ESG Report
Gaps in Attack Surface Monitoring and Security Testing for Cyber-risk Mitigation

Why is attack surface monitoring so critical? To paraphrase an old business adage, “You can’t manage what you can’t measure.”
Download the report to learn why security testing and attack surface monitoring work hand in hand.
A Sneak Peak at the Data
Attack surface monitoring helps organizations discover and monitor all the assets connected to their networks regardless of their location—in the DMZ, in public clouds, on third-party networks, etc.
By discovering and monitoring these assets, security professionals can then find the “path of least resistance” and vulnerabilities that hackers may use as a doorway to penetrate corporate networks and commence a cyber-attack. Armed with this intelligence, security teams can develop countermeasures, fine-tune security controls, and monitor signals that may indicate an attack in progress.
Key take-aways:
- Attack surface monitoring is critical but incomplete
- Organizations focus only on the known attack surface
- Attack surface testing remains separate and periodic
- A continuous closed-loop attack surface monitoring and security testing process is needed
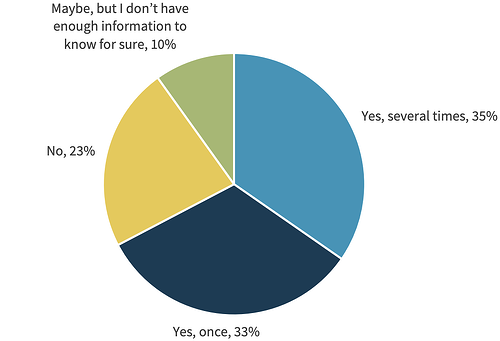
Over 2/3 of organizations report they experienced cyber-attacks that originated from an unknown, unmanaged, or poorly managed company asset (see chart below). More surprising – 75% say they believe it will happen again!