Vulnerability management is a comprehensive approach to identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software they run. It involves a continuous cycle of discovery, prioritization, and remediation to protect an organization’s digital assets from potential threats.
The process begins with the identification of vulnerabilities, followed by their assessment and prioritization based on the level of risk they pose to the organization. Subsequently, appropriate measures are taken to mitigate or eliminate the identified vulnerabilities.
Vulnerability management lies is a proactive security practice, aiming to prevent breaches and compromises before they occur. By implementing a systematic approach to vulnerability management, organizations can stay ahead of potential threats, minimize the attack surface, and maintain a secure digital environment for their operations.
This is part of an extensive series of guides about information security.
The Need for a Vulnerability ManagementSystem
Cyber Threat Landscape Evolution
The rapid evolution of the cyber threat landscape has made vulnerability management more critical than ever. With more sophisticated cyber attacks and the increasing interconnectedness of digital systems, organizations have many new attack surfaces that can be exploited by threat actors. Vulnerability management enables organizations to identify these attack surfaces and stay resilient in the face of constantly changing attack vectors and techniques.
Regulatory Compliance
In recent years, there are more government regulations and industry standards related to data protection and cybersecurity. Many standards, such as GDPR, HIPAA, and PCI DSS, require robust vulnerability management practices to ensure the security and privacy of sensitive data.
Failure to comply with these regulations and standards can result in severe penalties and reputational damage for organizations. Therefore, a vulnerability management system is important for maintaining compliance and demonstrating a commitment to security.
Asset Visibility
Organizations often struggle to maintain an accurate inventory of their digital assets, including hardware, software, and network components. It is particularly difficult to identify assets outside the organization’s control, such as cloud services.
Without a clear understanding of their asset landscape, organizations are unable to assess the potential impact of vulnerabilities and prioritize remediation efforts effectively. A robust vulnerability management system provides the necessary visibility, making it possible to identify and mitigate vulnerabilities across the entire infrastructure.
Risk Management
Vulnerability management is inherently tied to risk management, as it involves the assessment and mitigation of potential security risks within an organization’s digital ecosystem. By systematically addressing vulnerabilities, organizations can reduce the likelihood of security incidents and their associated impact.
This proactive risk management approach helps organizations allocate resources efficiently, focusing on the most critical vulnerabilities that pose the highest risk to their operations. Furthermore, it allows organizations to make informed decisions regarding their security posture and investment in mitigating potential threats.
The Vulnerability Management Process
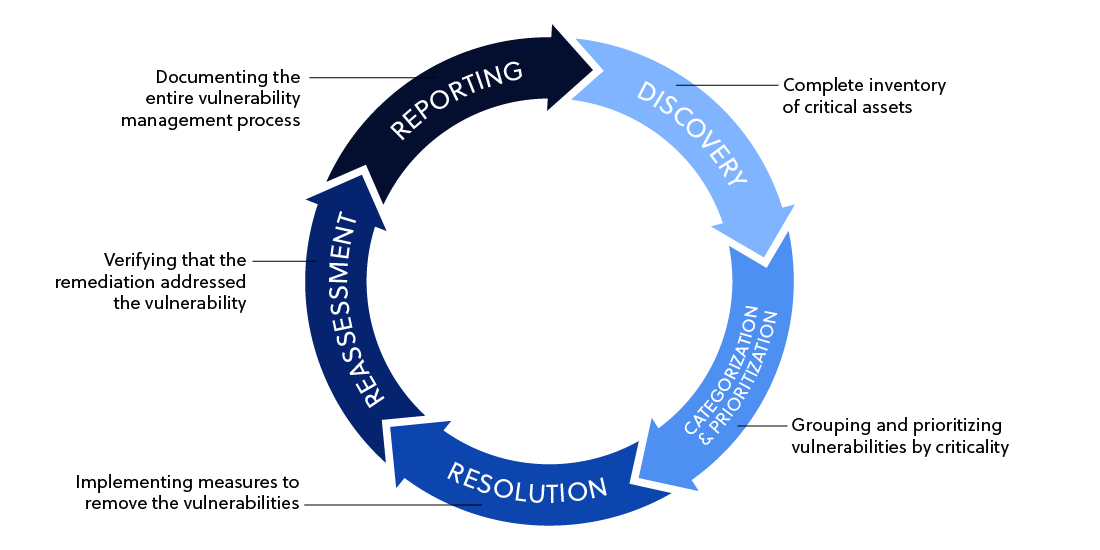
1. Discovery
The discovery phase is the first step in the vulnerability management process. First, It’s important to have a comprehensive inventory of your IT assets, as this will ensure that no area of your network is left unchecked. Don’t forget about digital assets that are outside your organization’s direct control, but are still part of your business operations.
Once you have an inventory of assets, you’ll use various tools and technologies to search for known vulnerabilities within each system. Once the vulnerabilities are identified, they are documented for further analysis.
The discovery phase is an ongoing process that should be carried out regularly to ensure that new digital systems, attack surfaces, and vulnerabilities are identified promptly. Regular scans and assessments are essential because new vulnerabilities emerge every day, and an unaddressed vulnerability could be a potential entry point for a cybercriminal.
2. Categorization and Prioritization
After the discovery phase, the next step in the vulnerability management program process is to categorize and prioritize the identified vulnerabilities. Categorization involves grouping the vulnerabilities based on various factors such as the type of vulnerability, its impact, the system it affects, among others. This categorization helps in understanding the nature of the vulnerabilities, hence informing the resolution process.
Prioritization is crucial to determine the order in which the vulnerabilities should be addressed. Prioritization typically depends on the severity of the vulnerability, their potential impact on the system, and their exploitability. Critical vulnerabilities that could have a significant impact on the system and are easy to exploit are usually given top priority.
3. Resolution
The resolution phase is the process of remedying the identified vulnerabilities. This phase involves implementing measures to remove the vulnerabilities or reduce their potential impact on the system. The resolution process may involve patching, system configuration changes, or even system upgrades.
One crucial aspect to note during the resolution phase is that it should be carried out carefully to avoid introducing new vulnerabilities into the system. Therefore, any changes or modifications made to the system should be tested to ensure they don’t compromise the system’s security.
4. Reassessment
Reassessment involves verifying that the implemented measures effectively address the vulnerabilities. This involves re-scanning the system to ensure that the vulnerabilities have been correctly fixed and that no new vulnerabilities have been introduced during the resolution process.
Reassessment is crucial as it confirms the effectiveness of the resolution process. It also ensures that the system is secure and free from the identified vulnerabilities.
5. Reporting
The last phase in the vulnerability management program process is reporting. This involves documenting the entire vulnerability management process, from discovery to reassessment. The report should detail the identified vulnerabilities, their categorization and prioritization, the implemented resolutions, and the reassessment results.
Reporting is crucial for accountability and future reference. It provides a historical record of the organization’s vulnerability management efforts, which can be useful in future vulnerability management processes or audits.
Tips from the Expert

Dima Potekhin, CTO and Co-Founder of CyCognito, is an expert in mass-scale data analysis and security. He is an autodidact who has been coding since the age of nine and holds four patents that include processes for large content delivery networks (CDNs) and internet-scale infrastructure.
In my experience, here are tips that can help you better optimize your vulnerability management strategy:
- Leverage asset criticality over CVSS scores: When prioritizing vulnerabilities, go beyond CVSS scores by considering the criticality of the affected asset. A low-severity vulnerability on a mission-critical asset might be more dangerous than a high-severity issue on a less important system.
- Implement a vulnerability exception process: Not all vulnerabilities can or should be remediated immediately. Establish a formal process for documenting, justifying, and approving exceptions, while also setting up regular reviews to ensure the rationale remains valid.
- Analyze post-remediation security incidents: After remediating vulnerabilities, closely monitor related systems for any security incidents. This helps in identifying any residual issues or new vulnerabilities introduced during the fix.
- Maintain an “exploit watchlist”: Keep track of emerging exploits for known vulnerabilities in your environment. This allows you to react quickly if an exploit is weaponized in the wild, even for lower-priority vulnerabilities.
- Establish a strong communication protocol with stakeholders: Ensure that there is a clear, established line of communication between IT, security, and business units. This helps in effectively prioritizing and communicating the impact of vulnerabilities, especially in high-pressure situations.
Vulnerability Management Tools andTechnologies
Attack Surface Management
Attack surface management is a critical component of vulnerability management. It involves the identification, classification, and monitoring of all the digital assets of an organization that could potentially be targeted by cyber attackers. This includes not only the visible and known parts of a network, like servers and endpoints, but also often overlooked elements such as unused ports, outdated applications, and shadow IT systems.
The primary goal of attack surface management is to minimize the opportunities for attackers to exploit vulnerabilities. This is achieved by continuously discovering, assessing, and securing all the exposed assets of an organization. One key challenge in this process is keeping up with the constantly evolving nature of an organization’s digital footprint, especially with the adoption of cloud services, mobile devices, and the Internet of Things (IoT).
Automated Vulnerability Scanners
Automated vulnerability scanners, which are typically a part of attack surface management but can also be used on their own, scan a system or network for known vulnerabilities. They are crucial in the discovery phase of the vulnerability management program process as they help identify the vulnerabilities present in the system.
Automated vulnerability scanners offer several advantages. They are fast, efficient, and can scan large systems within a short time. They also reduce the chances of human error, which can occur during manual vulnerability scanning. However, automated scanners typically cannot identify complex or unknown vulnerabilities.
Security Information and Event Management (SIEM) Systems
Security Information and Event Management (SIEM) systems collect and analyze security event data from various sources within an organization’s network. They provide real-time analysis of security alerts, which can help identify possible exploitation of security vulnerabilities as they happen. SIEM systems can also help with categorization and prioritization of vulnerabilities, by providing valuable insights into real security incidents.
Configuration Management Tools
Configuration management tools play a vital role in vulnerability management by helping organizations maintain a consistent, secure, and up-to-date configuration of their IT assets. These tools track and control changes in system configurations, ensuring that all systems conform to predetermined security policies and standards. By doing so, they not only reduce the risk of configuration-related vulnerabilities but also make it easier to revert changes in case of an identified security risk.
Configuration management provides a comprehensive view of the organization’s IT environment, facilitating the identification of unauthorized changes that could introduce vulnerabilities. This proactive approach to managing system configurations is crucial in preventing security breaches and maintaining the integrity of the IT infrastructure.
Patch Management Software
Patch management software is essential in the resolution phase of the vulnerability management process. It automates the task of keeping software and systems up to date with the latest patches, which are crucial for fixing security vulnerabilities. Patch management tools identify missing updates in the organization’s systems and facilitate their deployment, ensuring that vulnerabilities are addressed promptly and efficiently.
These tools typically provide features like scheduling patch deployments, testing patches before full deployment, and reporting on patching status. Efficient patch management reduces the window of opportunity for cyber attackers to exploit known vulnerabilities, significantly reducing the attack surface.
Learn more in our detailed guide to vulnerability management tools (coming soon)
Challenges in Vulnerability Management
Scaling with the Growing Number of Assets
As organizations grow and evolve, so do their assets. This includes not just physical assets, such as servers and workstations, but also virtual and cloud-based assets. Each new asset introduces potential new vulnerabilities that must be managed and mitigated.
The sheer volume of assets can be overwhelming, making it difficult to keep track of them all. This is compounded by the fact that assets often change, with new ones being introduced and old ones being decommissioned. This is especially true in cloud and containerized environments. Furthermore, each asset type may require different vulnerability management approaches, adding to the complexity.
To overcome this challenge, organizations need to have a clear and up-to-date inventory of all assets. This includes information about the asset’s type, location, owner, and other relevant details. They also need to have a process in place for regularly updating this inventory to reflect changes in their asset base.
Keeping Pace with New Vulnerabilities
Another significant challenge in vulnerability management is keeping pace with new vulnerabilities. Cybercriminals are always on the lookout for new ways to exploit systems, and they often find them. According to the National Vulnerability Database, thousands of new vulnerabilities are discovered each year.
The challenge of keeping pace with new vulnerabilities is exacerbated by the speed at which they are discovered and exploited. New vulnerabilities can be exploited within days or even hours of its discovery. This leaves organizations with very little time to react.
To cope with this challenge, organizations should use vulnerability management tools that receive real time threat intelligence updates, and are also able to detect unknown or zero day threats.
Reducing False Positives and Negatives
False positives occur when a system incorrectly identifies a harmless activity as a vulnerability. This can lead to wasted resources, as security teams rush to address a non-existent threat, and over time can lead to alert fatigue.
False negatives occur when a system fails to identify a real vulnerability. This can be even more dangerous, as it leaves organizations exposed to potential attacks.
Both false positives and negatives can be reduced by improving the accuracy of vulnerability detection tools and processes. This requires regular testing and calibration to ensure that they are functioning as intended.
Managing Vulnerabilities in Hybrid Environments
Hybrid environments, which combine on-premises infrastructure with cloud-based services, present unique challenges for vulnerability management. These environments typically feature a mix of legacy systems and modern cloud applications, each with distinct security considerations.
In hybrid environments, vulnerabilities can arise from multiple sources, including misconfigured cloud services, outdated on-premises software, or integration points between cloud and on-premises systems. To effectively manage these vulnerabilities, organizations must have a unified vulnerability management strategy that encompasses both cloud and on-premises components.
This strategy should include regular assessments of cloud configurations, consistent application of security patches across all environments, and thorough monitoring of data flows between different systems. Additionally, special attention should be given to compliance and data protection requirements, as hybrid environments often involve the storage and processing of sensitive data across multiple jurisdictions.
Best Practices in Vulnerability Management
Here are some critical best practices that will help you effectively manage security vulnerabilities.
Ensure Cross-Departmental Collaboration
Vulnerability management is not just the responsibility of the IT department. It involves all departments and levels of the organization. This means that everyone, from top management to frontline employees, needs to understand the importance of vulnerability management and their role in it. It also means that different departments need to work together to identify, assess, and mitigate vulnerabilities.
Integrated Threat Intelligence
To effectively manage vulnerabilities, organizations need to stay informed about the latest threats and vulnerabilities. This is where integrated threat intelligence comes into play. By leveraging threat intelligence, organizations can gain insights into the tactics, techniques, and procedures (TTPs) used by threat actors, helping them proactively defend against potential attacks.
Threat intelligence can provide valuable information about new vulnerabilities, emerging threat trends, and the most targeted assets. By integrating this intelligence into their vulnerability management process, organizations can make more informed decisions about prioritization and remediation strategies.
Proactive Zero-Day Vulnerability Management
Zero-day vulnerabilities, which are either unknown to the public and software vendors, or disclosed but a patch is not yet available, pose a significant risk to organizations. To effectively manage zero-day vulnerabilities, organizations must adopt a proactive approach. This involves closely monitoring security advisories, staying informed about the latest vulnerabilities, and promptly applying patches or implementing workarounds when they become available.
Additionally, organizations should consider leveraging vulnerability management solutions that provide proactive scanning capabilities. These solutions use advanced techniques such as behavior analysis and machine learning to identify and mitigate zero-day vulnerabilities before they are exploited.
Red Team Exercises and Attack Simulation
In addition to the practices mentioned above, conducting red team exercises and attack simulations can significantly enhance an organization’s vulnerability management program. These activities simulate real-world attack scenarios to identify vulnerabilities and test the effectiveness of existing security controls.
Red team exercises provide a realistic assessment of an organization’s security posture, helping identify areas of weakness that may not be apparent in regular vulnerability assessments. On the other hand, attack simulations can help validate remediation efforts and ensure that vulnerabilities have been effectively addressed.
Learn more in our detailed guides to:
- Vulnerability management best practices (coming soon)
- Vulnerability management metrics (coming soon)
Vulnerability Management with CyCognito Attack Surface Management Platform
The CyCognito platform addresses today’s vulnerability management requirements by taking an automated multi-faceted approach in identifying and remediating critical issues based on their business impact, rather than focusing on the generic severity of the threat alone. To do this you need a platform that is continuously monitoring the attack surface for changes and provides intelligent prioritization that incorporates organizations context.
The CyCognito platform addresses today’s vulnerability management requirements by:
- Maintaining a dynamic asset inventory with classification of the entire external attack surface, including exposed on-premise and cloud-hosted assets like web applications, IP addresses, domains and certificates, eliminating the need to rely on outdated or incomplete information from collaboration tools, spreadsheets, or emails. This approach significantly reduces the burden of tedious, error-prone and costly processes.
- Actively testing all discovered assets to identify risk. Active testing, including dynamic application security testing, or DAST, uncovers complex issues and validates known issues, with low false positives. Each exploited asset is assigned a security grade based on its criticality to the business.
- Prioritizing critical issues, guiding security teams to focus on the most urgent threats. Our unique risk-based prioritization analysis goes beyond the common vulnerability scoring system (CVSS), and incorporates factors like asset discoverability, asset attractiveness, exploitability, business impact and remediation complexity. Integrated tactical threat intelligence identifies the handful of attack vectors that pose the greatest risk.
- Streamlining communications between remediation teams by providing comprehensive, verifiable evidence for each exploited asset. This evidence includes detailed risk assessments, asset ownership information, and actionable remediation guidance. The platform seamlessly integrates with SIEM, SOAR and ticketing system tools like Jira, ServiceNow and Splunk to facilitate information sharing and collaboration.
See Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.
Vulnerability Assessment
Authored by CyCognito
- [Guide] Vulnerability Assessment: Process, Challenges & Best Practices
- [Guide] Complete Guide to Vulnerability Scanning
- [Product] CyCognito | Proactively Secure Your Attack Surface
DRPS
Authored by CyCognito
- [Guide] What Are Digital Risk Protection Services (DRPS)?
- [Guide] How Domain Spoofing Works and 8 Ways to Prevent It
- [Research Report] 2024 State of External Exposure Management Report
- [Product] CyCognito Attack Surface Management | Comprehensive Attack Surface Management Solutions
WAF
Authored by Radware












