The situation in Ukraine highlights that cyber attacks are an integral part of modern warfare and impact organizations outside of the central conflict. As a result, governments and security agencies globally are advising organizations to be prepared for continued attacks related to the current crisis.
Effective immediately, the CyCognito platform is able to help identify and mitigate the gaps used by Russian state-sponsored threat actors. The platform has an Exploit Intelligence Advisory that aligns with CISA Alert (AA22-011A). We are making this Exploit Intelligence Advisory and the Advisory for Log4Shell available free of charge for all CyCognito customers.
About Exploit Intelligence Advisories
As a brief background, CyCognito Exploit Intelligence Advisories provide you with an understanding of all assets susceptible to a particular threat; in this case, Russian state-sponsored cyber threats as described in CISA Alert AA22-011A. Summary results are shown as a pie chart (see image below) that is divided between assets that tested as –
- Vulnerable, or
- Not vulnerable
Advisory Example:
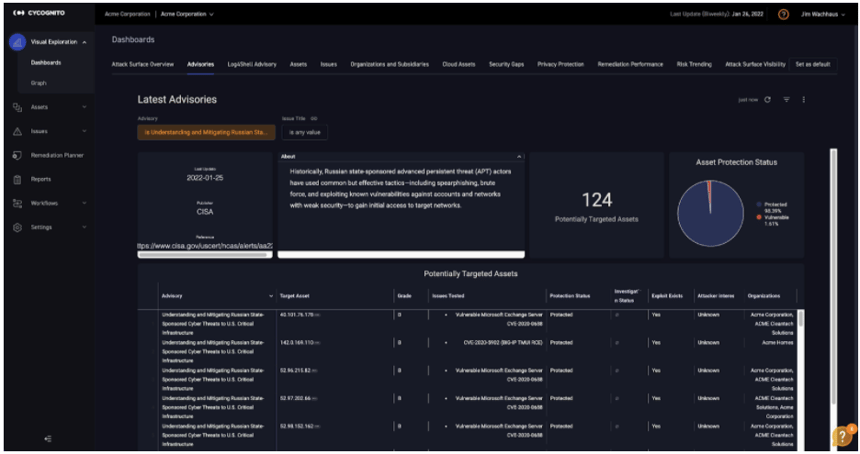
This allows you to see and communicate the domain of potential risk and the range of assets in your attack surface that are currently vulnerable to a cyber attack of the type described in CISA AA22-011A.
As with other security issues detected by the CyCognito platform, a wealth of information is provided to help you operationalize risk management and accelerate remediation. From the Advisory, you can drill down to understand the relevant details and take remediation actions. With Exploit Intelligence, you can also safely validate whether the vulnerabilities enumerated in the Advisory can be exploited. This provides your Security and IT Operations teams with evidence to prioritize remediation efforts and it also increases remediation efficiency.
CyCognito continues to work diligently to help keep our customers and the industry protected by proactively identifying their attack surface gaps and giving them the information they need to get ahead of attacks and preventing breaches.
If you are interested in experiencing CyCognito Exploit Intelligence in your environment, let us know. If you’re already a CyCognito customer, the Russian state-sponsored threat Advisory discussed above is available now in your platform, simply reach out to your Customer Success manager if you’d like to discuss or understand it more.



