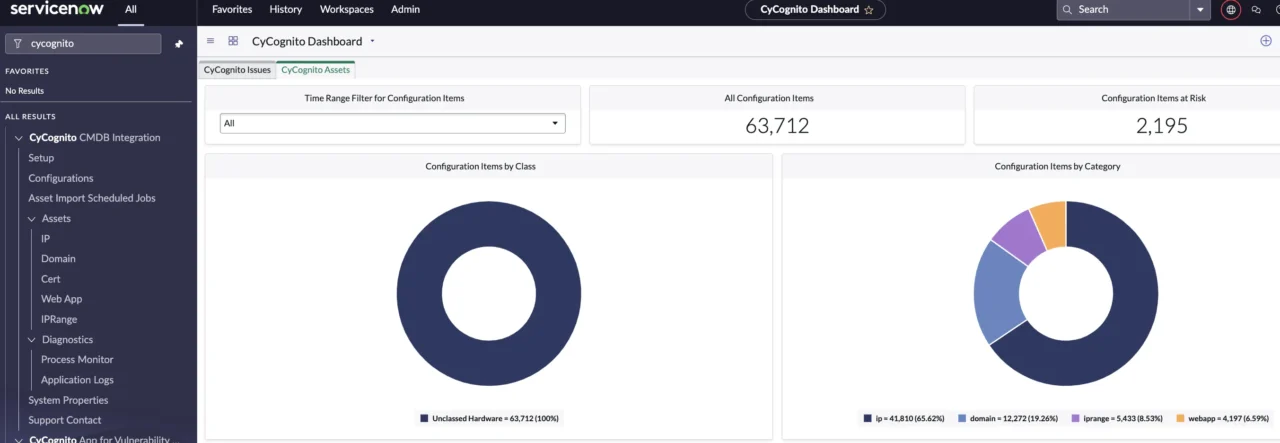
Figure 1. CyCognito dashboard showing external assets by category within the ServiceNow console
- Ability to configure CyCognito Integration Profile in ServiceNow: Users can set up and customize the integration to meet their specific needs.
- Periodic Asset Retrieval: The integration fetches assets on a regular basis to ensure the CMDB remains current.
- Detailed Asset Information: Users can view comprehensive details of the fetched assets within ServiceNow CMDB.
- Asset Relationship Visualization: The integration displays relationships between related assets, enhancing visibility and management.
- Configurable App Settings: Users can tune the integration by configuring various app settings to optimize performance and functionality.
- Process Monitoring: The integration includes a process monitor to track ongoing processes and allows for the cancellation of running processes if necessary.
Enhancing Incident Response
By integrating with ServiceNow CMDB, CyCognito ensures that security teams have access to the most current information, allowing them to quickly identify and respond to potential threats. This integration is particularly beneficial in complex environments where manual asset management can be time-consuming and error-prone.
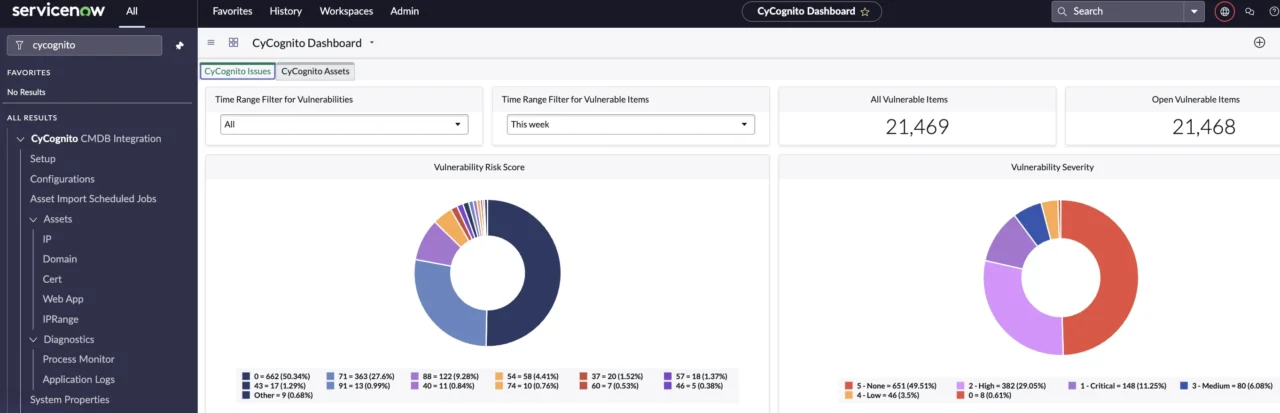
Figure 2. CyCognito dashboard showing external assets vulnerabilities and risk ratings within the ServiceNow console
Integration in Use
One of the world’s leading global information services companies standardized with the ServiceNow ITSM platform. The main reason for the standardization was to ensure that IT and SecOps had one source of truth about their assets, risks, and management tools. Working with CyCognto to discover their external attack surface then required that CyCognito provide integration into their ServiceNow CMDB, giving them visibility to internal and external assets. The Cycognito certified integration supports the latest Service Graph architecture and incorporates an Identification and Resolution Engine (IRE) to streamline issue management and reduce ticket duplication allowing for faster resolution to the most critical issues.
CyCognito's latest integration with ServiceNow CMDB represents a significant step forward in enhancing both asset management and cybersecurity. By leveraging the combined strengths of these platforms, organizations can achieve greater visibility, improved management of internal and external assets, and a stronger defense against security threats. To get started, visit the ServiceNow Store to install the CyCognito CMDB Integration application.


