What is Vulnerability Prioritization?
In a perfect world, security teams could use a straightforward process to remediate vulnerabilities, such as “first in, first out” or FIFO. Grocery stores use this method for milk; the oldest milk in inventory gets sold first. But really, milk isn’t the analogy we need to understand “what is vulnerability prioritization.” Instead, let’s consider a hospital emergency room.
In an emergency room, patients are triaged based on the severity of their injury or illness. The most critical patients are seen first, even if they arrived at the hospital later than other patients. This is because the most critical patients are at greater risk of dying if they don’t receive treatment right away.
Just like a hospital emergency room, security teams have limited resources. They can’t fix all the vulnerabilities that they know about. They have to prioritize their efforts and focus on what’s most important.
What is Vulnerability Management Prioritization in Cybersecurity?
Vulnerability management prioritization in cybersecurity refers to ranking vulnerabilities or exposures on software, hardware or systems. Prioritization is a means to resolve the most important vulnerabilities first and deal with a constantly growing number of vulnerabilities.
The frequency and sheer number of vulnerabilities being disclosed has shot up in recent years. Let’s consider a 20 year period from 2002 to 2022. In 2002, there were 1,000 CVEs (common vulnerabilities and exposures) disclosed monthly; in 2022 that skyrocketed to an average of 23,000 CVEs per month.1 According to CyCognito’s research, the average enterprise contends with 345 new ‘critical’ threats every month.2 Even the worst of the vulnerabilities are still too many to confront.
The vulnerability management process in cybersecurity is complex and involves part art and part science. There’s also a lot to consider, including impacts to the business, customers, compliance regulations and the health of critical systems.
Vulnerability Scanning Vendor Prioritization
Given the complexity of vulnerability prioritization, there really are no standards for determining how you should prioritize. Industry analysts like Gartner or training groups like the SANS Institute do provide some guidance. Most agree that taking a risk-based approach to prioritization is best, but even that has nuances such as the size of your risk appetite and how you define risk.
Vulnerability scanning vendors can provide detailed information about identified vulnerabilities, including their severity and exploitability. However, they tend to only review assets you tell them to scan, often by providing an IP address or other location information. Additionally, they also are typically limited to very few contextual details about the affected asset. Contextual details include things like what software or services are running, what other assets it technically links to, if it is connected to data and if the data is sensitive.
While vulnerability scanning vendors can provide value, it’s important to understand how they find assets and how they align to your organization’s goals for prioritizing vulnerabilities.
Why Vulnerability Prioritization is Important
Prioritizing and remediating crucial security vulnerabilities is important because it helps reduce the attack surface exposures attackers can use to exploit sensitive data, cause service disruptions, violate compliance requirements or cause reputational harm.
Vulnerability prioritization also helps to ensure resources are focused on the right issues and the most critical and high vulnerabilities are being addressed. Some compliance frameworks require a vulnerability management program and vulnerability prioritization in cybersecurity is an essential part of this process.
How Does a Vulnerability Prioritization Matrix Work?
A typical vulnerability prioritization matrix is a tool used by security teams to consider the cross-section of vulnerability factors to prioritize according to their risk tolerance. A basic prioritization matrix can be made by considering the intersection of both severity and probability.
Assigning severity or probability can be based on a single factor or a formula that assigns weights to several factors. It’s important that the formula you use aligns to your organization’s business and systems.
Severity considers the technical severity, such as CVSS (common vulnerability scoring system) score, which assigns a 0-10 numerical value to compare the severities. CVSS also looks at if the vulnerability would enable the attacker to propagate across systems.
Probability considers how easily the vulnerability can be exploited by attackers. When considering ease, how complex the vulnerability is or if it requires privileges to exploit can be primary factors.
A vulnerability matrix based on severity and probability might look like Figure 1 below. Severity is the X axis and the columns align to CVSS ratings from Low to Critical. Probability is the Y axis and the rows are Top to Bottom.
This example of a vulnerability matrix shows that while there are 345 vulnerabilities with a critical severity score, only 120 are top priority. Focusing on these top priority critical severity vulnerabilities helps focus immediate attention on the top 35% of critical vulnerabilities. Regardless of the priority, the vulnerability matrix helps to make more informed decisions.
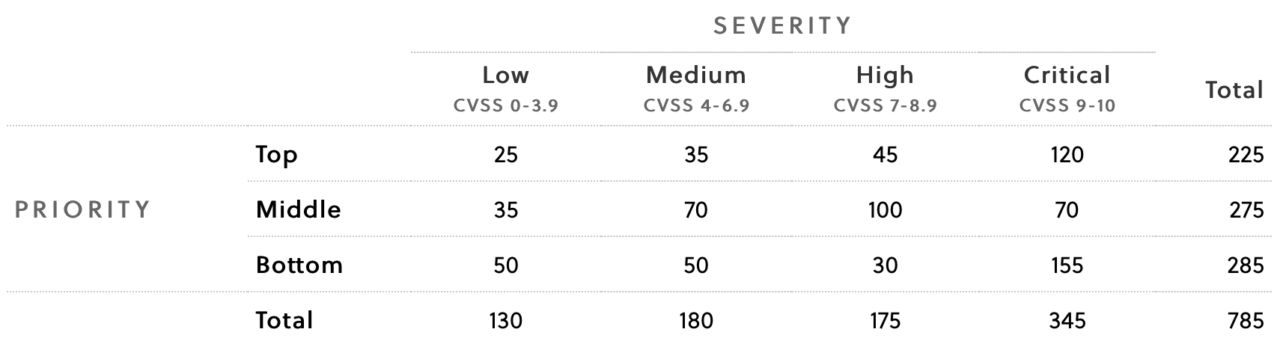
Figure 1: A vulnerability prioritization matrix with two factors, severity and priority.
Impact is commonly a formula that considers the potential damage to a particular system or how many systems could be affected.
A vulnerability matrix can be expanded to consider a third factor. In Figure 2, we show an example of adding the factor “Impact” with values of “High”, “Medium” and “Low”. The formula for Impact accounts for the potential damage a vulnerability could cause to the organization.
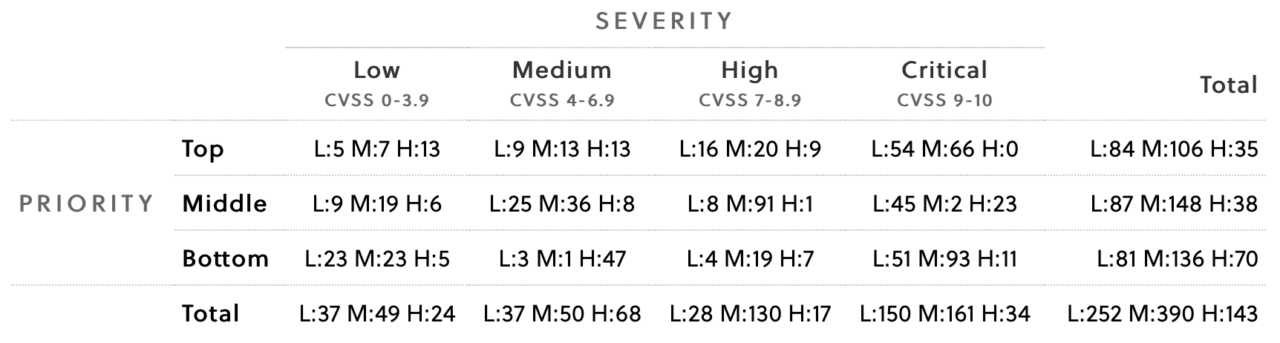
Figure 2: A vulnerability matrix with three factors: severity, priority and impact.
Let’s take a look at how to calculate some other factors and what they mean.
Calculate Vulnerability Score: Unraveling Digital Weakness
A vulnerability score is a combination of factors, typically calculated based on a formula of weighted attributes. Typical factors in calculating the score include the severity of the vulnerability, its potential impact, and how easy it is to exploit.
Calculate Asset Risk Score: Decoding Digital Peril
The score is a numerical value that assesses what the asset exposes, including sensitive data the asset contains or critical systems it can provide access to. An asset risk score can be used to identify assets that need greater protection or deeper security assessment like dedicated penetration testing.
Risk Attribute Weights: Balancing Cyber Defenses
Risk attribute weights help to assign relative importance to various factors. When considering the vulnerability score and the asset risk score, the overall score should be weighted using a formula to properly balance the importance of the asset at risk, be that it contains sensitive data or is a critical system. Highly important and sensitive asset risks may warrant higher prioritization even if the vulnerability is considered low or unlikely.
Automate Vulnerability Prioritization: Unleashing Efficiency
Manual vulnerability prioritization is time consuming and error prone. And once prioritization is done, you’re then off to manage the remediation process, which we discuss in more detail in this blog on vulnerability remediation.
The tables mentioned earlier quickly become complex with just a third factor added. As we’ll discuss shortly, keeping prioritization up-to-date is important yet hard to do with today’s constantly changing IT infrastructure.
CyCognito provides an attacker’s perspective of your attack surface to help uncover unknown, unmanaged assets and uses active security testing to discover vulnerabilities. With CyCognito’s automation, information about the vulnerability, the asset, and attacker insight and other factors contribute to vulnerability priorities. They are also kept up-to-date and assessed on a routine, even weekly cadence.
Examples of Adapting to Vulnerability Prioritization Techniques
Previously we discussed using a vulnerability prioritization matrix to assess the intersection of a few factors. Now let’s consider a few other prioritization techniques.
Vulnerability disclosure date. Each vulnerability with a CVE number has a disclosure date. Some vulnerabilities that exist in your environment may have been disclosed several years ago and thus, a cut-off based on disclosure date could establish which vulnerabilities to prioritize.
Compliance requirements. Governing bodies establish requirements and they typically apply to specific industries. Health Insurance Portability and Accountability Act (HIPAA) is a federal law designed to protect the privacy and security of patient health information and Payment Card Industry Data Security Standard (PCI DSS) is a set of standards for payment cardholder data security. These are just examples and there are others. Most compliance requirements mandate scanning for and remediating vulnerabilities and some may require specific security controls to be in place.
Application type or system architecture. Certain infrastructure inherently has a high likelihood of attack. Web applications, for example, are generally accessible to anyone with an internet connection and can be the front door for attackers to reach sensitive data. When prioritizing vulnerabilities of a particular type of asset, consider if there are common configuration issues that could be addressed by a team training for asset owners. Figure 3 shows how web apps are viewed in the Cycognito platform.
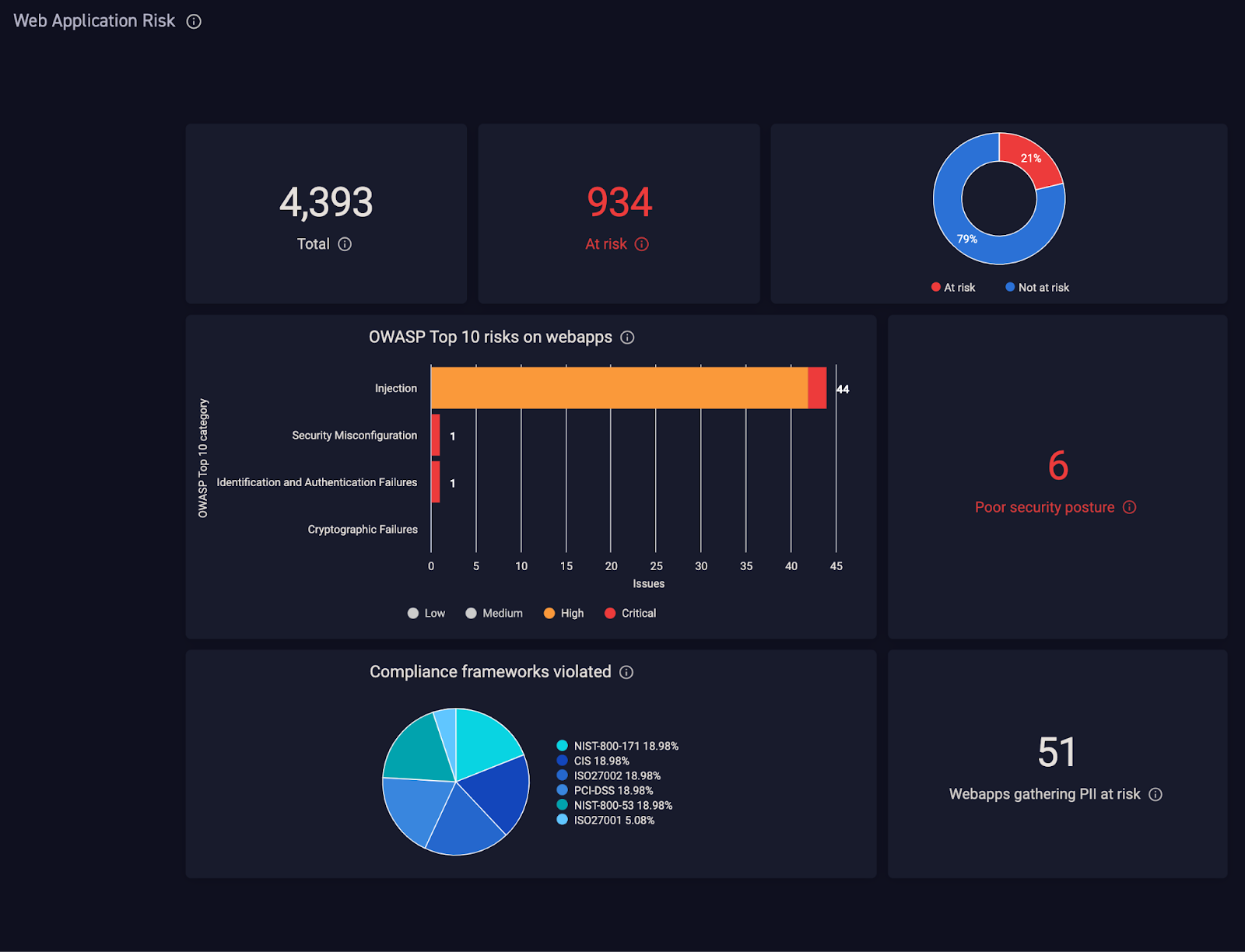
Figure 3. Some types of assets, like web applications, benefit from having their vulnerabilities evaluated and prioritized separately. CyCognito’s Web Application Risk dashboard examines and prioritizes just vulnerabilities affecting web applications.
Ease of remediation. Prioritizing vulnerabilities based on how easy they are to remediate might be the best way to reduce the overall vulnerabilities fastest and possibly with less resources. This could mean focusing on vulnerabilities that are better-documented or don’t require special expertise to remediate. Some vulnerabilities require a hardware upgrade whereas ones that just need a patch could be faster, cheaper and more immediately beneficial to remediate.
These are just examples of techniques that can help your prioritization strategy. Keep in mind that combining factors and techniques makes the biggest impact. A word of caution: while it’s easy to focus on reducing the overall number of vulnerabilities, make sure you’re prioritizing risks to the business. The primary goal is to safeguard your organization’s core intellectual and electronic assets. Better understanding the parts of the business assets support and what information they connect to can play a critical role in vulnerability prioritization. Once your vulnerabilities are prioritized, read our blog on vulnerability remediation to understand the next steps to take action.
Vulnerability Prioritization Challenges
Some of the biggest challenges in vulnerability prioritization are driven by having incomplete asset inventories, having incomplete data about assets or not prioritizing based on the right factors. The data below shows the impact of these challenges.
For the worse. Helpful stats on past breaches reveal that 60% of breaches occurred because of vulnerabilities that went unpatched,3 even though a patch was available. It’s been commonly reported that attackers are exploiting CVEs that were disclosed as many as 7 years prior. These statistics demonstrate that assuming old vulnerabilities don’t matter is bad practice and that prioritizing what really matters is a tough challenge.
For the better. There is hope: a recent report by CyCognito explained that additional context beyond simply the CVSS score helped lower the priority on 35% of issues. A small 2% were given increased priority. With the right context, your prioritization efforts can go beyond the severity of the vulnerability and look at the actual exposed risk. The result can be fewer high priority issues, saving time and resources while keeping the organization safe. Figures 4 and 5 show some of the ways the CyCognito platform helps to view vulnerabilities.
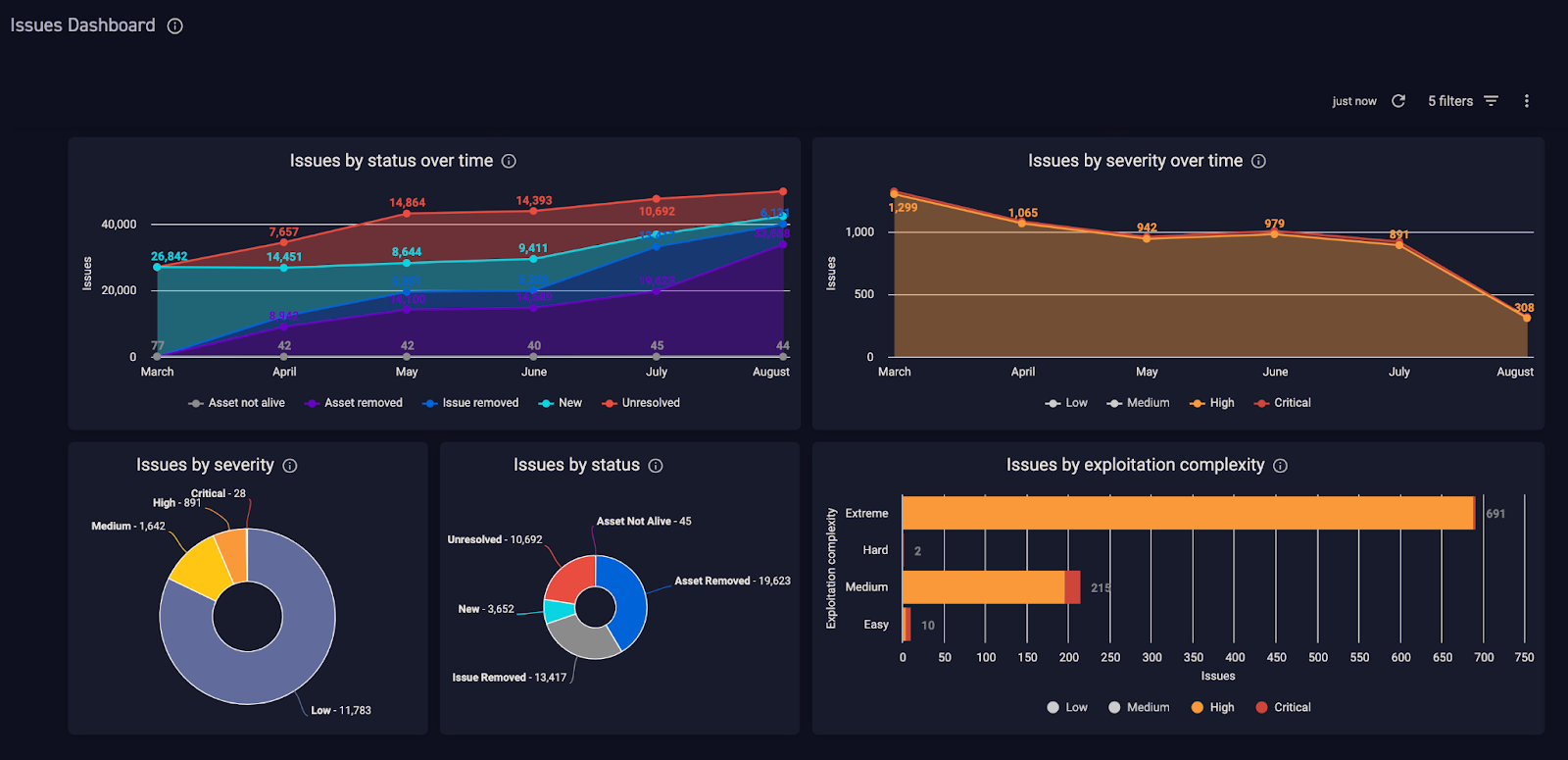
Figure 4. The CyCognito platform’s Issue Dashboard shows several ways to evaluate issues, including severity, status, and exploitation complexity.
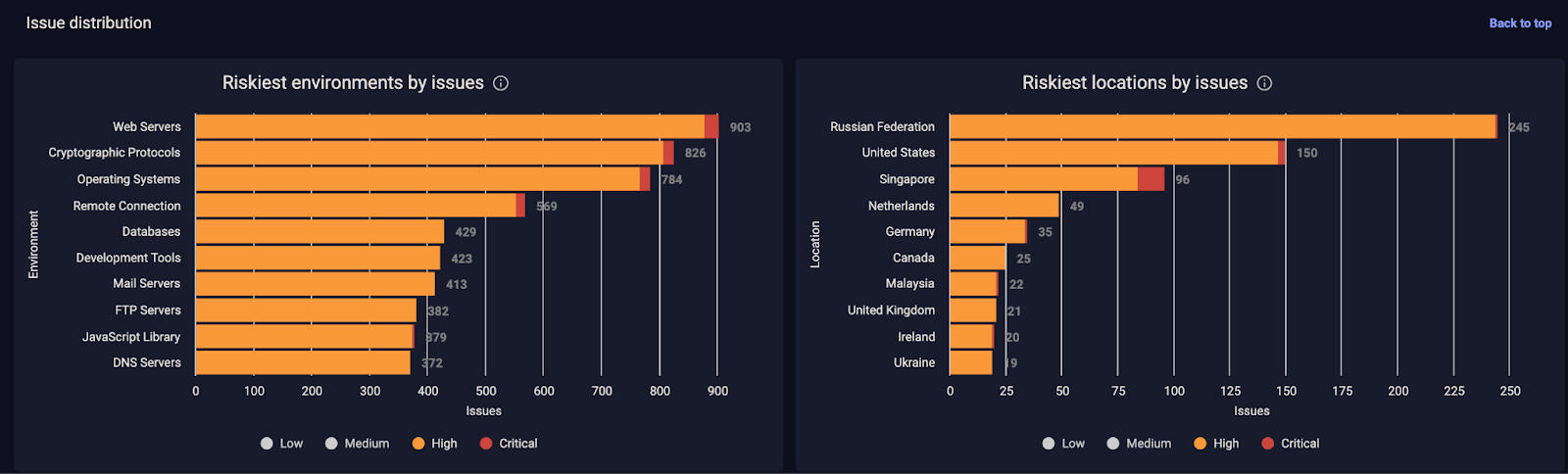
Figure 5. The affected environment or location may also inform vulnerability prioritization.
Key Factors for Effective Vulnerability Prioritization
Let’s consider five important key factors to consider when building your formula for vulnerability prioritization should include:
- Potential impact of an exploited asset, considering both the technical and business impact.
- Business context about the asset will help you understand how interesting it is to attackers.
- Exploitation complexity helps to know which vulnerabilities are easiest to exploit and are likely to be within an attacker’s path of least resistance.
- Discoverability to know how easy it is for an attacker to find the asset and associate it with the organization.
- Remediation effort to know the effort and skill level required to fix the vulnerability.
Weighing these criteria as part of your scoring system formula can help effectively prioritize vulnerabilities for accelerated remediation.
How to Prioritize Vulnerabilities Properly
Attackers are looking at your organization trying to find weak spots or vulnerabilities that allow them a way in. Most often, attackers are looking for the easiest way in and that path might not be the front door. It might be through a separate business unit, a branch location or recent acquisition.
This is why the CyCognito platform maps your external attack surface and helps you identify your externally exposed risks.
Identify Critical Assets
Maintaining an accurate inventory of assets is difficult; a recent report by CyCognito findings discovered Fortune 500 organizations are unaware of 10% to 30% of their own business units, brands or branches.
CyCognito’s discovery begins by mapping the entire organization. The next step is to discover all assets associated with each entity, identifying all assets across your entire external attack surface.
Identify Vulnerabilities
Identifying vulnerabilities can be done a number of ways, but not all are equal. It’s important to assess all your assets on a regular basis. The CyCognito platform helps you more thoroughly assess vulnerabilities by performing active security testing across all live assets.
An important consideration is how frequently you are assessing your attack surface because the size of environments fluctuates larger and smaller, as much as 10% per month. Bear in mind that cloud environments can change rapidly, often daily.
Categorize and Prioritize Vulnerabilities
To assess asset risk, it’s important to have contextual information about the asset including the applications, operating system or services that are running on it and what data it might provide access to. This context will help you assess the exposed risk created by the vulnerability.
CyCognito helps you to prioritize vulnerabilities according to risk exposure they create. CyCognito’s Exploit Intelligence enhances risk prioritization by incorporating threat intelligence to understand attacker activity on the exploit in the wild.
Implement Fixes & Mitigations
Mitigating risk exposure and fixing vulnerabilities takes communication and coordination. As you read our blog on vulnerability remediation, pay close attention to techniques to implement a program using best practices and metrics to help monitor the effectiveness of your program.
CyCognito helps automate remediation steps to accelerate the process by integrating with ticketing systems, SIEMs and various vulnerability management platforms. Step-by-step guidance to fix the vulnerabilities and evidence of findings are automatically made available to help teams resolve issues quickly with confidence.
Monitor and Retest for Vulnerabilities
Once the vulnerabilities are resolved, it’s important to retest and revalidate the vulnerability is no longer there. By continuously assessing your external attack surface management, you can monitor for any new vulnerabilities as changes are made throughout your organization, be that in the cloud, at a remote location or anywhere IT assets are made available to the internet.
Learn more about how CyCognito can help you prioritize vulnerabilities.
Explore the CyCognito platform with a self-guided, interactive dashboard product tour. To speak with one of our experts to discuss how the CyCognito platform can help you prioritize your vulnerabilities according to your external risk exposure, schedule a vulnerability prioritization demo now!
Sources:
- https://www.iamagazine.com/markets/1-900-new-cyber-vulnerabilities-each-month-in-2023-says-coalition
- https://www.spiceworks.com/it-security/vulnerability-management/guest-article/external-exposure-management-are-your-attack-surfaces-safe/
- https://www.servicenow.com/lpayr/ponemon-vulnerability-survey.html


