What is CVE-2024-7594?
CVE-2024-7594 is a severe unrestricted authentication issue affecting HashiCorp’s Vault’s SSH secrets engine. The National Institute of Standards and Technology (NIST) has not yet evaluated this vulnerability’s CVSS score but HashiCorp assigned it a base score of 7.5 (high).
An outside security researcher, Jörn Heissler, discovered an issue with the valid_principals field in Vault’s SSH secrets engine. This field did not require the valid_principals list to contain a value by default. By allowing this field to receive an empty string as valid, a malicious authorized user can request an SSH certificate that allows the attacker to authenticate as any user on the host.
A successful attack could allow a bad actor unrestricted SSH access to systems, potentially leading to data breaches, service disruptions, and unauthorized control over critical infrastructure.
What assets are affected by this vulnerability?
This vulnerability affects Vault Community Edition versions 1.7.7-1.17.5 and Vault Enterprise versions 1.7.7-1.17.5, as well as 1.16.9 and 1.15.14
Is a fix available?
HashiCorp has released patches for CVE-2024-7594; organizations can deploy Vault Community Edition 1.17.6 or Vault Enterprise 1.17.6, 1.16.10, and 1.15.15 to remediate this issue.
Are there any other actions to take?
If it isn’t possible to patch vulnerable instances, organizations can mitigate this vulnerability by setting the SSH secrets engine valid_principals field to a non-empty value.
Is CVE-2024-7594 being actively exploited?
As of October 1st, 2024, there have been no reports of active exploitation of this vulnerability.
How is CyCognito helping customers identify assets vulnerable to CVE-2024-7594?
CyCognito is investigating methods to deploy to actively detect this vulnerability. Meanwhile, users can check their assets may be vulnerable using provided filters in the CyCognito platform. All customers have access to an in-platform emerging security issue announcement as of October 1st, 2024.
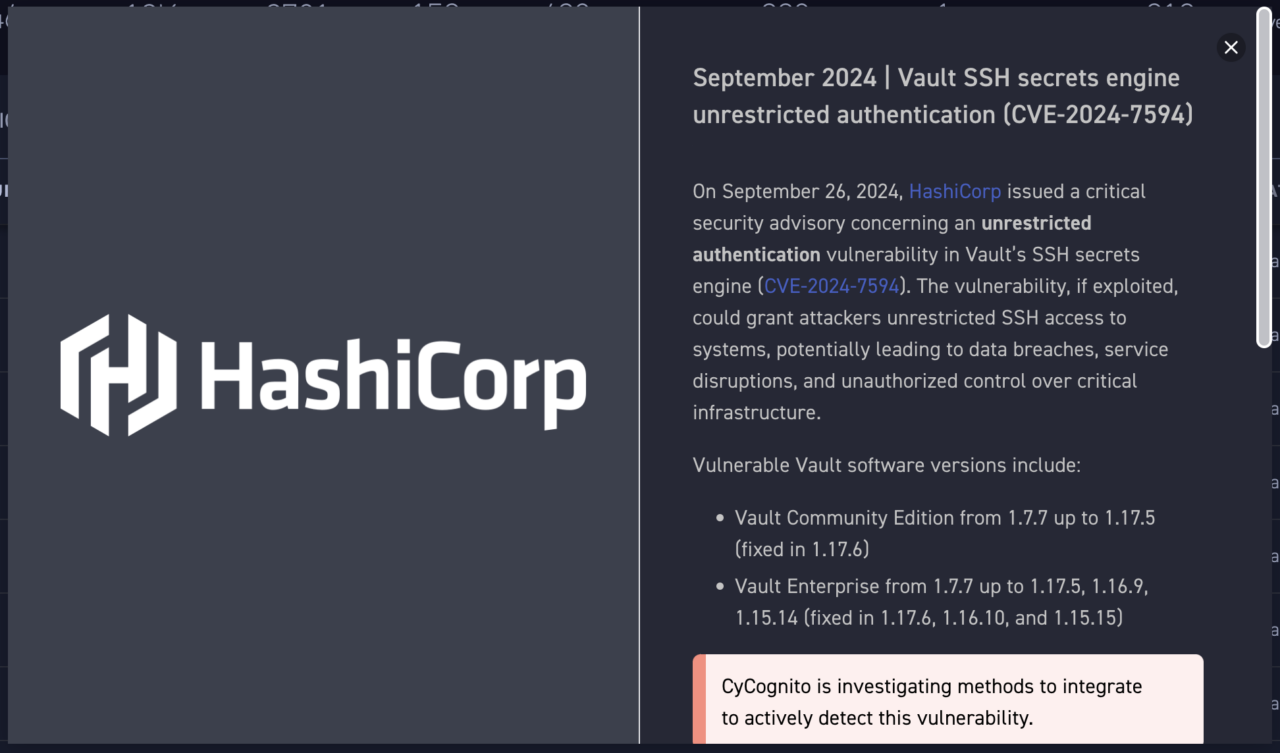
Figure 1: The alert sent by CyCognito for CVE-2024-7594
How can CyCognito help your organization?
CyCognito is an exposure management platform that reduces risk by discovering, testing and prioritizing security issues. The platform scans billions of websites, cloud applications and APIs and uses advanced AI to identify the most critical risks and guide remediation. Emerging companies, government agencies and Fortune 500 organizations rely on CyCognito to secure and protect from growing threats. Want to see how it works? Check out our website and explore our platform with a self-guided, interactive dashboard product tour. To learn how CyCognito can help you understand your external attack surface and exposed risks, please visit our Contact Us page to schedule a demo.



