The MITRE PRE-ATT&CK framework released in 2017 consisted of 15 tactics and 148 techniques designed to address community concerns about what adversaries are doing before the adversary achieves access.However, it was completely separate from MITRE Enterprise ATT&CK because the Enterprise ATT&CK focused only on the behaviors of attackers after they’ve gotten into an enterprise. On October 27, 2020 that all changed when the MITRE Pre-ATT&CK folded into Enterprise ATT&CK with a concise format of Reconnaissance, Resource Development, and Initial Access that really works!

The reason for the new format is that security practitioners and the team at MITRE observed that a lack of insights into pre-compromise behaviors hindered organizations’ ability to implement controls that mitigate tactics used later in the framework. For me it was also further recognition of the need to shift security posture to the “left” -- meaning earlier in the attack chain, well before the enterprise is compromised -- as a way to keep the bad guys out by knowing what and where they are going to attack before they do. This change to the framework means that the capabilities that the CyCognito platform brings to bear can help you address far more of the tactics in the framework, and really preempt attackers. In other words, we take care of reconnaissance automatically so your organization can focus on remediation, mitigation, and detection at those initial access points in the attack surface.
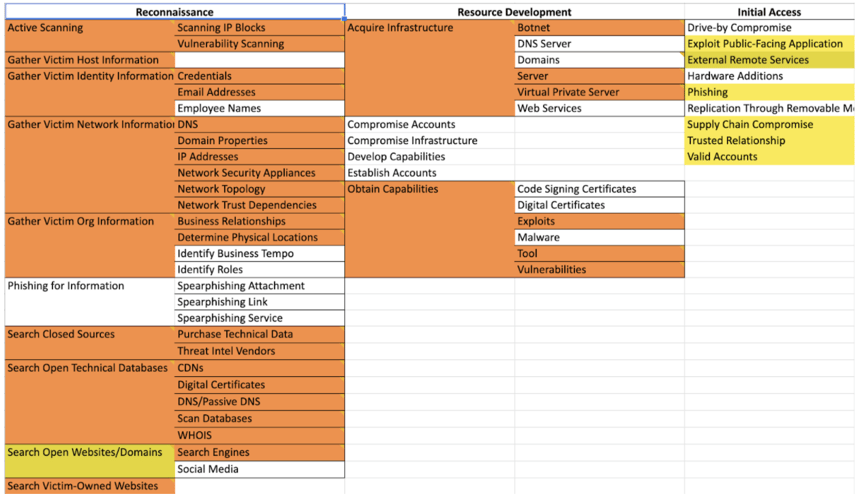
The diagram above shows a snapshot of the techniques CyCognito contributes to in the first three tactics; with orange indicating significant coverage and yellow indicating secondary mapping.
Now I’d like to walk you through the first two tactics in particular, and the remaining in net, and give an overview into how CyCognito can help.
Phase 1: Resource Development
The first phase of MITRE ATT&CK version 8.0 is the Reconnaissance tactic which focuses on a potential attacker gathering information they can use to plan future operations. With 10 techniques and 31 subtechniques this tactic is all about information gathering and is usually undetectable, so mitigation is about limiting the information available. In this phase our secret weapon is human intelligence. Human analysts working off of our customer’s initial request to be targeted by our platform apply their expertise and knowledge to further enhance our platform’s machine learning and data gathering cloud-scaling botnet. By working closely with the system, analysts train it to know our customer’s attack surface so our customers can protect their systems by limiting the information that can be gathered and then remediating, mitigating, and monitoring the assets that are discoverable and most likely to be targeted.
Phase 2: Resource Development
The second phase is the Resource Development tactic where the adversary creates, purchases, or steals resources that can be used in an attack. With six techniques and 26 subtechniques this tactic is about building the capabilities to launch attacks without being detected. But how do you combat attackers in the build stage? At CyCognito we have built the infrastructure necessary to emulate attacker operations, based on nation-state grade architecture, and make it available as an easy-to-adopt cloud-based service. At the center of this capability is our world-class global botnet which uses attacker-like reconnaissance techniques to scan, discover, fingerprint, and classify billions of digital assets all over the world. And because CyCognito works the way adversaries do, no input or configuration are needed. The big difference at the end of the process is that CyCognito tells our customers what we found rather than launch an attack.
Subsequent Phases
All subsequent phases of the MITRE ATT&CK framework go into details about tactics and techniques that can typically be detected through technical means via network or host monitoring. For example, Initial Access might be achieved by Exploiting Public Facing Applications and while CyCognito won’t detect this exploit in real time, the platform will identify vulnerabilities and exposures via external vulnerability scanning and automated pentesting and can suggest assets that should have network segmentation. In all cases, knowing how an adversary sees targeted systems can and should help the security team protect the enterprise and the mission. And by mapping the CyCognito platform detections to MITRE ATT&CK techniques, they will be prioritized appropriately before they become an incident to be handled.
What It Looks Like In Real Life
In practice all assets the CyCognito platform discovers will be reported as part of “reconnaissance.” The discovery path information will group these assets to the technique used, which may be by nine of the 10 techniques (we aren’t Phishing for Information from anyone). To give you an idea of what this discovery information looks like, here is a screenshot from the CyCognito platform on an anonymized asset showing that we Gather Victim Network Information: DNS and then Search Victim-Owned Websites to find associated attack surface assets:
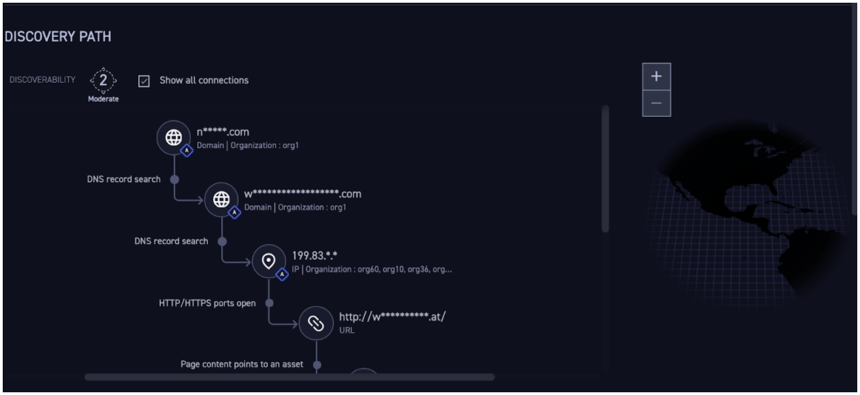
The diagram above shows the “Discovery Path” capability of the CyCognito platform showing automatic DNS record searching, organizational attribution, asset fingerprinting, and web app identification.
What all this means is that you will be able to utilize the CyCognito platform mappings to the MITRE ATT&CK framework to shift your security posture to the left from the bad stuff that occurs after a breach. With our capabilities, you can move to proactive defense before the attack occurs by looking at your network the way the attackers do. So, while these newly formatted PRE-ATT&CK tactics and techniques aren’t something you can easily address with the three traditional controls of detection, prevention, and correction, you can still learn through attack simulation. Even if the simulation of information collection isn’t identical to every scenario you might face (for example, the platform will not be phishing for information), by using the CyCognito platform you’ll understand what attackers are able to collect and how they would collect it. You can then examine these exposures and the information gathered and allow that information to inform prioritization of your security issues, and make better and faster decisions with a laser focus on keeping intruders out.



