In the world of cybersecurity, all too often it feels like “another day, another unprotected asset and another breach.” Last month’s breach of Ecuadoran data by Novaestrat1 stands out given that the breach seems to have affected almost the entire population of the country and an arrest has already been made2, but more importantly, it highlights how the introduction of IaaS+SaaS has destroyed the traditional perimeter concept upon which security has been based since the first data centers were built. A colleague and I were debating how best to configure defenses to detect a Novaestrat-esque data compromise, and we thought it worth sharing our discussion and thought process.
A Multi-Layerer Defense Strategy
I’ve been privileged to have worked with many Fortune 500 and federal government entities whose budgets were, in a practical sense, empowered to buy whatever made a positive impact on their defensive posture, so we didn’t limit defensive selection. As a generalization, I’ve seen most defenses comprised of a series of capabilities like the following:
- Network Intrusion Detection Systems (IDS) deployed throughout data centers and in Amazon Web Services (AWS) using AWS port mirroring for all workloads;
- Host-based IDS, antivirus (AV), and endpoint detection and response (EDR) on all traditional workstations and servers, and all cloud workloads;
- Data loss prevention (DLP) at the network and host layers;
- Security Information and Event Management (SIEM) solutions which gather all logs from all security defenses and apply tailored correlation rules;
- Vulnerability scanning solutions, set to continuously scan all known assets all the time; and
- Breach and attack (BAS) solutions, integrated with security defenses and SIEMs, and configured to constantly run to detect defense deficiencies.
Given the solution selection, this would pose a relatively robust environment for detecting incidents. An argument can be made about adding more tactical details like firewalls, a web application firewall, etc., but we’ll use this as a baseline and a lens for discussing a Novaestrat-specific breed of breach.
The Novaestrat Compromise
For those unfamiliar with it, the Novaestrat compromise involved an employee unintentionally exposing an (internal) Elasticsearch server in Florida to the internet, which contained millions of personally identifiable information (PII) records to the internet. Once exposed, it simply became a matter of time before someone (friendly or otherwise) would discover the host and its data.
Let’s break the result down security defense by security defense:
- Network IDS – detects nothing, as there’s no active attack inbound to, or outbound from, the server. Note the emphasis on the need for an attack to trigger a defensive response, as it is a key aspect throughout the defensive analysis.
- Host IDS, AV, and EDR – assuming the server is properly managed (unlikely based on at least one misconfiguration and its accidental exposure to the internet) and has all the requisite agents on it, they’ll report nothing, as there are no active attacks associated with the host.
- DLP – might detect something after someone on the internet accesses the data, and that’s assuming the DLP agent or network tool is covering the unmanaged asset; in any case, it doesn’t necessarily prevent the legal entanglement unless the DLP:
- detects the data exfil,
- sits inline, and
- has prevention/blocking enabled, which most organizations fear to do due to disruption of the business.
- SIEM – might detect something after someone on the internet accesses the data based on logged events from one of the defenses or the host, which again doesn’t save the data from compromise.
- Vulnerability Scanner – detects nothing, as this wasn’t the result of a vulnerability, and likely wouldn’t be scanning the host anyway because it only scans known assets.
- BAS – interestingly, BAS does nothing here as well, as it’s designed to test network defenses (see #1 and #3 just above), and it’s limited to testing the host-based defenses of a single image, not the full attack surface or assets of an organization (see #2 above regardless).
In sum, because the Elasticsearch server didn’t have a vulnerability that exposed the data, didn’t have an active attack associated with it, and couldn’t have been validated by a BAS solution, the only chance an organization like Novaestrat has of catching a data breach like this is after an adversary on the internet sees the data.
Traditional Defenses and Detection Methods are Certain to Fail
Despite unlimited funding, traditional defenses and detection methods are still almost certain to fail.
The term we’re using at CyCognito to describe risks like those posed by the rogue Novaestrat server is “shadow risk.” Shadow risk arises from the 21st century IT ecosystem that involves partners and subsidiaries who have your data, assets you own that are exposed to the internet (from workloads in the cloud to data-center servers to routers in offices), and IaaS and SaaS providers you use in the course of business. The level of technical control varies in each case, and critically, the level of visibility you have varies, creating types of risk that are new.
Going back in time with the knowledge that traditional tools couldn’t protect against this high-profile breach, what could an organization like Novaestrat have done to combat their shadow risk problem
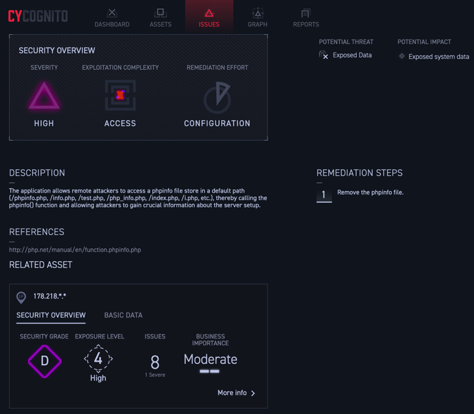
The CyCognito platform is able to identify data exposures (as shown above) so that organizations can take action before a breach occurs.
To find attacker-exposed assets like the Elasticsearch server, organizations would need something that continuously scans the entire internet looking for misconfigured assets, exposed data, default configurations and credentials, and systems with vulnerabilities and other risks. That solution would then need to take that data it discovered from all areas of the modern IT ecosystem (traditional data centers, partners, subsidiaries, IaaS, SaaS, etc.), and accurately determine what belonged to their organization. This would be a new approach that matches the new reality of distributed IT ecosystems—and one that CyCognito is creating for its customers today.
[1] https://www.cnbc.com/2019/09/17/ecuador-data-breach-leaks-personal-information-for-millions-of-citizens.html
[2] https://www.zdnet.com/article/arrest-made-in-ecuadors-massive-data-breach/


