A lot goes into deciding what to buy during the holiday shopping season – shipping times, sale prices, and finding the perfect gift for your niece (who is impossible to shop for) are likely to be at the top of your mind. Unfortunately, attackers are counting on that.
An attacker’s best friend is urgency and Black Friday kicks off a perfect season for them. Not only are online retailers primarily focused on meeting shopping demand – and avoiding downtime on their sites – but shoppers are rushed, stressed, and primed to act fast to get a good deal. Because of this, both retailers and shoppers can create a prime environment for attackers to deploy ransomware, scam buyers, or steal valuable PII.
The countdown begins
Despite not celebrating American Thanksgiving, sites worldwide mark Black Friday and Cyber Monday as the beginning of the holiday sales season. Because of this, we decided to look at ecommerce assets in the UK and Europe, as well as global trends, to understand where external assets could be vulnerable to attackers this shopping season.

We examined an anonymized set of ecommerce assets collected from November 2023 to October 2024. These assets are web applications (web apps) or web interfaces. To identify whether they are used for ecommerce or part of an ecommerce system, we used machine learning and natural language processing to identify indications like payment functions, cart functions, or common keywords like “checkout.”
Ecommerce assets aren’t only in high demand on Cyber Monday – they also represent a potential treasure trove of data. The majority (53%) of ecommerce assets collect user PII. Although this number has gone slightly down compared to 58% last year, it presents a tempting target for attackers looking to harvest PII, steal payment card details, or damage a brand’s reputation. Collecting and storing PII makes an asset fundamentally more attractive to attackers and, combined with other vulnerabilities, can expose massive risks for an organization.
Some ecommerce websites are still on the naughty list
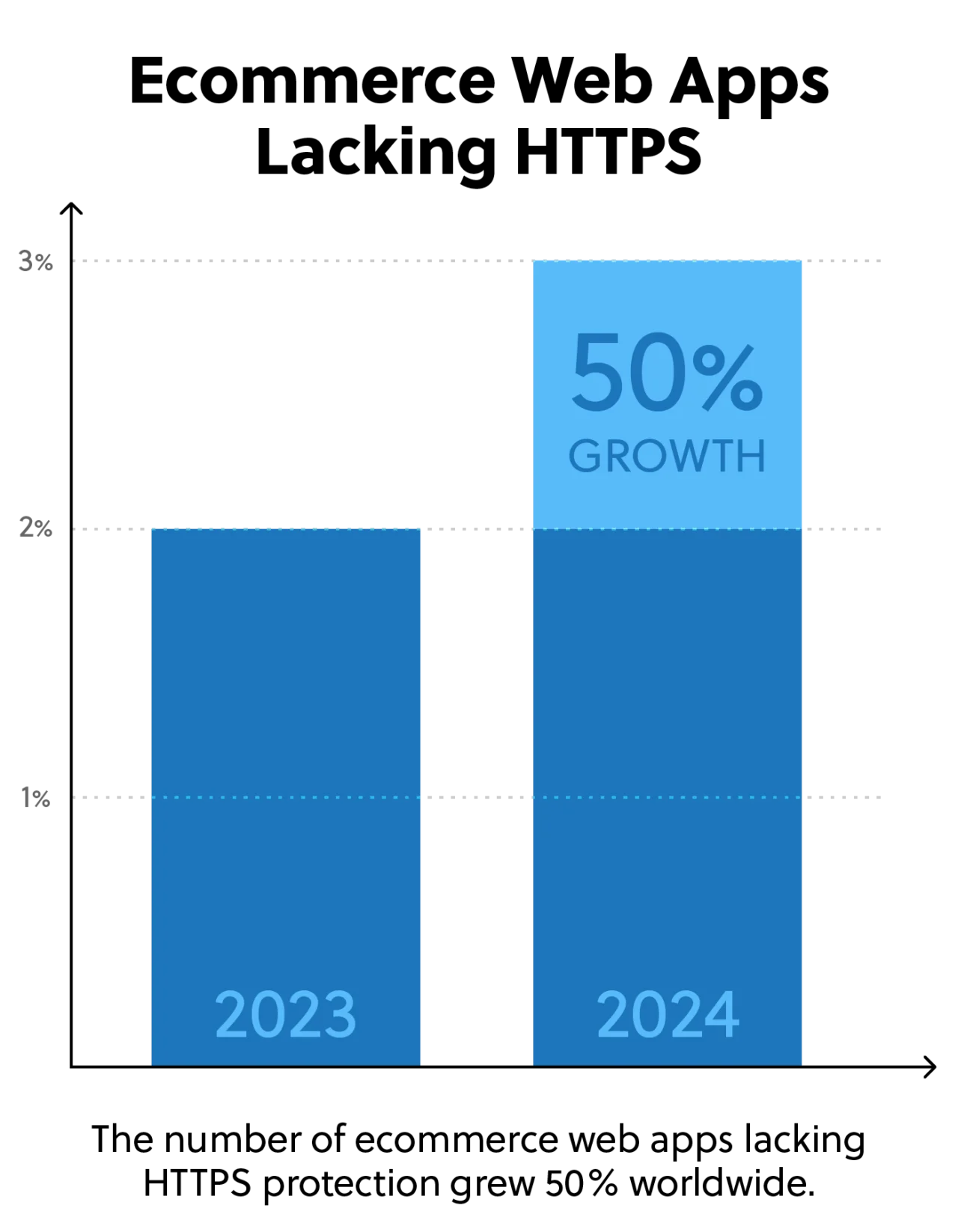
In the 2024 edition of our State of External Exposure Management Report, we looked at adoption rates of HTTPS and web application firewalls (WAFs) as a proxy for “basic care” on web interfaces and web applications. These measures aren’t the best protections available, but if an asset is missing them, it can be a sign of deeper neglect (or that the asset was forgotten about entirely).
HTTPS just celebrated its 30th birthday, but we found that adoption rates have gotten worse, not better, when it comes to ecommerce sites. Although the vast majority of ecommerce sites use HTTPS, 3% of ecommerce web apps still lack this protection, increasing from 2% last year. Adoption rates are even lower in Europe, with almost 5% of ecommerce assets hosted by European companies lacking HTTPS.
When it comes to WAFs, last year we found they were missing from over a quarter (28%) of ecommerce web apps. This year protections declined even further, with over 40% of assets lacking a WAF. This was consistent in both the UK and Europe as a whole as well.

While it’s never good for a web application to be missing a WAF, it becomes more serious if that asset is attractive to attackers or in some way presents a tempting target. We found that the number of ecommerce assets that contain PII and are missing a WAF also increased, from one in four (24%) in 2023 to over one in three (35%) this year. Numbers are worse in the UK, with 43% of ecommerce assets that collect PII missing a WAF, and in Europe, with 40% lacking this protective measure.
Certificate validity issues have improved, with only 6% of ecommerce assets having certificate validity issues compared to 13% last year. Unfortunately, in the UK rates actually increased, with 14% of ecommerce assets with certificate validity issues. Europe fared slightly better, with 11% of assets having certificate validity issues. Missing certificates creates a massive customer trust issue for retailers hoping to make a sale on Cyber Monday, as buyers may close a window or click away rather than trusting their details to a suspicious or insecure looking site.
Asking users to consent to cookies is a basic regulatory issue, especially for sites operating or with customers in Europe. Although companies have had years to become compliant with GDPR, we found that 79% of all ecommerce assets fail to ask users to consent to cookies, creating a potential compliance headache for the organization. This number has increased 1% since 2023. Across the pond, figures are only slightly better: only 67% of UK-based ecommerce assets fail to ask, and 76% across all of Europe.
But a lot to be thankful for
At the end of the holiday season, a lot of people make big commitments for their New Year's resolutions – eating healthier, picking up a hobby, or even running a marathon.
The New Year’s resolutions to clean up web apps worked, at least for retail organizations – fewer than 1% of ecommerce assets have any critical security issues, a 50% decrease from last year. Only 17% of those assets store PII, another marked improvement from last year where half of all ecommerce assets with critical issues collected or used PII.
Security teams are also focusing on the right issues, with the number of easily exploitable critical issues decreasing from 76% to only 67%. Easily exploited issues in general dropped as well, falling to 19% from 31% last year. This hard work has also cut the number of ecommerce assets affected by an issue in the OWASP top ten in half, dropping from 7% to 4%.
We found that almost 2 in 5 (38%) of ecommerce assets have one or more cryptographic vulnerabilities. It appears that the retail industry has made progress on this since last year, with a 10% decrease in vulnerable assets (48% to 38%). Over 40% of ecommerce assets in the UK have at least one cryptographic vulnerability, however, and numbers are even worse for Europe as a whole – 50% of ecommerce assets owned by European organizations have at least one cryptographic issue.
Unlike the holidays, good cybersecurity lasts the whole year
No matter when the sales start, retailers need to take the time to make sure their ecommerce sites are keeping valuable PII and financial information safe. Checking for basic issues, like HTTPS or missing WAFs, can serve as indicators of more serious security issues. Don’t leave discovering, testing, and remediating issues until the last minute – it’s more effective to conduct continuous discovery and low-and-slow testing throughout the year.
Making a list and checking it twice may be good enough for Santa Claus, but it’s not enough for ecommerce sites. Don’t leave discovering and testing your attack surface to once or twice a year – to stay ahead of attackers, prioritize continuous, comprehensive surveys of your entire external attack surface. You don’t want customers to find they received a piece of coal when they meant to buy a new sweater.
At CyCognito, we know you want to focus on the joyous parts of the holiday season. That’s why we spend the whole year continuously identifying, testing, and prioritizing externally exposed assets, giving organizations time to resolve critical issues before attackers can exploit them.
Methodology
For this piece, CyCognito’s research team aggregated and analyzed ecommerce web application assets across its customer base from November 2023 to October 2024. All findings are anonymized and normalized. These customers span multiple industry verticals and include a mix of small, medium, and large enterprises across the globe, including Fortune 500 companies.
References to security scores are based on the common vulnerability scoring system (CVSS) scores derived from the National Institute of Standards and Technology’s (NIST) National Vulnerability Database (NVD).
Interested in learning more?
To learn more about CyCognito’s platform and see it in action, explore our platform with a self-guided, interactive dashboard product tour. If you’d like to chat to an expert about external risks that might affect your organization, you can schedule a demo at https://www.cycognito.com/demo.



