Have you ever wondered just how much the average external attack surface changes every month? What about where cybercriminals might find leaked personally identifiable information (PII)? Maybe you’ve wondered about why a vulnerability is marked as critical? At CyCognito, we’re asking these questions too, which is why we published our Summer 2023 State of External Exposure Management report. This report examines how risk appears in the external attack surface and what factors security teams can use to prioritize external exposures.
In this edition of the State of External Exposure Management report, we examined trends related to attack surface size, web applications (web apps) in the attack surface, and how context informs prioritization of issues. Data for this report was aggregated and normalized from the external attack surfaces of our customers, primarily Fortune 500 global organizations.
Our goal with this report was to find actionable recommendations by asking interesting questions. If you’re curious, you’ll find a link to the report here and at the end of this blog. In the meantime, let’s look at some of the fascinating things we learned.
What Did We Learn?
- 70% of vulnerable web applications had severe security gaps like lacking WAF protection or not using an encrypted connection, particularly HTTPS, while 25% of all web applications (web apps) lacked both.
- The typical enterprise has over 12 thousand web apps and at least 30% of these web apps – over 3,000 assets – have at least one exploitable or high risk vulnerability.
- 74% of assets with personally identifiable information (PII) are exposed to at least one known major exploit and one in 10 have at least one easily exploitable issue.
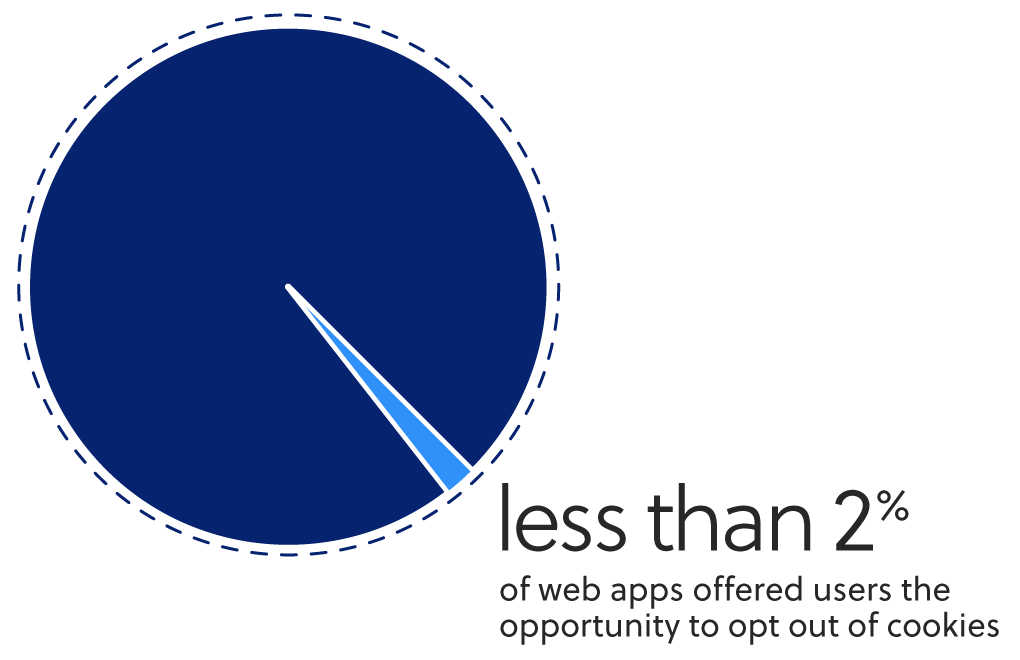
- 98% of web apps are potentially GDPR non-compliant due to lack of opportunity for users to opt out of cookies.
- For every easily exploitable critical severity issue affecting an organization, there are 133 easily exploitable high, medium, or low severity issues.
These are the five key results from our report, but the full report has plenty of additional findings that you may find useful. Looking across all these insights, we found three main takeaways, which we’ll discuss next.
Don’t Forget the Fundamentals
One of the biggest surprises from this research was how many assets were missing basic protections and features. WAFs, encrypted connections, and cookies aren’t magical, and their presence doesn’t necessarily mean that the asset is perfectly protected or GDPR-compliant. But their absence can be a warning sign that other, more sophisticated security techniques weren’t being applied to these assets either.
A 2021 report from ESG found that 69% of organizations are breached by unknown, undermanaged assets. It's these types of neglected assets that are most likely to put an organization at serious risk. Even small organizations can have thousands or even tens of thousands of web apps that they’re responsible for managing – these assets make up about 22% of the average organization’s total attack surface.
Prioritize the Core Assets
The average attack surface has tens or hundreds of thousands of assets and each of those assets could potentially be affected by dozens of security vulnerabilities. Prioritizing by CVE score is a common first step, but it’s also critical to understand what your assets are and what they do. Applying layers of context about assets and the issues that affect them is a great way to identify the most urgent exposed risks in your attack surface.
As an example, the first factor to consider could be the presence of PII. Some types of assets, like ones that take PII inputs, are far more likely to expose risk to the organization than others. We found that on average, 7% of all web apps that CyCognito monitors take PII inputs. 74% of those assets are affected by at least one issue. Your organization may want to focus on more critical issues, though, so you may look at just the one in 20 assets with PII that also have an issue in the OWASP top ten. To narrow it down even further, however, you could just focus on assets with PII and OWASP top ten issues that are easily exploitable by attackers. While these vulnerable high value assets are incredibly attractive to attackers looking to exfiltrate and sell data or leverage access, applying layers of context and filtering down to just the most critical issues helps find the most urgent exposed risks.
And De-Prioritize the Rest
Finally, it can be equally helpful to deprioritize issues that aren’t as important. We found that about 10% of all assets under monitoring are affected by security issues at any given time – in the average attack surface, that’s around 20,000 assets to sort through. While applying some context can elevate the urgency of some issues, as we saw above, in some cases context can be used to deprioritize issues that don’t pose as great of a risk.
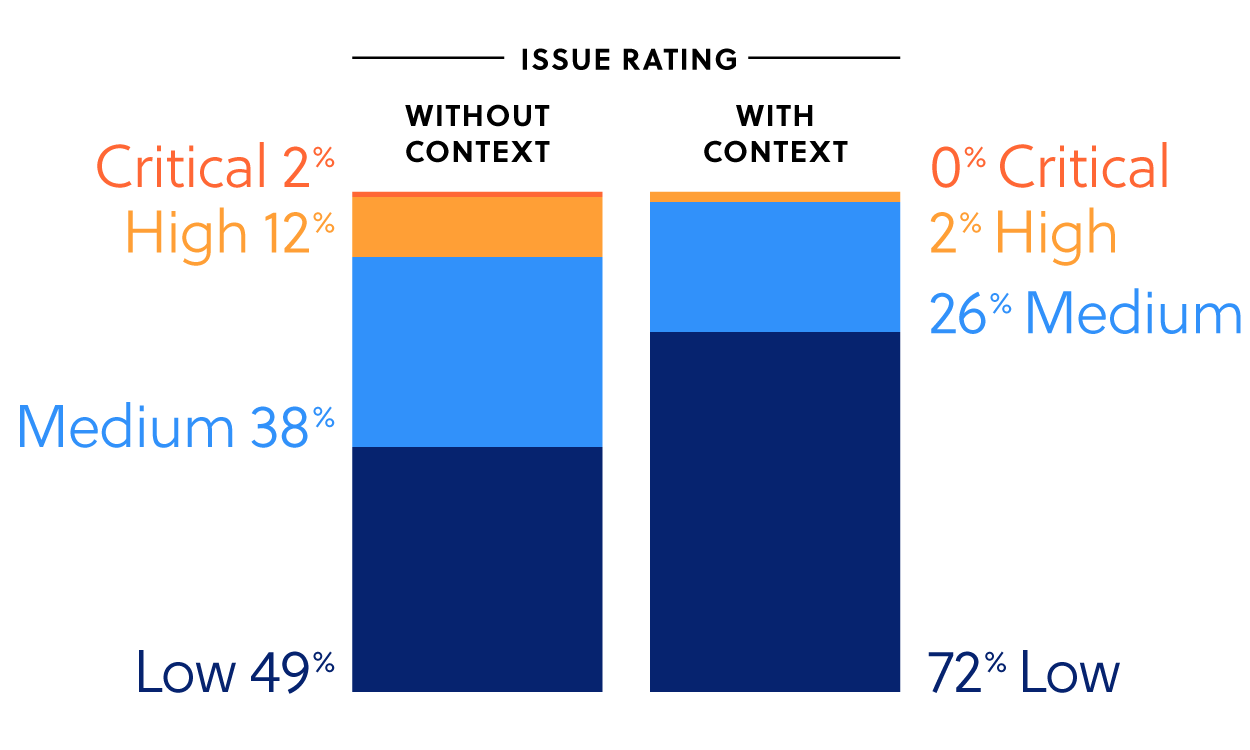
After applying additional context about the affected issue and assets, we found that the severity category of issues was downgraded in 35% of cases – i.e. that in this context the issue was less critical than its security rating implied. On the other hand, we found that the security category was upgraded for only 2% of issues. This results in a much larger volume of seemingly urgent issues being moved off the plate of security teams. Not only could this save hours of work, some of those upgraded issues wouldn’t have been addressed quickly without this additional context.
Interested in Learning More?
To read more insights about the external attack surface and external exposure management, download the State of External Exposure Management Report.
Want to see how it works? Check out our website and explore our platform with a self-guided, interactive dashboard product tour. If you’d like to chat to an expert about external risks that might affect your organization, you can schedule a demo at https://www.cycognito.com/demo.



