Whether you're the CISO or part of the incident response team, it’s likely you have heard of exposure management (EM).
Introduced by Gartner in 2022 as the evolution of vulnerability management (VM), the name “exposure management” was adopted by vendors faster than you can say “next gen” or “AI-powered”. Unfortunately for consumers the hype added more confusion than clarity.
This blog is a chance to reset expectations. First, the good news is that EM represents significant progress for reducing risk. Second, you are likely pursuing exposure management without realizing it.
A Quick Recap
IT security team managers are well aware of elevated stress levels during incident response. Critical issues even more so – responding to a breach or ransomware attack requires CISO, CEO and board of director level involvement.
Resolving issues before they escalate, for instance identifying a website handling PII without a WAF or an asset susceptible to HashiCorp Vault SSH CVE is the ideal goal for everyone involved.
Gartner’s EM definition reads like a CISO’s mission statement: “a set of processes that gives enterprises the awareness to continually and consistently evaluate the visibility, accessibility and vulnerability of their digital assets.”
Busy IT security teams need more detail or risk misinterpreting what to do or how best to do it. If there’s too much uncertainty, they may choose not to implement due to the time required to “figure it out”.
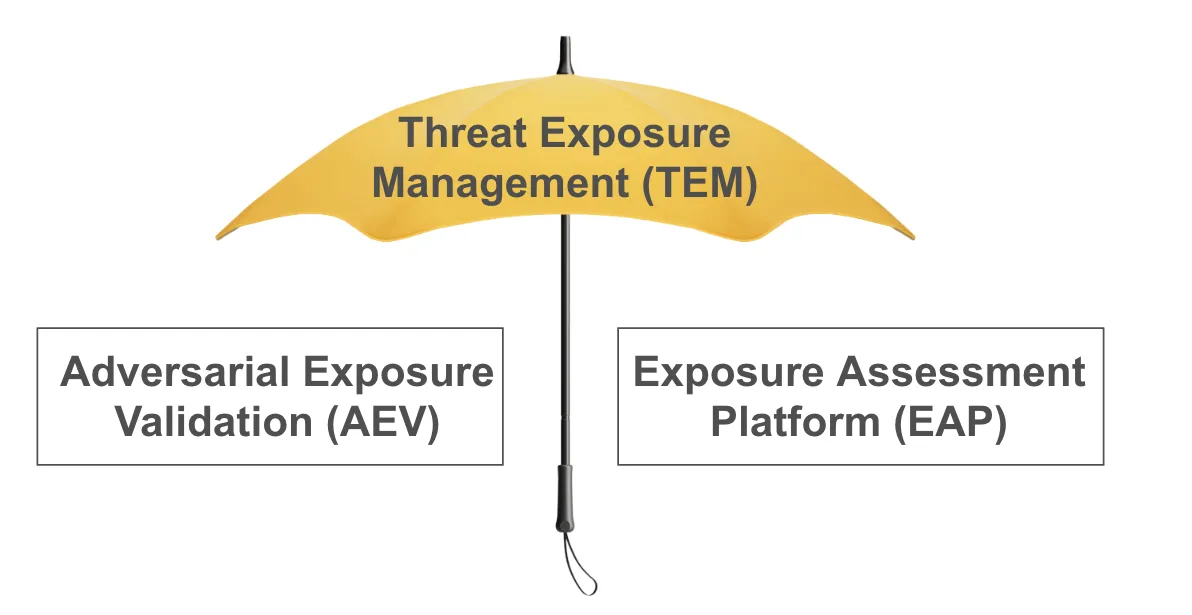
To this end, in 2024 Gartner added two sub-categories to EM: adversarial exposure validation (AEV) and exposure assessment platform (EAP). AEV focuses on testing attack paths, and EAP addresses vulnerability identification, assessment and prioritization. Together they form threat exposure management (TEM) and replaces the original “exposure management” terminology.
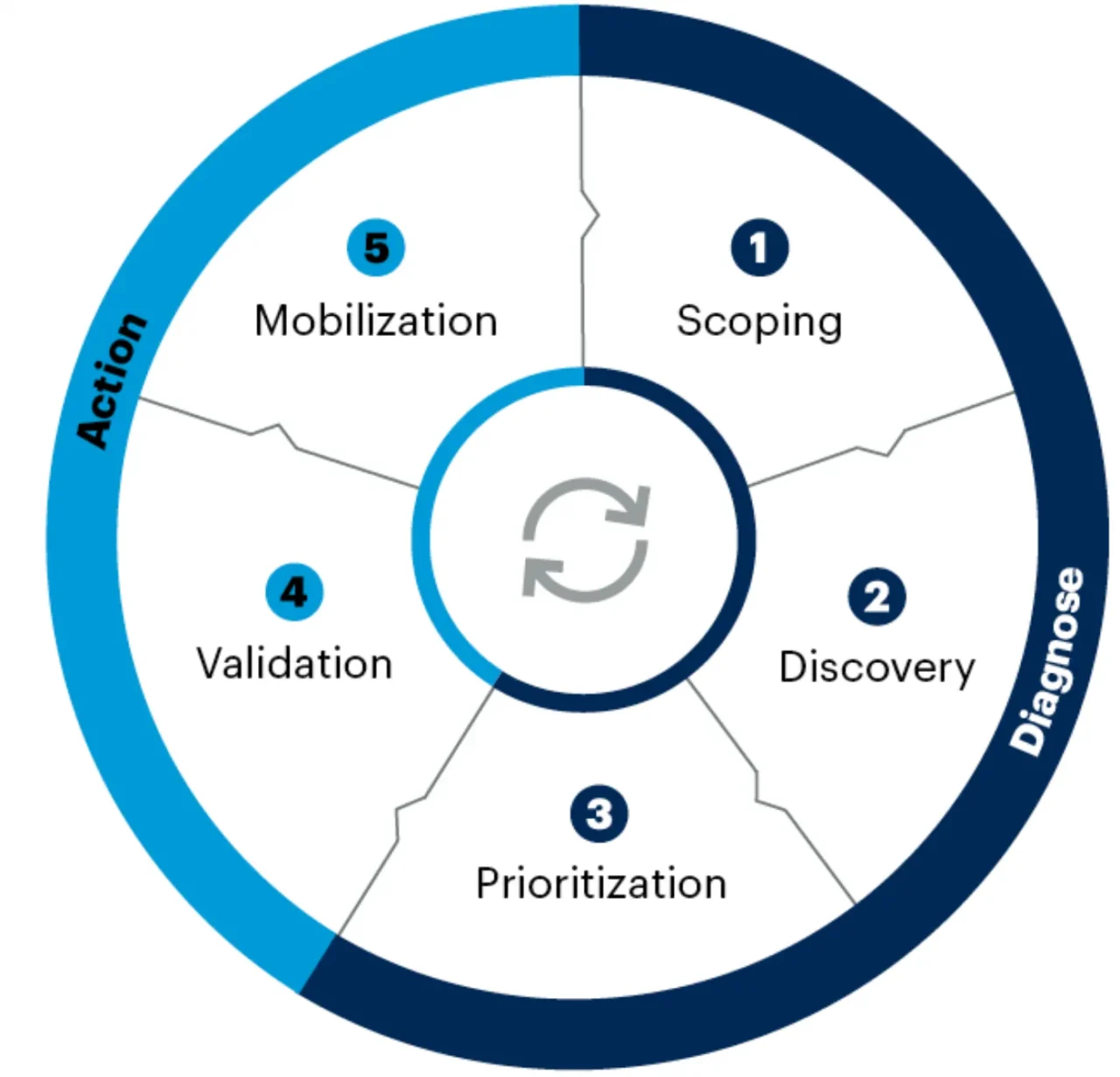
Implementing TEM starts with continuous threat exposure management (CTEM), a five-step program designed to operationalize the mission statement.
Six Signs You Need Threat Exposure Management
If you are frustrated by visibility and coverage challenges, and never-ending lists of issues that require manual reconnaissance, planning and revalidation, you aren’t alone. Many organizations have issues coming in faster than they can be resolved. For example, our recent study found 60% of surveyed organizations update web apps weekly or more often, yet 75% test their web apps monthly or less often: a clear disconnect.
Here are six signs your organization would benefit from TEM:
- Limited Visibility into External Assets: Without visibility to all exposed assets, inventory, especially those external to your main infrastructure, you are vulnerable.
- Large Digital Footprint or Complex Supply Chain: Organizations with a sprawling network of partners, vendors, and external systems are at risk of missing exposure points.
- Frequent Security Incidents and High False Positives: If your security team is bogged down by constant incidents or unnecessary false alerts, it's a sign your current systems are not keeping up with your attack surface.
- Incidents from Shadow IT: Unauthorized systems or apps (shadow IT) easily create vulnerabilities if they aren’t visible and managed.
- High Mean Time to Remediate (MTTR): Manual effort to validate issue criticality is a sure sign your MTTR is too high.
- Difficulty Complying with Frameworks: Struggling to meet compliance standards, such as GDPR or PCI-DSS, is a sign that your exposure management is incomplete.
Five Critical Priorities
At the top of this blog, I wrote that you are likely pursuing TEM without realizing it. Why? Chances are, in your (brief) moments of downtime or the end of a team meeting, you’ve talked about perfect-world scenarios that reduce effort and increase your resilience against attack. As the evolution of vulnerability management, CTEM’s scoping, discovery, prioritization, validation, and mobilization phases capture many dream list items. (The definitions aren’t always obvious – don’t assume you know what they mean as I did; there are important nuances to each that are worth understanding.)
To scale and meet today’s IT demands—and prepare for future needs—start with the essentials with your implementation.
- Focus on external exposures. External actors are involved with 80%+ of breaches.
- Find everything. All exposed business units and all assets tied to them, across cloud and on premise systems. No exceptions.
- Test everything. Active security testing, including application security, on all exposed assets. Not just crown jewels. No exceptions.
- Prioritize based on risk. Business risk, not issue criticality.
- Share broadly. Use integration to glue it all together with your existing processes.
Together, these provide the core elements that tackle the majority of exposure management requirements: validated, meaningful issues that enable your teams to successfully respond.
Legacy technologies that lack these capabilities cannot dynamically react to attack surface change and miss the brunt of risks that fall outside of CVEs, like misconfigurations, exposed data, and security control validation (CVE detection technologies are forever playing catch up, for example, as of this writing NVD has a backlog of 17K+ vulnerabilities.)
Take Your Next Step
With the right technology TEM implementation doesn’t have to be slow. If you have questions about fit, value and requirements, CyCognito offers two short guidebooks to help you:
- Exposure Management: The Definitive Guidebook for the CISO: Learn about exposure management from a leadership perspective—what it means, how to calculate ROI, how to author a business case, and how to ensure success through an Exposure Management Center of Excellence (EMCoE).
- Exposure Management: The Definitive Guidebook for the Practitioner: Understand exposure management from a practical perspective, learn how to transition from your current skills to new methodologies, the value of EM and your next steps.
CyCognito automates key CTEM scoping, discovery, prioritization, validation, and mobilization phases. Reach out to us to learn more about how organizations using the CyCognito platform achieve 95% of their EM technology goals for their external attack surfaces, with zero installation, configuration, or management. Automatically.



