In today’s heavily regulated business environment, organizations must illustrate conformance to the compliance and regulatory frameworks that apply to their industry. Often, these events are disruptive, stressful, and costly.
During this time, milestones are identified, gaps are uncovered, issues are remediated, evidence is collected, and documentation is updated. Day-to-day activities are often put on the back burner, and stress levels rise as your teams scramble to gather information in preparation.
Passing an audit is a challenge from start to finish. A recent study found that only 43.4% of organizations report achieving 100% compliance during interim compliance validation. Considering an audit can take weeks to accomplish, this means the blast zone from the project can easily turn into months as issues are investigated and resolved.
Understanding Requirements is Often the First Step
The time preceding an audit involves extensive meetings to interpret the latest standard and translate it into the language of your company.
Organizational pressure to pass an audit often results in security teams feeling like they are under the magnifying glass, resulting in a “stop everything” approach to meet the needs of the auditor, executive leadership, and the business. IT security teams are forced to become compliance experts, and constant fire drills become the norm.
For those who are not full-time professional auditors, interpreting the path to alignment with a control can be frustrating. Some are more clear than others – for example, PCI-DSS 11.3.1 requires at least annual penetration tests on internal and external systems. Others not so much – for example, PCI 6.4.1 requires separate access controls between test and development systems. Widely different.
Trying to forecast what the auditor wants to see can be difficult. If you are lucky, over time, you build a relationship with your auditor, which helps you understand their thought processes and how they define success.
Externally Exposed Assets Add Considerable Risk
Externally exposed assets, typically not easily tracked or tested, introduce substantial risk to an organization. Many IT teams are acutely aware of the challenges associated with managing externally exposed assets:
- Gaps in inventories create uncertainty
- Lack of asset ownership and discovery path information (globally, across parent company and subsidiaries) add delays
- Lack of business context and asset importance underline knowledge gaps
- Lack of visibility into complex risk reduces team credibility
Maintaining a complete external asset inventory is a top priority for any organization, but especially so for one that must align with compliance frameworks. Even one unknown asset with a critical or high-severity issue can introduce uncertainty at a time when every moment is precious.
Continuous Risk Assessments Make Compliance Manageable
Risk assessments are the best way to understand the level of exposure and, consequently, how to manage it. The risk assessment provides the action list needed to develop policies and procedures that act as the foundation of a compliant security program. It also provides a tactical list of issues to resolve immediately. However, unless the issue list is mapped to the compliance framework you are pursuing, it can also result in wasted effort.
Timing and frequency are always a challenge. Annual assessments are interesting but unhelpful, considering that CISA reports that 50% of vulnerabilities are exploited within 48 hours of disclosure. More frequency is better but is costly to maintain and operationalize.
Simplify Compliance Audits with CyCognito
Reducing unknowns, both asset-based and issue-based, is of paramount importance when working with an auditor.
Using CyCognito, governance risk compliance (GRC) teams have confidence they have the full list of externally exposed assets. They are able to quickly assess the current state of exposure, the assets that need immediate attention, where the asset resides in your architecture, and instructions to remediate the issue.
CyCognito provides:
- Industry-leading visibility into organizational structure and externally exposed assets – Ensure your GRC teams have an accurate map to work from.
- Continuous active testing for all exposed assets, including IP-based systems and web applications – Provide the risk visibility required to respond proactively.
- Dynamic mapping of compliance violations – Deliver your team a clear path to resolving issues promptly.
- Broad framework support – PCI-DSS v4, NIST 800-53 R5, NIST 800-171 R2, CIS v8, ISO27001:2022 and ISO27002:2022.
All data is available for local data export and through the CyCognito API, making operationalization both flexible and easy.
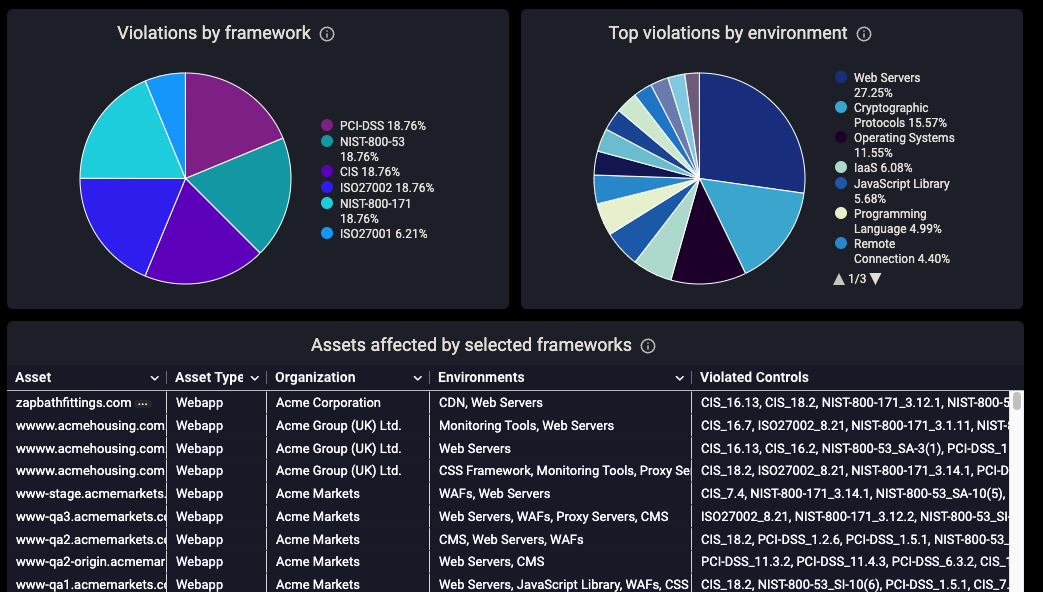
CyCognito provides multiple views into compliance posture. Figure 1 below illustrates the CyCognito compliance dashboard that summarizes the environment state. Links are dynamic, allowing you to click into specifics as needed. The ability to filter by sub-organization is also provided.
Figure 1: CyCognito compliance dashboard summarizing violations globally and per division
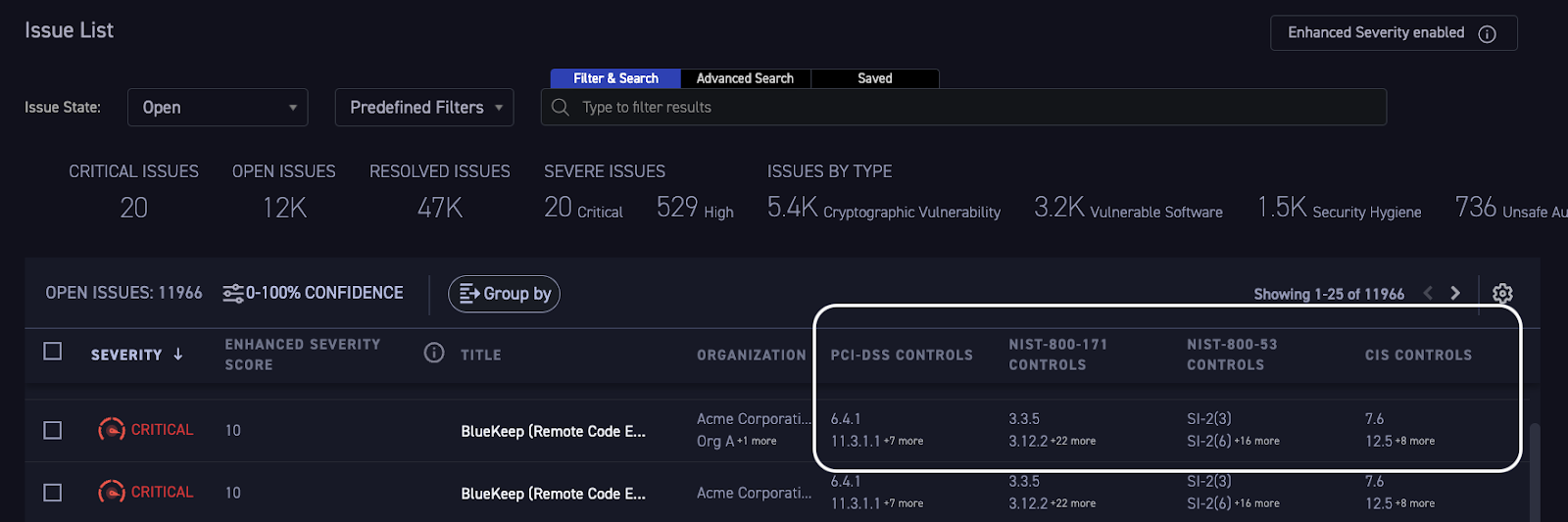
Framework violation details are provided for each issue. Figure 2 shows several of these columns, including a summary and violations per control, available for viewing, download, and via the CyCognito API.
Figure 2: Violation details list for every asset
Find Out More
Failing an audit may have legal or financial implications as well as waste precious IT security team time. Compliance data is currently available to all CyCognito customers. Simply navigate to the Risks page or Compliance dashboard page, available through the home page menu.
CyCognito is a cloud-native software-as-a-service that was built to meet the external risk requirements of the largest and most complex organizations. If you are not a CyCognito customer and want to find out more about how we can help streamline your audit process, please contact us.
Jason Pappalexis has worked professionally in cybersecurity for over 18 years in roles that include security administration for the US government, 3rd party testing, solutions architecture, product management, and technical product marketing.









 Attack Surface
Attack Surface