Penetration testers and Red Teamers are vital to risk management. Part police officer, part archeologist – even seemingly sometimes part magician – their passion pushes them continuously forward in pursuit of security gaps in networks and systems. Their goal: prevent breaches by uncovering risk before adversaries.
With over 25,000 CVEs recorded in 2022 and even more slated for 2023, a pen testing team has its work cut out for them. Pen testing, with time and practice, is a finely honed skill. Some of the skill development is simple muscle memory. Other skills, such as exploit chaining or identifying obscure indicators of compromise (IoCs), are honed during years of practice. Pen testing is exhilarating. Pen testing is also mentally and physically exhausting.
Challenges with Pen Tests
However valuable, penetration tests come with challenges. From an organizational risk perspective, the low frequency and coverage combined with manual reporting lead to long remediation times. From an individual tester's perspective, tedious repetitive tasks consume a significant portion of a time-bound project.
Repetitive tasks, long remediation times, and operationalization challenges. Let's take a closer look.
Labor-intensive repetitive tasks
Time-bound black-box pen tests are often 2 weeks with long hours – “too much to do and too little time” is a common theme. Pen testers are precious and expensive resources. This means keeping them focused on meaningful and complex activities – labor-intensive repetitive “legwork” should be kept to a minimum.
Reconnaissance and scoping activities. Business scoping, open-source intelligence (OSINT) gathering, software fingerprinting, gathering architecture information, capturing exposed domains, etc. all are time-consuming. Due to the amount of work involved these efforts are clearly bounded - either by time or by IP-range. And if the scope calls for full external network topology discovery, this means days of work.
Vulnerability assessment scanning. VA can be mind-numbingly repetitive. Scanning a handful of known IP ranges for CVEs isn’t difficult, but if the project scope includes the full known attack surface, the effort (and redundancy) increases significantly.
Attribution investigation. Uncovering an asset’s owner (not basic WHOIS info, but the actual business unit that owns the asset) is especially time-consuming and may even require human-to-human contact. This can take hours alone – it’s not uncommon to cut corners here simply based on time constraints.
Active testing. Typically, active testing is human-led to manage risk if the pen test scope includes exploitation. However, many low-impact active tests are repetitive and labor-intensive. Web app testing is a good example - authentication bypass checks, use of default credentials, and weak javascript libraries are non-destructive tests that take a lot of time.
[Looking for more info on the importance of active testing? Read more in this blog.]
Long remediation times
The size of an organization’s external attack surface coupled with a status-quo pen test’s high cost and long time-to-deliver force many organizations to reduce scope and frequency. This means only known “crown jewel” assets are deeply tested (as low as 5-10%), and when they are, it’s for a specific reason (for example, PCI-DSS compliance).
Infrequent testing of a small set of assets leads to long remediation times, often 12 months or more. CyCognito’s 2023 State of External Exposure Report reports that 74% of assets with personally identifiable information (PII) are exposed to at least one major exploit. Issues such as these need to be discovered, addressed and remediated quickly – not months later.
Clearly, traditional pen tests can feel disconnected. These point-in-time risk snapshots have a short shelf life in today's rapidly changing risk landscape.
Operationalization difficulties
Risk communication is often fractured in the best of times. Close to half (44%) of respondents in recent research reported they suffer from slow or delayed risk remediation or too many manual workflows and processes.
Due to the highly manual nature of a typical pen test, investigation results arrive via spreadsheet or pdf report, possibly weeks after the close of the project.
Even excellent pen test results are significantly less useful when delivered at inconsistent times and require interpretation before implementation. Plus, these inefficiencies slow down confirmation that remediation was successful – leaving the issue in limbo until the next test cycle.
[Looking for more info on managing exposure? Read more in this blog “External Exposure Management: Key to Safeguarding Your Attack Surface”.]
Automated Pen Testing Solves Three Challenges at Once
Organizations must embrace sweeping change to maintain pace with modern external risk exposures. The target goals shouldn’t be modest; 10-20X the current scope of testing and 26-52X the current testing cadence. Put more simply, 100% of external assets should be tested every one or two weeks.
Adopting a hybrid model for pen testing is the only way to achieve this goal. Full automation of reconnaissance and low-impact active testing combined with human-led advanced tests provides the cadence, coverage, and scope that maintain pace with risk.
How much time can be saved with automated pen testing? Let's look at an example.
A status-quo pen test of assets within a bounded IP range can take two weeks. In this timeframe, performing reconnaissance and gathering attribution information take days. Low-impact application testing would only be possible on 1 or 2 apps, even for rudimentary attacks like credential stuffing or directory traversal. High-risk “destructive” active tests that include initial access, execution, persistence, etc., require intense focus and more time, which by then is a scarce commodity.
Here is a table that compares a manual approach to a nearly fully automated approach.
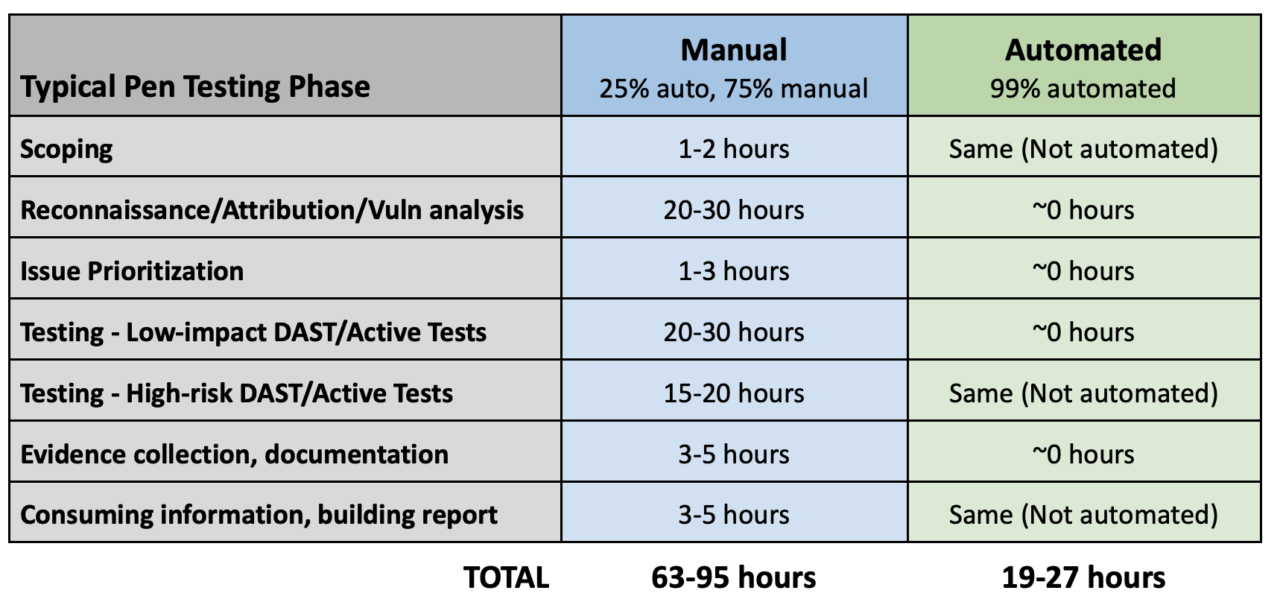
The numbers listed are approximate but realistic. Every pen testing team has its own methodology and toolsets, but clearly, automating reconnaissance and some active testing tasks has the potential for significant time savings.
In addition, an automated approach provides a consistent data set for pen testers to build from. Instead of starting from zero, they can spend only a handful of hours reviewing data before beginning higher-risk active testing such as exploitation and lateral movement. They also have a current list of “crown jewel” assets that should be tested immediately (and, as importantly, the list of assets that don’t need to be tested).
Not only does automation make better use of a pen tester’s time, but it also reduces the repetitive tasks that lead to stress and burnout.
Scale your Pen Test and Red Team Operations with CyCognito
Designed by reconnaissance leaders from a globally recognized intelligence agency, CyCognito built the discovery and testing engines in its external attack surface management (EASM) and active testing platform to replicate an attacker’s thought processes and workflows.
This transformative service supports a wide range of initiatives:
- Increase test cadence and coverage to match the speed of risk change
- Avoid the risk ripple effect that occurs with incomplete asset inventories
- Leverage 25,000 tests to reduce repetitive work
- Automate active security testing for all exposed assets, including web applications
- Overcome challenges with operationalizing pen test information
Pen testers and red teamers with access to CyCognito are able to tap into “single source of truth” that helps both organizationally and personally. The result – offensive security testing efforts that are fast and focused, without the common ups and downs.
Find Out More
Download the CyCognito whitepaper “Rethinking Penetration Testing” to learn more about how CyCognito automated testing data delivers efficiency to your penetration testing and red teams.
CyCognito is an enterprise-grade exposure management platform that will increase the power of your pen testing program. Read more about how CyCognito provides scalable, comprehensive results in our pen testing pen testing datasheet.


