What are the issues?
Earlier this month, Ivanti disclosed two new vulnerabilities affecting their popular Ivanti Connect Secure (formerly Pulse Connect Secure) and Ivanti Policy Secure remote access SSL VPN systems. Identified as CVE-2023-46805 and CVE-2024-21887, these vulnerabilities were assigned base scores of 8.2 (high) and 9.1 (critical) and affect software versions 9.x and 22.x.
What’s the impact?
Because CVE-2023-46805 allows attackers to bypass control checks and CVE-2024-21887 gives authenticated administrators the ability to execute arbitrary commands, chaining these vulnerabilities together allows attackers to run unauthenticated commands on the exploited systems.
Since Ivanti Connect Secure is used to give employees access to sensitive corporate resources from a variety of web-connected devices, these CVEs have a serious impact on companies' abilities to secure critical data. Their network access control (NAC) solution, Ivanti Policy Secure, also controls access to sensitive information by only providing network access to authorized devices and users and monitoring usage of critical applications.
Are these issues currently being exploited?
Unfortunately for users, these issues are actively being exploited in the wild. Volexity and Mandiant have both identified instances of individuals and groups, including nation-state threat actors, taking advantage of CVE-2023-46805 and CVE-2024-21887.
Can it be patched?
No patch is available for these issues as of January 17th, 2024. However, Ivanti has announced plans to release patches on a staggered schedule beginning on January 22nd and ending on February 19th, 2024. In the meantime, customers are advised to use a workaround provided by Ivanti. Users can also use Ivanti’s Integrity Checker Tool to identify evidence of compromise.
How does CyCognito identify assets vulnerable to CVE-2023-46805 and CVE-2024-21887?
CyCognito actively tests all customer assets for these vulnerabilities. First, the test attempts to append a subdirectory to the base URL attached to a potentially compromised asset. If this new URL is valid, the page is searched for key phrases, text, and a specific status associated with vulnerable versions of Connect Secure and Policy Secure.
How does this affect CyCognito users?
CyCognito customers will see a pop-up notification providing a short overview of this vulnerability, Ivanti’s advised action, and a list of vulnerable assets.
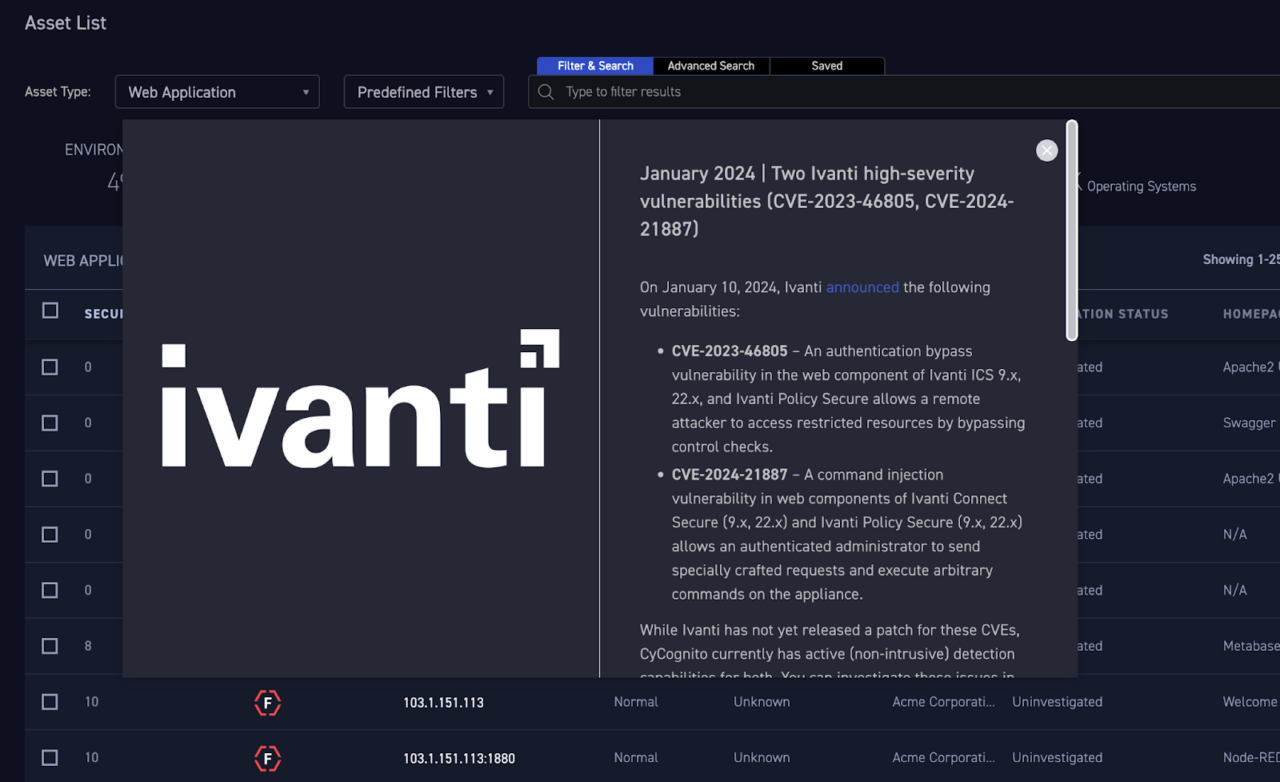
Figure 1: A pop-up notification in the CyCognito dashboard notifying users about CVE-2023-46805 and CVE-2024-21887
This notification provides shortcuts to read the full text of the issues advisory, check for IPs running the vulnerable software, investigate these CVEs within available issue data, and contact CyCognito customer support for assistance. Once patches are available, customers will also be able to identify patchable and already-patched assets.
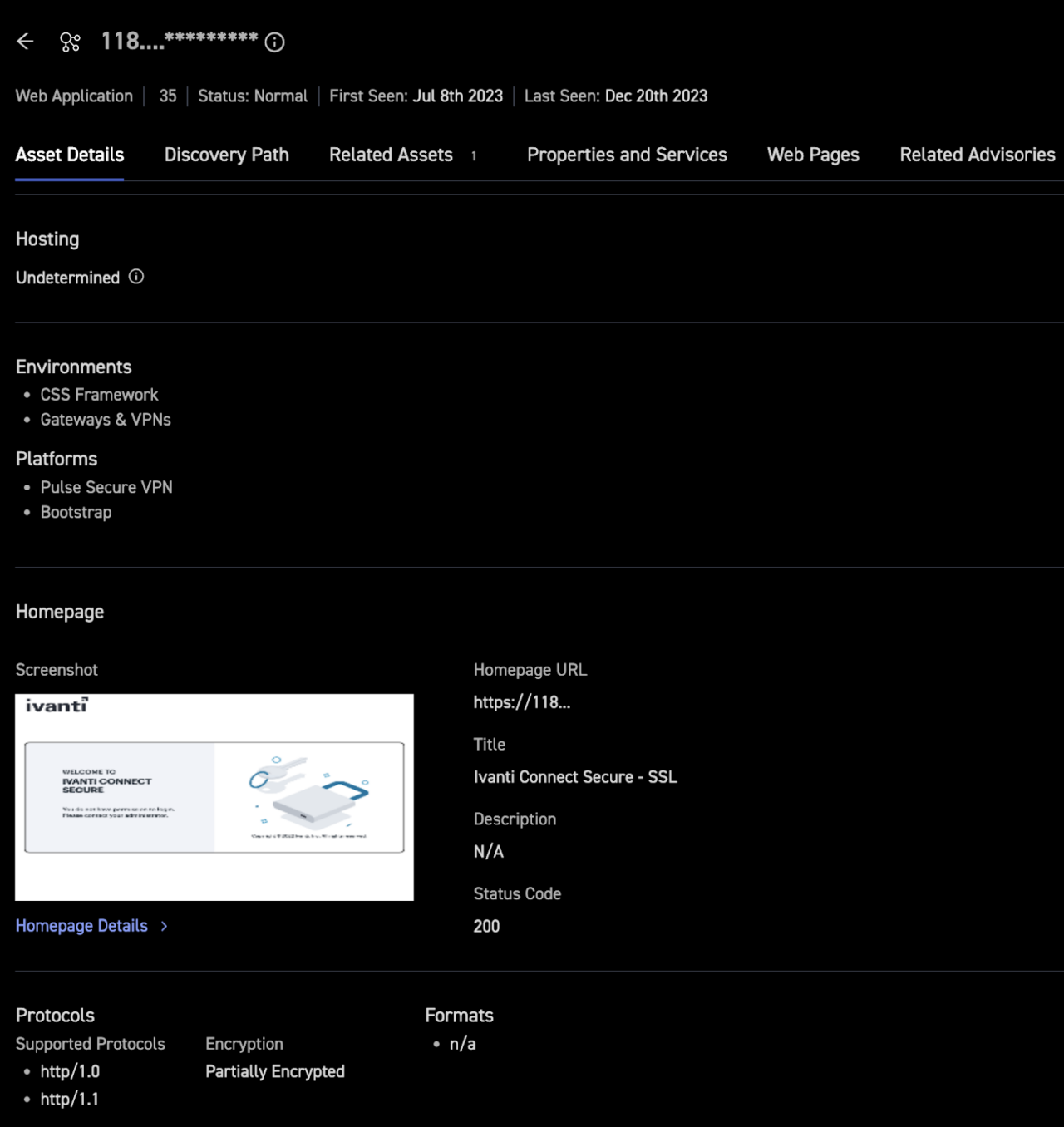
Figure 2: Asset details and screenshot for an IP address asset in the CyCognito dashboard attached to an Ivanti Connect Secure device.
While Volexity identified over 1,700 compromised assets worldwide, CyCognito identified only 30 vulnerable assets under monitoring. Affected customers have already been contacted directly by their customer support team.
If you’re curious about your attack surface and want to understand your external risks, you may be interested in CyCognito. Check out our website and explore our platform with a self-guided, interactive dashboard product tour. To learn how CyCognito can help you find, actively test, and prioritize your vulnerable assets, please visit our Contact Us page to schedule a demo.



