With EASM now a critical piece of security operations, it seems like every vendor is jumping into the EASM pool. But not all EASM products are created equal. Companies in adjacent markets, like threat intelligence, are creating attack surface scanning products that are well short of enterprise grade. The shortcomings of these basic EASM products can waste time, erode confidence in security teams, and give an inaccurate picture of organizational risk.
To make sure you are getting your money’s worth and not creating headaches for your team, ask your vendor these five questions.
How does their product discover assets from IP ranges you don’t provide?
Basic EASM products work by scanning the IP address ranges you provide to them. But what about assets that are not on those ranges? If you don’t provide all the ranges - perhaps one belonging to another division or managed by someone who left the company - then these assets will not be found. And finding assets is the primary reason to purchase EASM.
CyCognito finds all of your assets – web interfaces, domains, IPs, IP ranges, certificates, and more – based only on your organization’s name. We don’t require you to provide any IP ranges. Because this approach doesn’t require any seed data to start searches or to ensure particular areas of the attack surface are covered, it’s called ‘seedless’ discovery.This discovery technique allows us to find assets that your security teams may not even know about. We typically discover 80% more assets than other EASM products, which eliminates blind spots. Effective prioritization, using live testing and dark web information, means teams will only need to deal with the most important exposures.
Do they discover which organization owns the asset?
Basic EASM products have no knowledge of asset ownership. Knowing which organization – the parent company, a division, a joint venture, a brand, outsourced marketing agency – is critical for remediation. That means hours of days of work for someone to figure out ownership and track down the right contact to start the remediation process. Even if you own a CMDB or CAASM product, the external IP mapping won’t be there, so neither will help.
CyCognito, by the nature of a seedless discovery process, starts by mapping out the complete organizational structure first, and then mapping discovered assets to the appropriate organization. This is done using advanced AI to interpret business databases, news sources, and websites. (We often find organizations IT teams don’t know about.). Once mapped, CyCognito can populate technical owners and assign to assets.
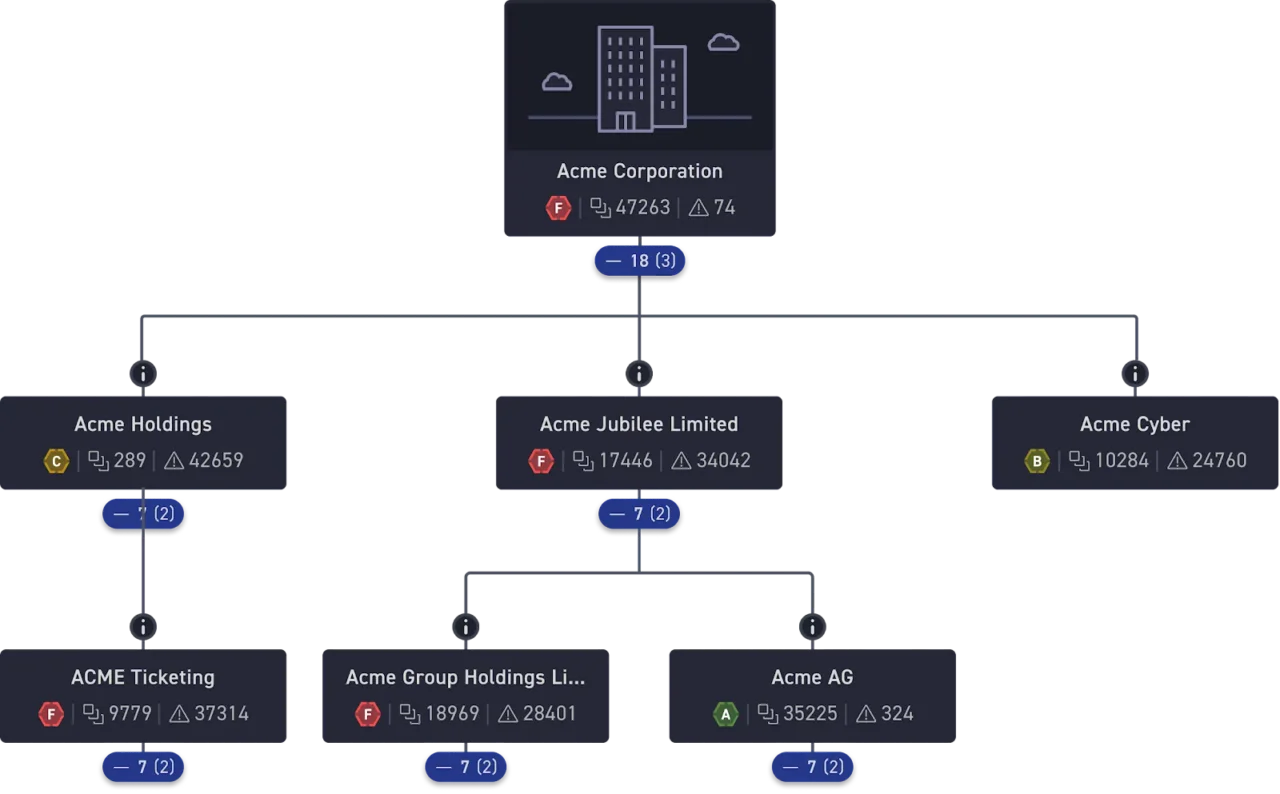
Figure 1. CyCognito Organizational Discovery Graph automatically attributes assets to organizations.
Do they know their false positive rate? What is it?
Basic EASM products - especially those that rely on open source intelligence - has a false positive rate as high as 70%. Seven out of ten issues found are false alarms. That means more headaches and wasted time for IT and security teams, and a low success rate for an EASM project.
CyCognito has a false positive rate of 5%. On top of that, CyCognito lists a confidence score, from 0 to 100, for each issue, so teams can judge for themselves. CyCognito determines confidence using a blend of proprietary techniques, including active security testing modules, risk validation modules, attacker chatter, heuristic models, and assessment of user behavior,, and more. The nature of the detection method can influence its accuracy, making our multi-method approach invaluable for accurate issue prioritization.
Do they scan for vulnerabilities or test vulnerabilities?
While many people use the terms scan and test interchangeably, in the context of information security, they are significantly different. Scanning, sometimes called passive scanning, compares software versions to a database of known vulnerabilities (CVEs), to know if there might be an issue. For example, CVE-2018-11776 - Apache Struts 2, versions before 2.3.34 and 2.5.16 permits SQL injection. This is where a lot of false positives come from. Without actually testing that particular instance of a server using Apache Struts 2, whether the vulnerability is real or theoretical isn’t known.
CyCognito actively tests assets and validates risk to see if they are exploitable. This is also called active testing or security validation. The CyCognito test engine uses the database of known vulnerabilities to configure tests that are likely to be successful, and then only reports a vulnerability if the test exploit is successful. Common exploits like SQL injection and credential stuffing are also performed regardless of the software version. The platform also annotates the vulnerability with evidence – the script, the result – that can be passed along to a security analyst or developer.
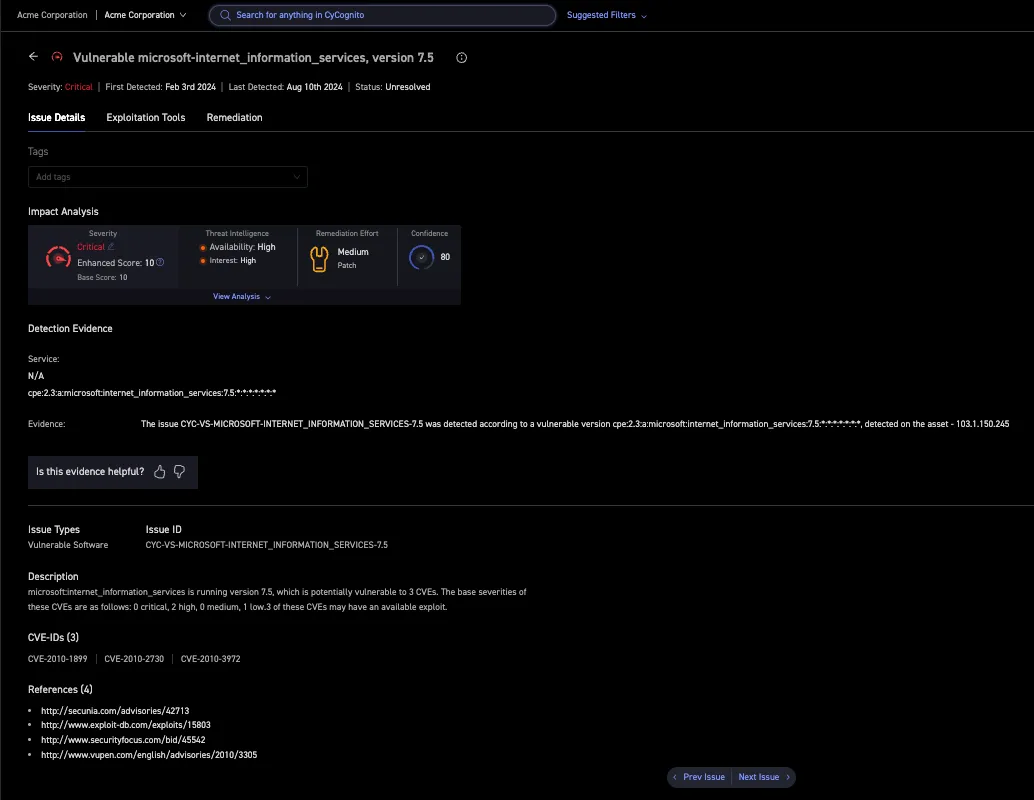
Figure 2. Evidence for a software vulnerability in a Microsoft server, including CVE, description and external references.
Can you view your attack surface by organization, function, or importance?
Basic EASM vendors do not discover your organizational structure, as mentioned above. They do allow for manual or semi-automated tagging, but that means a human needs to understand which organization each asset belongs to (a midsize attack surface has 5,000 assets; 50,000 assets is typical of a large enterprise) and either add tags by hand or create rules that assign tags with minimal mistakes. There is also no grouping by function, like ecommerce servers or physical security devices like cameras. Most cannot automatically tell you about important assets, like applications that handle PII.
CyCognito allows you to view your attack surface in three key ways. First, the attack surface can be viewed by organization, e.g., only the assets of a subsidiary. Second, it can be viewed by the type of asset. Perhaps you want to see only servers or cloud instances. Last, you can view the attack surface by business importance - ecommerce servers, systems that handle PII, corporate crown jewels. Gartner has coined the term ‘scope’ to describe this kind of asset organization. CyCognito allows for multiple scopes, each with role based access control.
There are a lot of basic EASM products on the market. Many of them will cause headaches and heartburn, not to mention a false sense of security. So ask your EASM vendor these five questions. If they don’t get back to you, that’s telling you something.


