TLDR: Take Action Now
The recent SolarWinds supply chain attacks reinforce that if your organization isn’t proactively discovering and securing its attack surface, it needs to get started now. Attacks on the US Federal government highlight that highly distributed organizations with multiple divisions, branches, lines of business and agencies, need to map their extended IT ecosystem: Both what’s yours and what’s closely related. Attackers target the paths of least resistance; a weak link that leads back to your organization works just as well as – if not better – than a frontal attack.
No, this isn’t some New Wave blog post about psycho-babble vibes, it’s about:
- How FireEye has responded to APT29’s abuse of SolarWinds as a trojan horse
- What full disclosure looks like
- Why these events are so critically important to every organization
- What you can specifically do with the CyCognito platform to proactively move your cybersecurity posture to the left to preempt a breach.
There is no impenetrable armor.
In my 20+ years in cybersecurity, I’ve yet to see the bad guys entirely prevented from “getting in” once and for all. Eventually the odds stack up, and a breach occurs. There is no impenetrable armor. When I worked at Network Associates in 2001, it was Code Red that slammed our networks. And Symantec posted an early write up for SQL Slammer because it hit them too. The common element with security vendor breaches is typically downplaying the impact and a lack of transparency as a misplaced way to preserve stock valuation.
Fortunately it’s not every day that elite Red Team tools and tactics are exposed. Last time it was 2016 and the Shadow Brokers leaking The Equation Group’s NSA tools - leading to WannaCry attacks in May 2017 and other highly devastating attacks. The FireEye breach is different: no zero day vulnerabilities were exposed and the company was extremely transparent and rapid in their response on December 8th. Their advisory begins with a powerful sentence:
“A highly sophisticated state-sponsored adversary stole FireEye Red Team tools”
Because they knew their tools were stolen they IMMEDIATELY took responsibility and released hundreds of countermeasures (against their own stolen intellectual property) so every organization can at least detect the indicators of compromise (IOCs) -- albeit late (or to the right) in the attack lifecycle-- to mitigate further damage. Hopefully this breach will have a much lower impact than The Equation Group breach and set a good example -- if not a new standard -- of how such incidents should be handled in the future.
The bottom line is that organizations need to shift to a more proactive stance so they can preempt attackers during their reconnaissance phase, to the left of initial access in the attack lifecycle.
Professional Breach Response: A Timeline on GitHub
FireEye posted detective countermeasures against their Red Team tools on December 8th and has been updating them frequently: https://github.com/fireeye/red_team_tool_countermeasures
These countermeasures provide incredible insight into how FireEye was using only a relatively small number of highly powerful exploits to infiltrate customers' networks. While vulnerability scanners can trigger a large number of high severity issues that might distract you into security theater activity, you need to focus on what’s critical. In the present situation, special attention should be given to the products below that are targeted by the FireEye tools as they will now be specifically attractive to hackers with access to the breached trove:
- Pulse Secure SSL VPN
- Fortinet Fortigate SSL VPN
- Windows Remote Desktop services
- Atlasian Crowd and Confluence
- Citrix ADC
- Zoho’s ManageEngine
- Microsoft Exchange
Protect Your Paths of Least Resistance
Proactively searching for these products in an organization is a first step in checking their posture, including validating the latest patches are applied, checking for default credentials, proper encryption settings, misconfigurations, unintended exposure to the internet, etc. And because we KNOW these tools were stolen from FireEye by bad actors, you can safely predict they will be used against you. Therefore, organizations need to better discover these target assets now before they become the paths of least resistance the bad guys find and exploit.
Other information we can glean from the way FireEye is handling this breach comes from FireEye’s Github where you can see a real-time response to a nation-state attack by a professional cybersecurity organization. Tools and tactics are being revealed quickly and secops is paying attention as you can see from the date stamps and download activities.
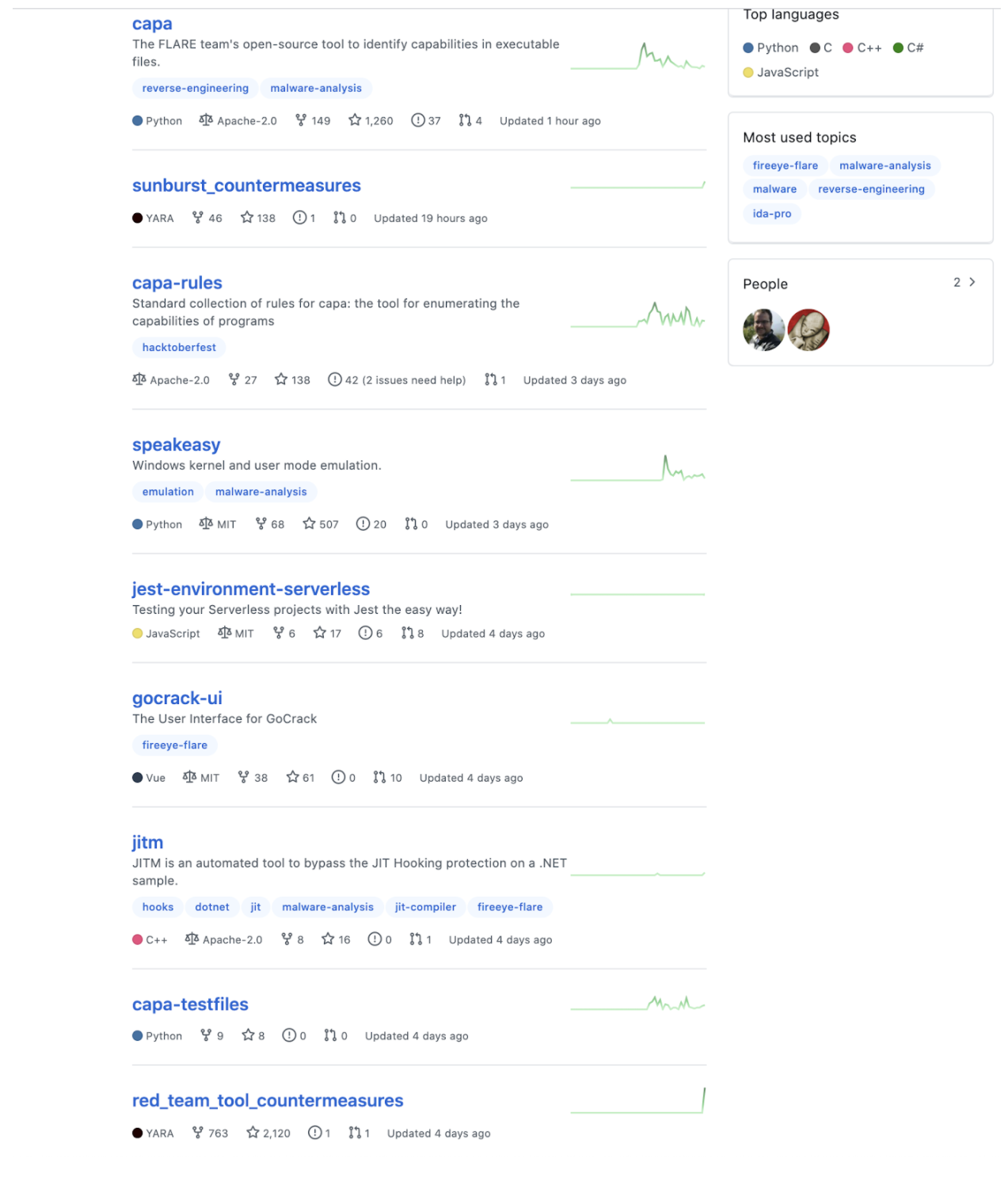
What’s clear from the details released on December 14th about the supply chain attack on SolarWinds -- that lead to the breach at National Telecommunications and Information Administration, the US Treasury, and others -- is that the SolarWinds supply chain attack is also how hackers gained access to FireEye's network and that the incident was considered so serious that it led to a rare meeting of the U.S. National Security Council at the White House, on Saturday, December 12th.& you can see from the Github screencap of the SUNBURST countermeasures FireEye released on Sunday, December 13 that they are meant to detect this attack in real time. In other words, FireEye personnel are working as fast as they can to make sure that this thing is understood and contained as much as possible. If only we had a time machine.
The “Standard Response”: Solarwinds Security Advisories
The FireEye response is exemplary and contrasts rather starkly with SolarWinds’ neutral Security Advisory released December 14, that basically enumerates that any company running SolarWinds Orion platform with their software updates from March 26, 2020 onward had better be vigilant with quite a few software packages, including cybersecurity operations tools:
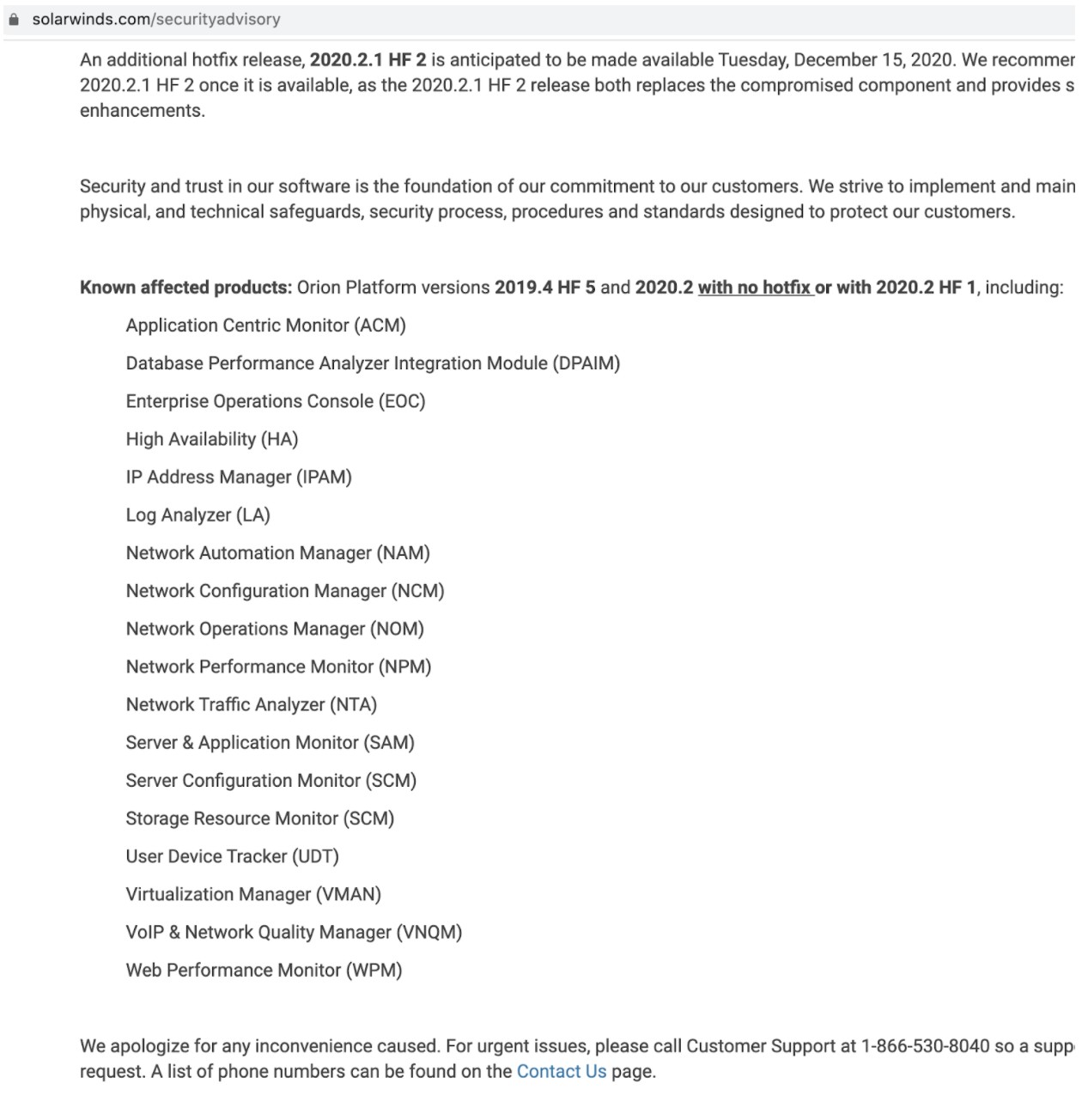
The top line of the advisory on December 14th from SolarWinds uses passive voice to downplay the severity of the incident by calling out the sophistication of the attack, the manual effort involved and the versions affected.
“SolarWinds has just been made aware our systems experienced a highly sophisticated, manual supply chain attack on SolarWinds® Orion® Platform software builds for versions 2019.4 HF 5 and 2020.2 with no hotfix</span or 2020.2 HF 1.”
Not your standard “sophisticated attacker”
This is not just your standard “sophisticated attacker” though. APT29 is a nation state actor associated with Russia intelligence agencies that has essentially weaponized the SolarWinds’ commercial software used by the U.S. government and other SolarWinds clients. They have turned commercial off the shelf software into a trojan horse with privileged network access to every device and system it’s configured to monitor and manage. Microsoft’s Security Response Center provides an excellent write-up if you’d like more details and, even as this is being written, we’re fully expecting to see more details emerge.
By December 15th at 8:00 a.m. SolarWinds provided an update with much stronger language about what they understood happened and clear indication of the steps they’ve taken to mitigate the threat and validate what software packages are, and are not impacted.

So What is the Potential Impact?
SolarWinds tools are doing network monitoring, virtualization management, voice over IP management, controlling high availability, and performing log analysis. In other words, by exploiting the Orion platform, the bad guys could own your network along with the instrumentation that might stop them or allow you to detect them. And depending on what packages you’ve installed on the Orion Platform, they may be managing your cloud environment, firewalls, routers, and switches, your IP addresses, and even DNS. For example:
1. SolarWinds VMAN can add, edit, or remove managed cloud instances in AWS and Azure. So in addition to looking for exposed SolarWinds systems, you will want to check for unexpected or absent cloud assets with your attack surface management platform. For organizations with significant digital transformation efforts in place, or those generally leveraging the cloud -- the case with the anonymized CyCognito customer in the screenshot below – this can be a significant exposure. In this case, there are 23,000 assets classified as Infrastructure as a Service (IaaS).:
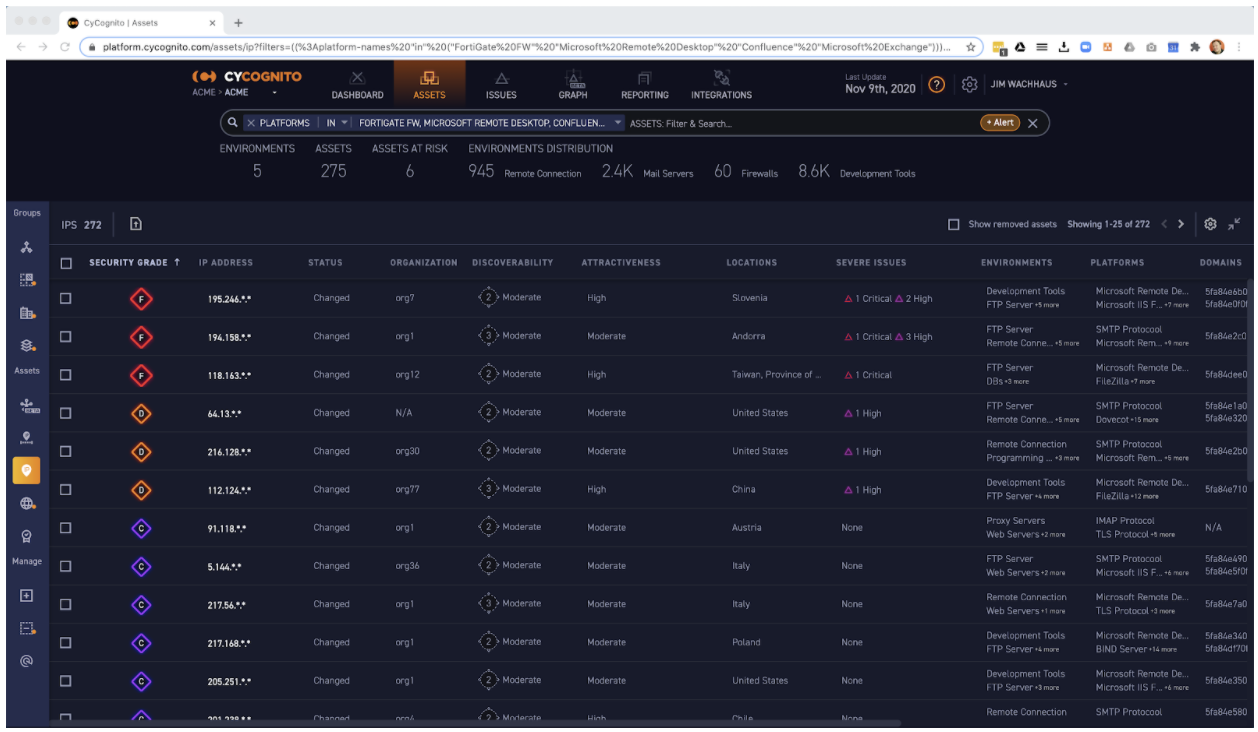
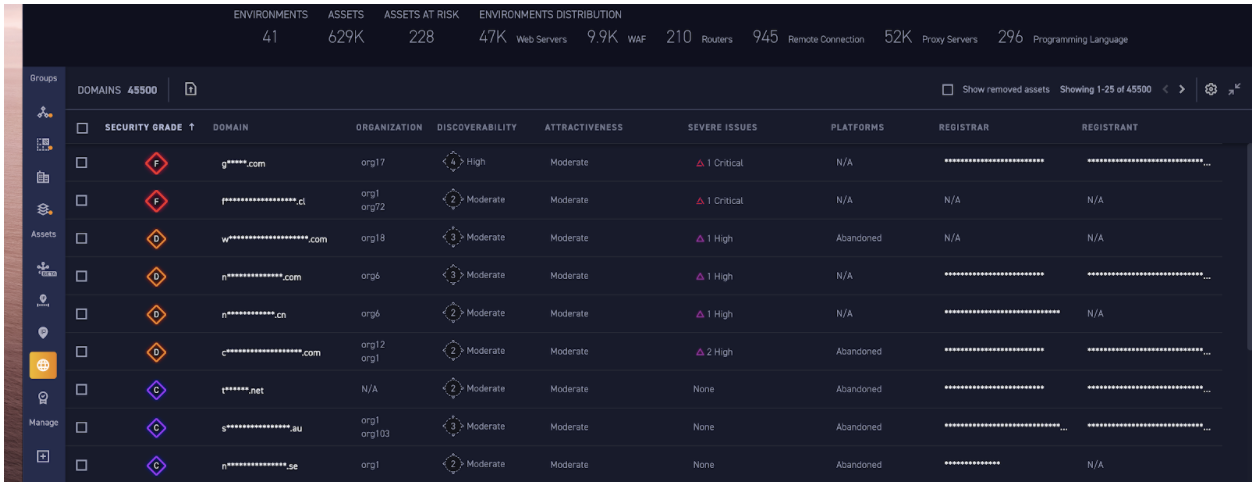
2. SolarWinds Network Configuration Manager can configure Cisco, Juniper, and Palo Alto firewalls and switches, so you’ll want to find those and double check they aren’t configured as a path of least resistance into your network. Here is a search for these platforms in the CyCognito platform as an example, classified automatically into environments. The key takeaway is that you are going to want to find and audit all of the systems like these if you were using the compromised SolarWinds platform with the back-doored updates.
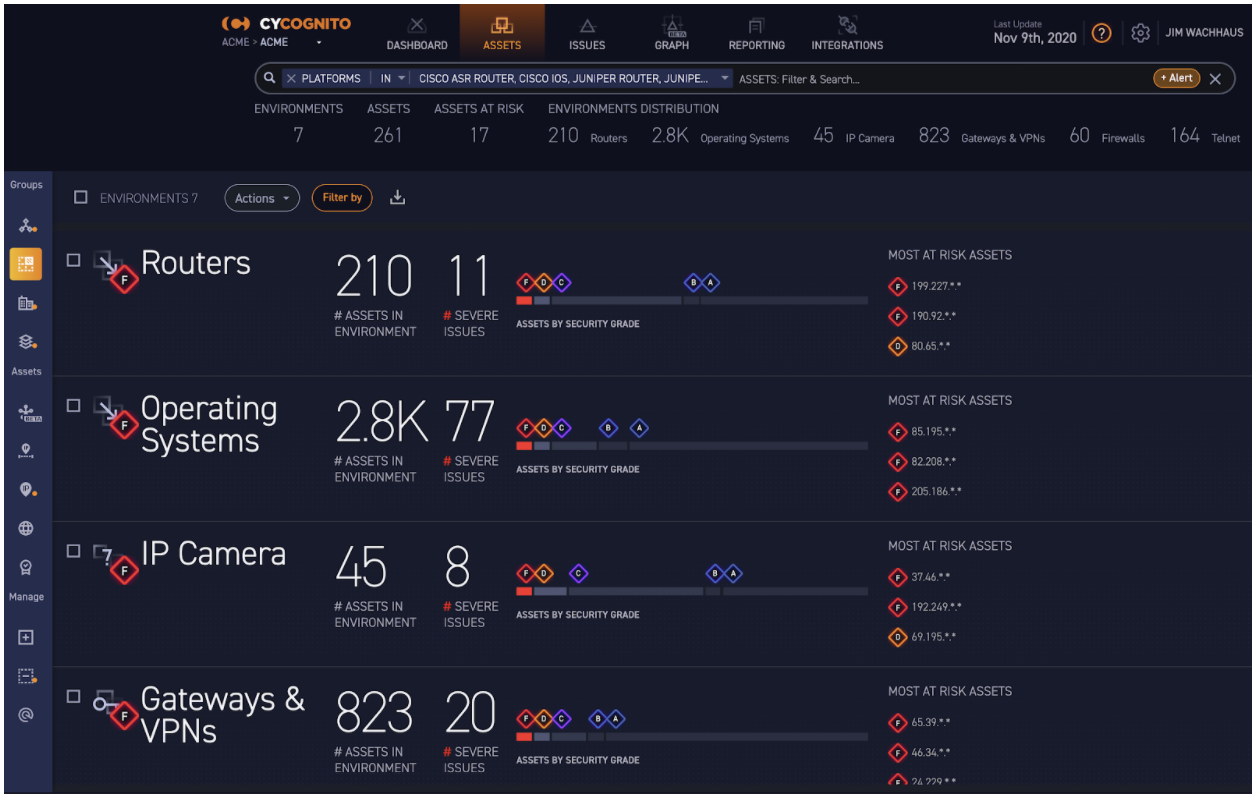
3. And with control of SolarWinds IP Address Manager, an attacker potentially has access to the managed IPs, DHCP settings, and DNS Domains managed from the compromised Orion Platform. Here is another example from the CyCognito platform. Again, you will want to investigate changes in your organization that took place since March 2020 if you were using that compromised SolarWinds package.
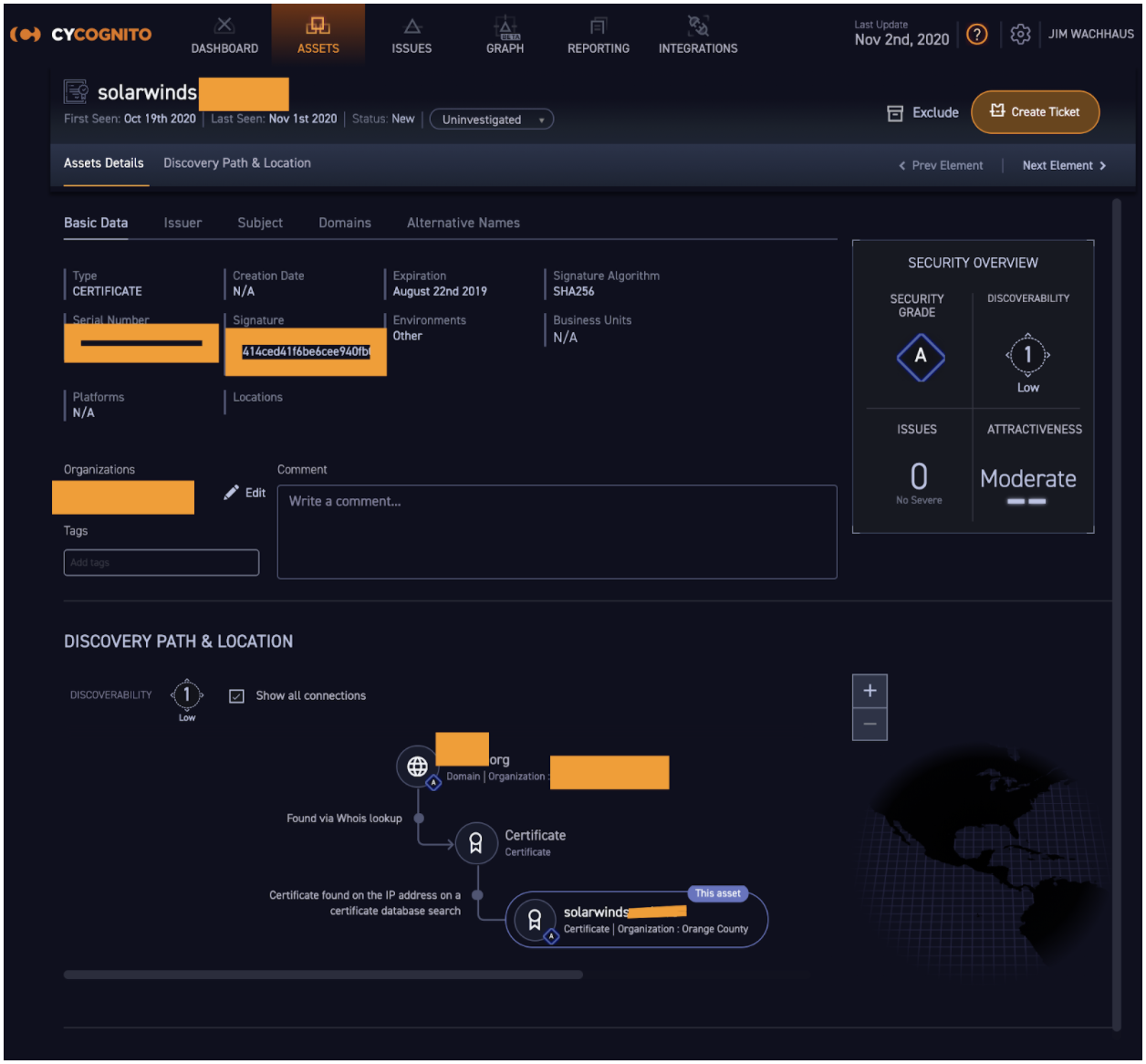
4. There is one other asset type beyond IPs and domains that may be affected. Because this backdoor can allow attackers to gain access to your organization’s global administrator account and/or trusted SAML token signing certificate, they can forge certificates or credentials. So you're going to want to investigate user accounts and certificates and make sure the spy accounts and certificates are booted. The CyCognito platform can help with finding the SolarWind certificates in your organization as shown in this anonymized example:
So, what are we to do with all this?
Hopefully your SOC has already started using the various rules and countermeasures posted by FireEye to detect IOCs associated with these tools and tactics! And if you have one, use a time machine to go back to pre-COVID-19 and before the SolarWinds compromise, but realistically, just do the monitoring. And proactively, going forward, contact whoever manages your attack surface visibility and ask them for a report on every asset running SolarWinds Orion Platform and any assets (IPs, cloud, domains, and certificates) monitored or managed by that platform! If you don’t have this kind of visibility, then you might want to look at having a conversation with CyCognito about how we can move your security posture rapidly to the left and help you see where you need to defend.



